DGS-1250 Series Gigabit Ethernet Smart Managed Switch Web UI Reference Guide
232
Statistics
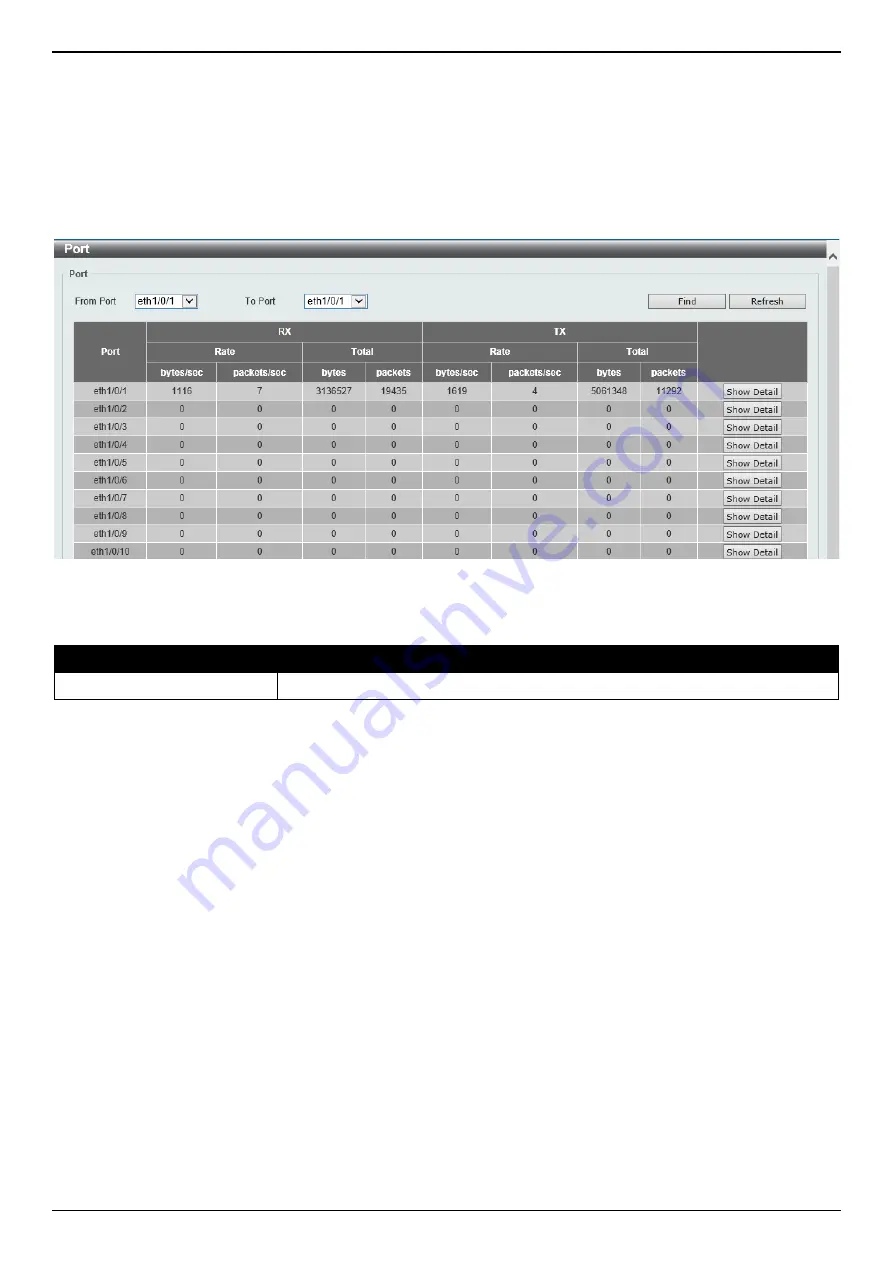
Port
This window is used to view the port statistics information.
To view the following window, click
Monitoring > Statistics > Port
, as shown below:
Figure 11-2 Port Window
The fields that can be configured are described below:
Parameter
Description
From Port - To Port
Select the range of ports that will be used in this display here.
Click the
Find
button to display entries in the table based on the information selected.
Click the
Refresh
button to refresh the information displayed in the table.
Click the
Show Detail
button to view more detailed statistics information on the specified port.
Содержание DGS-1250 Series
Страница 1: ......






























