5-11
Cisco Secure Desktop Configuration Guide
OL-8607-02
Chapter 5 Setting Up CSD for Microsoft Windows Clients
Defining Location Criteria
String value
field—Enter a string to compare with the String value of the registry key on the client
computer.
EXAMPLE Choose
matches
and enter Active if you want to ensure the following protective
software application is active:
HKEY_LOCAL_MACHINE\SOFTWARE\
<Protective_Software>
\Status
Case sensitive—
Check to require the String value of the registry key on the client computer to
match the case used in the String value field to satisfy the criterion.
Step 3
Click
OK
.
The dialog box closes and the new criterion appears as an entry in the Registry Criteria window inside
the Registry and File Criteria dialog box.
Step 4
Click
Add
if you want to specify another registry key, refer to the next section if you want to specify a
file criterion, or click
OK
to return to the Identification for
<Location>
pane.
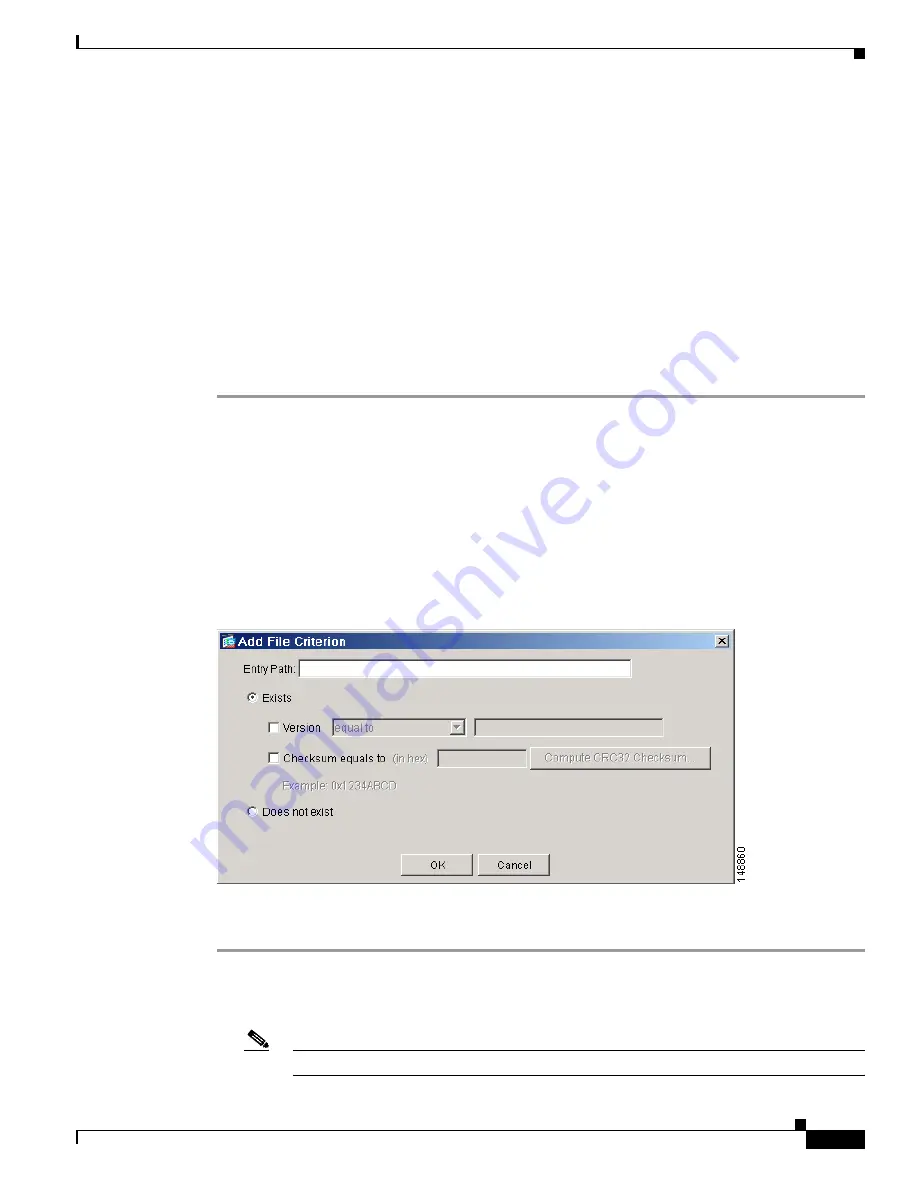
File Criteria
In the File Criteria area of the Registry and File Criteria dialog box (
Figure 5-3
), click
Add
if you want
to confirm the presence or absence of a specific file as a criterion for assigning the location you are
configuring for the remote client, or choose a criterion to be modified from the File Criteria area and
click
Edit
.
The Add or Edit File Criterion dialog box opens.
Figure 5-5
shows the Add File Criterion dialog box.
Figure 5-5
Add File Criterion
Configure a file criterion as follows:
Step 1
Assign a value to the following mandatory attribute:
•
Entry Path
—Enter the directory path of the file required to be present on or absent from the client
system.
Note
Refer to the subsequent attribute descriptions for examples File paths.






























