72
VM-Series
Deployment
Guide
Create Policies
Set Up a VM-Series NSX Edition Firewall
Define Policies on the NSX Manager
In order for the VM-Series firewall to secure the traffic, you must complete the following tasks:
Set Up Security Groups on the NSX Manager
Define Policies to Redirect Traffic to the VM-Series Firewall
Apply the Redirection Policies on the NSX Manager
.
Set Up Security Groups on the NSX Manager
A security group is a logical container that assembles guests across multiple ESXi hosts in the cluster. Creating
security groups makes it easier to manage and secure the guests; to understand how security groups enable
policy enforcement, see
Policy Enforcement using Dynamic Address Groups
.
Before you apply the redirection policy, make sure to create policies on Panorama
and push them to the VM-Series firewall, see
Apply Policies to the VM-Series
Firewall
.
The default policy on the VM-Series firewall is set to
deny all
traffic, which means
that all traffic redirected to the VM-Series firewall will be dropped.
Set up Security Groups on the NSX Manager
Step 1
Select
Networking and Security > Service Composer > Security Groups
, and add a
New Security Group
.
Step 2
Add a
Name
and
Description
. This name will display in the match criteria list when defining Dynamic Address
Groups on Panorama.
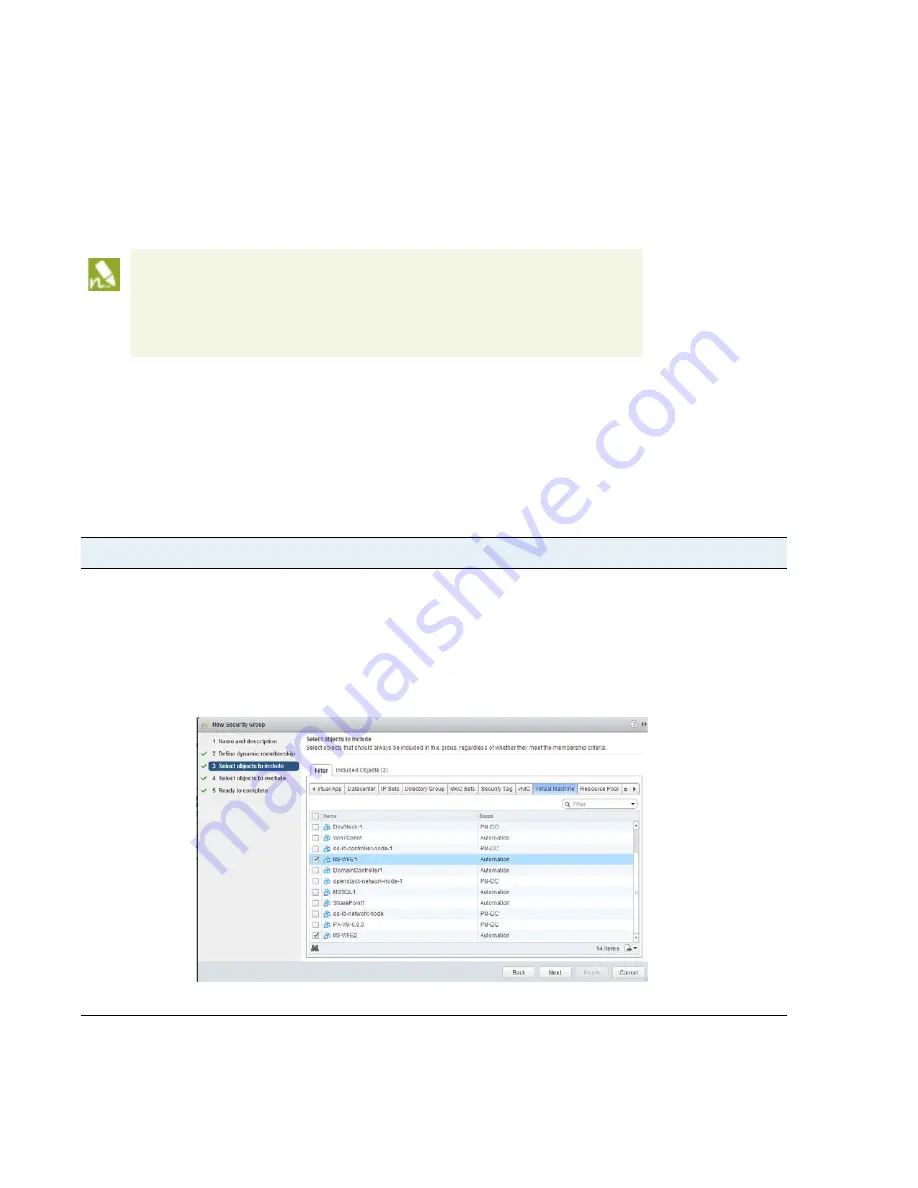
Step 3
Select the guests that constitute the security group. You can either add members dynamically using
Define
Dynamic Membership
or statically using
Select the Objects to Include
. In the following screenshot, the guests
that belong to the security group are selected using the
Select objects to include
>
Virtual Machine
option.
Step 4
Review the details and click
OK
to create the security group.























