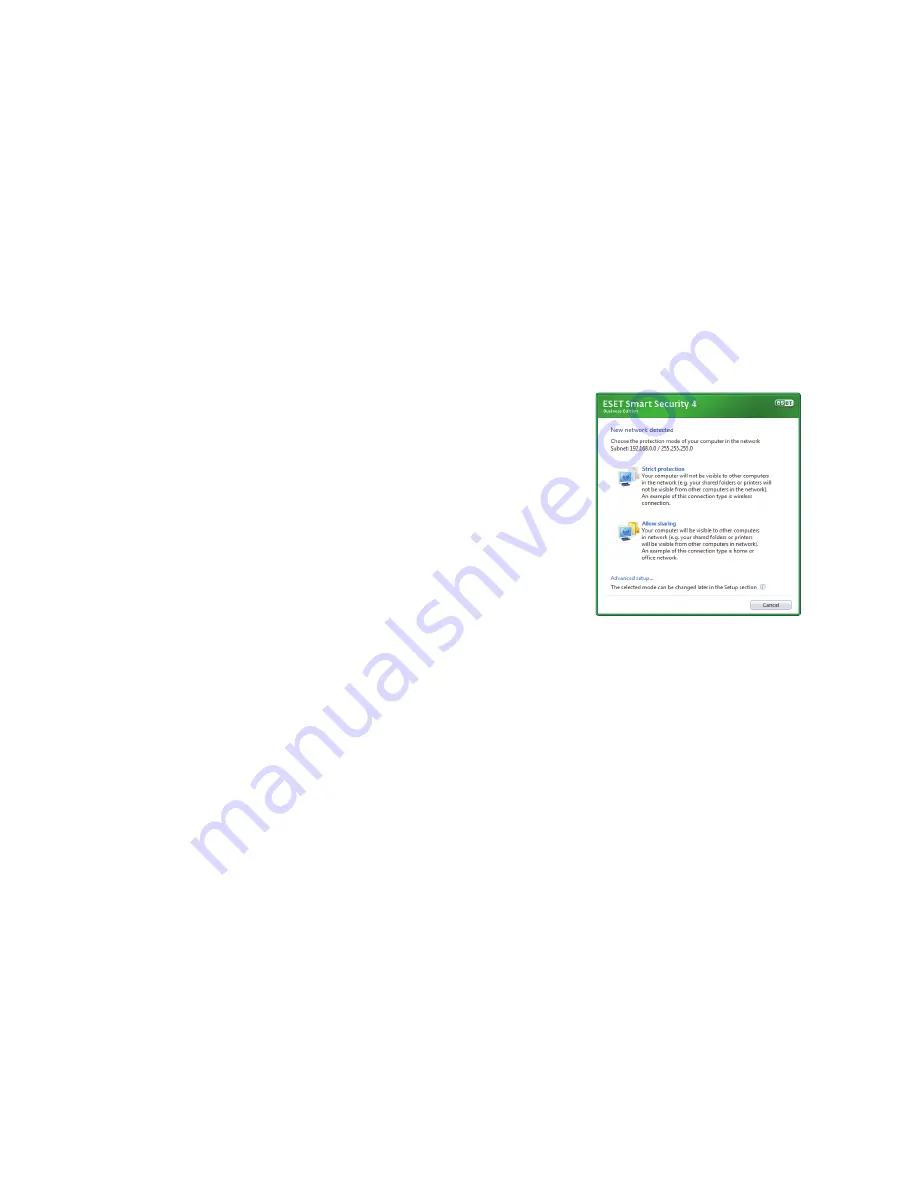
Trusted zone setup
After the installation has completed
and a network connection is detected,
a prompt window allowing you to
configure a trusted zone will appear.
The window shows the local subnet
defined in your computer’s system
setup. These options only affect the
visibility of your computer in the local
network, not the internet. There are
two access modes available:
Strict protection
– select this option
if you do not want to share files and
folders on your computer and want
your computer to be invisible to other
users on the same network. This
setting is recommended for users with
a wireless connection.
Allow sharing
– select this option if
you want to be able to share files and
folders on your computer and want
your computer to be visible to other
users on the same network. This
setting is recommended for local home
or office trusted networks.
Содержание NOD32 ANTIVIRUS 4 - FOR MICROSOFT WINDOWS 7-VISTA-XP-2000-2003-2008
Страница 1: ...Quick Start Guide Microsoft Windows 7 Vista XP 2000 2003 2008...
Страница 5: ......
Страница 15: ...A technical support representative will contact you as soon as possible...


































