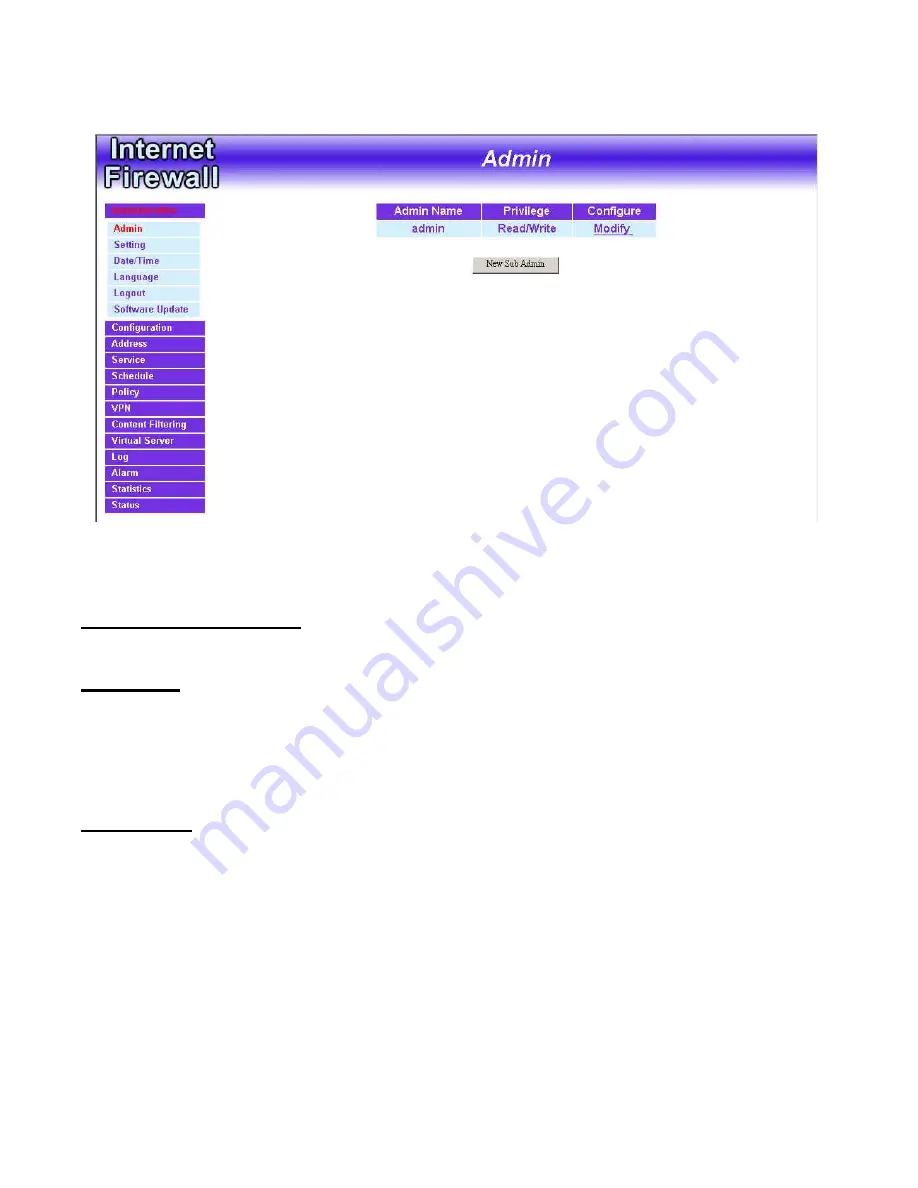
Firewall Administration setup
On the left hand menu, click on
Administration
, and then select
Administrator
below it. The current list of Administrator(s) shows up.
Settings of the Administration table:
Administrator Name:
The username of Administrators for the firewall. The
user
admin
cannot be removed.
Privilege:
The privileges of Administrators (Admin or Sub Admin)
The username of the main Administrator is
Administrator
with
read/write
privilege.
Sub Admins may be created by the
Admin
by clicking
New Sub Admin.
Sub Admins have
read only
privilege.
Configure:
Click
Modify
to change the “Sub Administrator’s” password and
click
Remove
to delete a “Sub Administrator.”
- 6 -
Содержание DFL-300 - Security Appliance
Страница 1: ... 1 FIREWALL VPN ROUTER User s Manual Doc No 120602 01 ...
Страница 45: ... 45 ...
Страница 123: ...Step 3 Click OK to save modifications or click Cancel to cancel modifications 123 ...
Страница 144: ...When Disable appears in the drop down list no Virtual Server can be added 144 ...
Страница 172: ...Step 4 When the following screen appears the setup is completed 172 ...
Страница 174: ...Step 8 When the following screen appears the setup is completed 174 ...
Страница 177: ...Step 9 An Incoming FTP policy should now be created 177 ...
Страница 179: ...Step 8 Open all the services ANY Step 9 The setup is completed 179 ...






































