210
01-28006-0068-20041105
Fortinet Inc.
Configuring service groups
Firewall
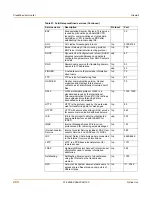
Service group has the following options.
Configuring service groups
To organize services into a service group
1
Go to
Firewall > Service > Group
.
2
Select Create New.
3
Enter a group name to identify the service group.
4
Select a service from the Available Services list and select the right arrow to move the
service into the group.
5
Select OK.
To delete a service group
If a service group is included in a policy, it cannot be deleted unless it is first removed
from the policy.
1
Go to
Firewall > Service > Group
.
2
Select the Delete icon beside the service group you want to delete.
3
Select OK.
To edit a service group
1
Go to
Firewall > Service > Group
.
2
Select the Edit icon beside the service group you want to modify.
3
Make any required changes.
4
Select OK.
Schedule
Use schedules to control when policies are active or inactive. You can create one-time
schedules and recurring schedules.
You can use one-time schedules to create policies that are effective once for the
period of time specified in the schedule. Recurring schedules repeat weekly. You can
use recurring schedules to create policies that are effective only at specified times of
the day or on specified days of the week.
Group Name
Enter a name to identify the address group.
Available
Services
The list of configured and predefined services. Use the arrows to move
services between the lists.
Members
The list of services in the group. Use the arrows to move services between
the lists.
Note:
To change the service group name you must delete the service group and add it with a
new name.
Содержание FortiGate FortiGate-100A
Страница 24: ...24 01 28006 0068 20041105 Fortinet Inc FortiLog documentation Introduction...
Страница 46: ...46 01 28006 0068 20041105 Fortinet Inc Installing and using a backup firmware image System status...
Страница 72: ...72 01 28006 0068 20041105 Fortinet Inc Transparent mode VLAN settings System network...
Страница 80: ...80 01 28006 0068 20041105 Fortinet Inc DHCP IP MAC binding settings System DHCP...
Страница 114: ...114 01 28006 0068 20041105 Fortinet Inc Access profile options System administration...
Страница 232: ...232 01 28006 0068 20041105 Fortinet Inc CLI configuration Firewall...
Страница 244: ...244 01 28006 0068 20041105 Fortinet Inc peergrp Users and authentication...
Страница 320: ...320 01 28006 0068 20041105 Fortinet Inc service smtp Antivirus...
Страница 366: ...366 01 28006 0068 20041105 Fortinet Inc syslogd setting Log Report...
Страница 380: ...380 01 28006 0068 20041105 Fortinet Inc Glossary...
Страница 388: ...388 01 28006 0068 20041105 Fortinet Inc Index...