Chapter 4
Advanced Configuration
58
10/100 8-Port VPN Router
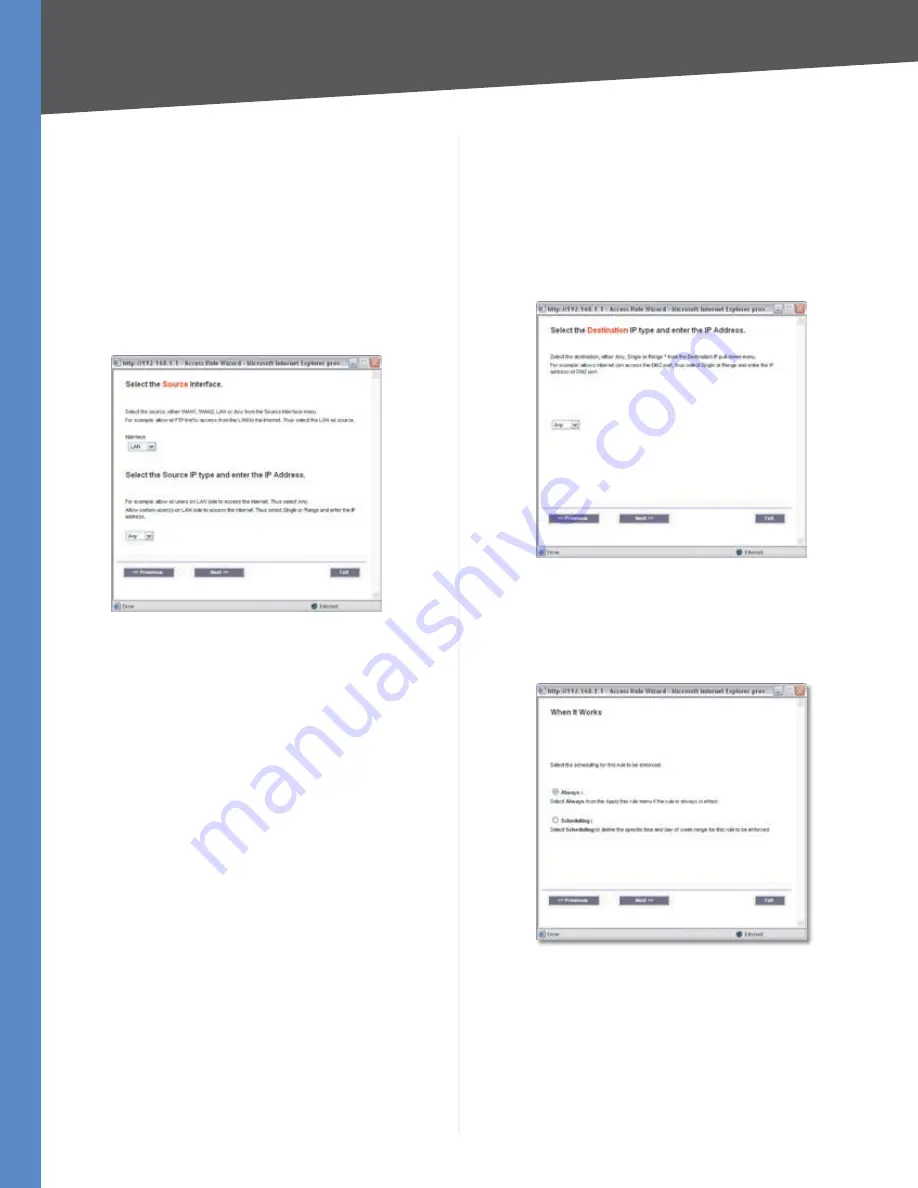
Select the Source Interface:
5.
LAN
,
WAN1
,
WAN2
, or
Any
from the
Interface
pull-down menu.
Select the Source IP address(es) for this Access Rule. If it
can be any IP address, select
Any
. If it is one IP address,
select
Single
and enter the IP address. If it is a range
of IP addresses, select
Range
, and enter the range of
IP addresses.
Click
Next
to continue. Click
Previous
if you want to
return to the previous screen. Click
Exit
if you want to
exit the Setup Wizard.
Select the Source
Select the Destination IP address(es) for this Access
6.
Rule. If it can be any IP address, select
Any
. If it is one
IP address, select
Single
and enter the IP address. If it
is a range of IP addresses, select
Range
, and enter the
range of IP addresses.
Click
Next
to continue. Click
Previous
if you want to
return to the previous screen. Click
Exit
if you want to
exit the Setup Wizard.
Select the Destination
Decide when you want this Access Rule to be enforced.
7.
Select
Always
if you want the Access Rule to be always
enforced, or select
Scheduling
if you want to specify
when the Access Rule should be in effect.
When It Works
If you selected Always, click
Next
to continue. Click
Previous
if you want to return to the previous
screen. Click
Exit
if you want to exit the Setup Wizard.
If you selected Scheduling, click
Next
to continue. A
new screen appears. Decide what times and which
days of the week the Access Rule should be enforced.
Then enter the hours and minutes in 24-hour format,






























