Managing Ethernet Services
Ridgeline Concepts and Solutions Guide
98
4
When you are done, click
Add
(for a new bandwidth profile) or
Modify
(for an existing bandwidth
profile).
5
After you create a bandwidth profile, you can apply it to the UNI ports in Ethernet services. See
“Modifying an Ethernet Service” on page 94
.
Viewing Ethernet Services Information
You can display information about E-Line and E-LAN services from the
All map
or
All table
, or from the
Services
view under Network Views.
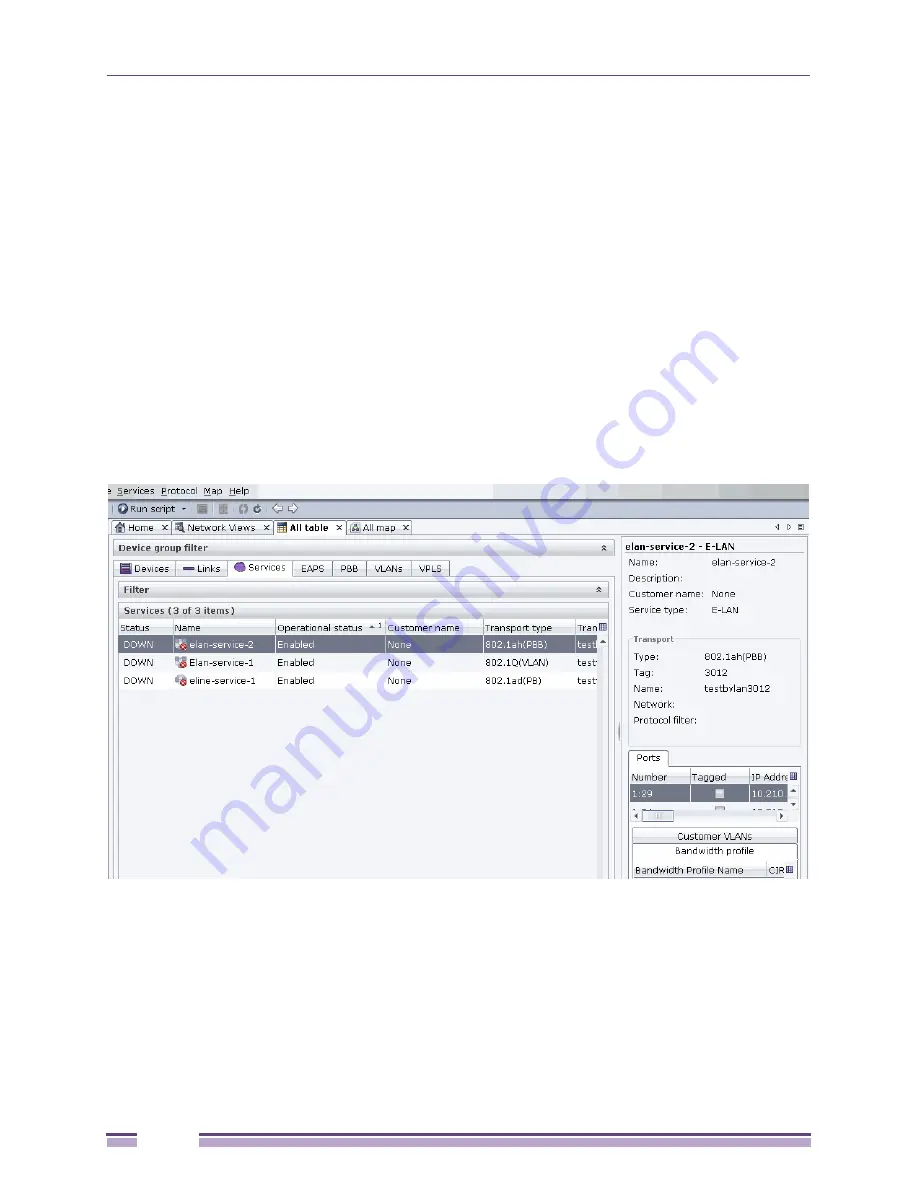
Using the All Table and All Map View
To view information about the E-Line and E-LAN services known to Ridgeline, click a device group or
the
All map
or
All table
group under the Network Views folder, then click the Services tab. A table listing
the E-Line and E-LAN services in the group is displayed, as shown in
Figure 60
.
Figure 60: Services Table in Network Views
If you also have enabled the map view of a device group, you can select a row in the table and display
an overlay view highlighting all of the devices and UNI ports in the map where the selected E-Line or
E-LAN service is configured, as shown in
Figure 60
.
Содержание Ridgeline 3.0
Страница 14: ...Related Publications Ridgeline Concepts and Solutions Guide 12 ...
Страница 26: ...Ridgeline Overview Ridgeline Concepts and Solutions Guide 24 ...
Страница 52: ...Getting Started with Ridgeline Ridgeline Concepts and Solutions Guide 50 ...
Страница 78: ...Using Map Views Ridgeline Concepts and Solutions Guide 76 ...
Страница 88: ...Provisioning Network Resources Ridgeline Concepts and Solutions Guide 86 ...
Страница 103: ...6 Ridgeline Concepts and Solutions Guide 101 Figure 63 E Line Service Details Window ...
Страница 104: ...Managing Ethernet Services Ridgeline Concepts and Solutions Guide 102 ...
Страница 113: ...7 Ridgeline Concepts and Solutions Guide 111 Figure 72 Importing E Line Service Dialog with Validation Errors ...
Страница 114: ...Importing Services Ridgeline Concepts and Solutions Guide 112 ...
Страница 132: ...Managing and Monitoring VPLS Domains Ridgeline Concepts and Solutions Guide 130 ...
Страница 146: ...Managing VLANs Ridgeline Concepts and Solutions Guide 144 ...
Страница 190: ...Managing Your EAPS Configuration Ridgeline Concepts and Solutions Guide 188 ...
Страница 202: ...Managing Network Security Ridgeline Concepts and Solutions Guide 200 ...
Страница 350: ...Book Title Ridgeline Concepts and Solutions Guide 348 ...
Страница 372: ...Book Title Ridgeline Concepts and Solutions Guide 370 ...