When to use this type
What is scanned
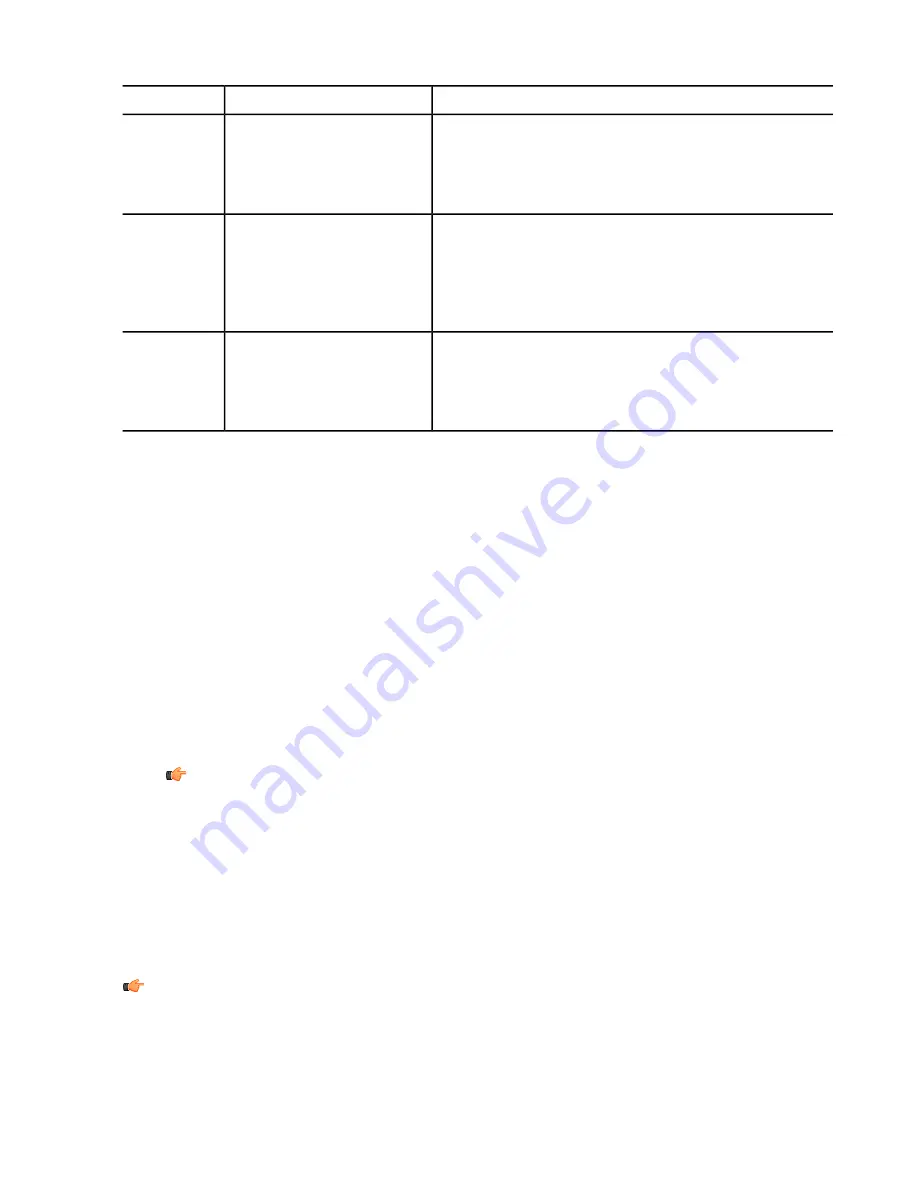
Scan type
files, such as documents, music, images, and videos. This
type of scan is slow and recommended only if the Virus and
spyware scan has not found any malware and if you want to
be sure that the other parts of your computer do not contain
malicious files.
This type of scan is much quicker than a full scan. It searches
only the parts of your system that contain installed program
Parts of your computer for
viruses, spyware and riskware
Virus and
spyware scan
files.This scan type is recommended if you want to quickly
check whether your computer is clean, because it is able to
efficiently find and remove any active malware on your
computer.
When you suspect that a rootkit may be installed on your
computer. For example, if malware was recently detected in
Important system locations
where a suspicious item may
Rootkit scan
your computer and you want to make sure that it did not
install a rootkit.
mean a security problem.
Scans for hidden files, folders,
drives or processes
Clean malware automatically
If
malware
is found during the scan, you can either let the program automatically decide how to clean your
computer or you can decide yourself for each item.
1.
Select either of:
What will happen
Option
The program decides what to do to each
malware
item to
automatically clean your computer.
Handle automatically (recommended)
The program asks what you want to do to each
malware
item.
I want to decide item by item
2.
Click
Next
.
•
If you selected
Handle automatically (recommended)
, a window with the results of automatic malware
handling opens.
Note:
Some malware items may have a "Not processed" status, which means that the infected
file is inside an archive (for example, a zip file) and cannot be handled automatically. You can
delete the infected file by opening the archive and deleting the file manually. If the content of the
archive is not important, you can delete the whole archive.
•
If you selected
I want to decide item by item
, you must specify action for each detected malware.
3.
Click
Finish
to close the Scan Wizard.
View the results of manual scan
You can view a report of the scanning results after the scan is complete.
Note:
You might want to view this report because the action you selected may not always be the action
that was performed. For example, if you chose to clean an infected file, but the
virus
could not be
removed from the file, the product may have performed some other action to the file.
To view the report:
1.
Go to
Server Protection
➤
Manual Scanning
and open the Status tab.
F-Secure Anti-Virus for Windows Servers | Protecting the server against malware |
29
Содержание Anti-Virus for Windows Servers
Страница 1: ...F Secure Anti Virus for Windows Servers Administrator s Guide...
Страница 2: ......
Страница 14: ......
Страница 38: ......
Страница 44: ......
















































