Administering the WMIC
Protecting Access to Privileged EXEC Commands
8
Cisco 3200 Series Wireless MIC Software Configuration Guide
To configure encryption for enable and enable secret passwords
, follow these steps, beginning in
privileged EXEC mode:
If both the enable and enable secret passwords are defined, users must enter the enable secret password.
Use the
level
keyword to define a password for a specific privilege level. After you specify the level and
set a password, give the password only to users who need to have access at this level. To specify
commands accessible at various levels, use the
privilege level
command in global configuration mode.
For more information, see the
“Configuring Multiple Privilege Levels” section on page 10
.
If you enable password encryption, it applies to all passwords, including username passwords,
authentication key passwords, the privileged command password, and console and virtual terminal line
passwords.
To remove a password and level, use the
no enable password
[
level
level
] or
no enable secret
[
level
level
] command in global configuration mode. To disable password encryption, use the
no service
password-encryption
command in global configuration mode.
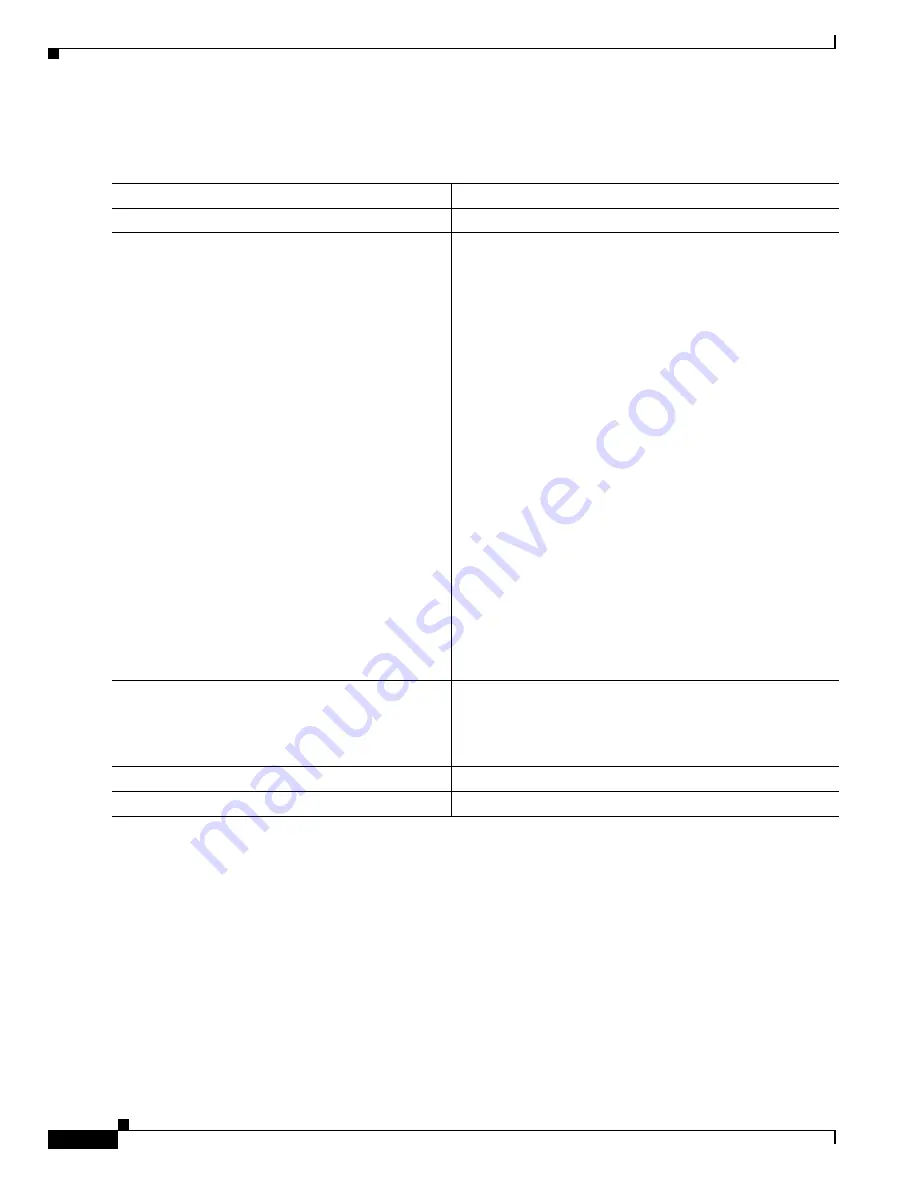
Command
Purpose
Step 1
configure terminal
Enters global configuration mode.
Step 2
enable password
[
level
level
] {
password
|
encryption-type encrypted-password
}
or
enable secret
[
level
level
] {
password
|
encryption-type encrypted-password
}
Defines a new password or change an existing password for
access to privileged EXEC mode.
or
Defines a secret password, which is saved using a
nonreversible encryption method.
•
(Optional) For
level
, the range is from 0 to 15. Level 1 is
normal user EXEC mode privileges. The default level is
15 (privileged EXEC mode privileges).
•
For
password
, specify a string from 1 to 25
alphanumeric characters. The string cannot start with a
number, it is case sensitive, and it allows spaces but
ignores leading spaces. By default, no password is
defined.
•
(Optional) For
encryption-type
, only type 5, a Cisco
proprietary encryption algorithm, is available. If you
specify an encryption type, you must provide an
encrypted password—an encrypted password that you
copy from another WMIC configuration.
Note
If you specify an encryption type and then enter a
clear text password, you can not reenter privileged
EXEC mode. You cannot recover a lost encrypted
password by any method.
Step 3
service password-encryption
(Optional) Encrypt the password when the password is
defined or when the configuration is written.
Encryption prevents the password from being readable in the
configuration file.
Step 4
end
Returns to privileged EXEC mode.
Step 5
copy running-config startup-config
(Optional) Saves your entries in the configuration file.
Содержание 3200 Series
Страница 14: ...xiv Cisco 3200 Series Wireless MIC Software Configuration Guide OL 6415 04 ...
Страница 120: ...Administering the WMIC Managing the System Time and Date 56 Cisco 3200 Series Wireless MIC Software Configuration Guide ...
Страница 136: ...Dynamic Frequency Selection Additional Information 6 Radio Channels and Transmit Frequencies OL 11491 03 ...
Страница 254: ...WIMIC Troubleshooting Error and Event Messages 12 Cisco 3200 Series Wireless MIC Software Configuration Guide ...
Страница 272: ...Supported MIBs Using FTP to Access the MIB Files 4 Cisco 3200 Series Wireless MIC Software Configuration Guide ...
Страница 314: ...Index IN 12 Cisco 3200 Series Wireless MIC Software Configuration Guide OL 6415 04 ...






























