Reference Manual for the ProSafe VPN Firewall FVS114
6-18
Advanced Virtual Private Networking
202-10098-01, April 2005
c.
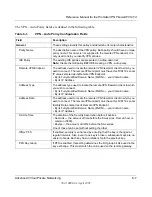
From the main menu Advanced section, click the
LAN IP Setup
link. The following
menu appears
Figure 6-8: LAN IP Setup menu
d.
Configure the LAN IP address according to the settings above and click
Apply
to save
your settings. For more information on LAN TCP/IP setup topics, please see
“Configuring
LAN TCP/IP Setup Parameters” on page 8-5
.
Note:
After you click
Apply
to change the LAN IP address settings, your workstation will
be disconnected from the FVS114. You will have to log on with
http://10.5.6.1
which is
now the address you use to connect to the built-in Web-based configuration manager of
the FVS114.
Содержание FVS114NA
Страница 4: ...202 10098 01 April 2005 iv...
Страница 12: ...202 10098 01 April 2005 xii Contents...
Страница 16: ...Reference Manual for the ProSafe VPN Firewall FVS114 1 4 About This Manual 202 10098 01 April 2005...
Страница 116: ...Reference Manual for the ProSafe VPN Firewall FVS114 6 28 Advanced Virtual Private Networking 202 10098 01 April 2005...
Страница 148: ...Reference Manual for the ProSafe VPN Firewall FVS114 9 8 Troubleshooting 202 10098 01 April 2005...
Страница 166: ...Reference Manual for the ProSafe VPN Firewall FVS114 B 16 Network Routing and Firewall Basics 202 10098 01 April 2005...
Страница 200: ...Reference Manual for the ProSafe VPN Firewall FVS114 D 22 Preparing Your Network 202 10098 01 April 2005...
Страница 211: ...Reference Manual for the ProSafe VPN Firewall FVS114 Glossary 11 202 10098 01 April 2005...
Страница 212: ...Reference Manual for the ProSafe VPN Firewall FVS114 12 Glossary 202 10098 01 April 2005...