Avaya G250 and G250-BRI Branch Office Media Gateways w/FIPS Non-Proprietary Security Policy
Version 1.2 Wednesday, 14 December, 2005
© 2005 Avaya Inc.
May be reproduced only in its original entirety [without revision]. Page 18 of 23
CID 106595
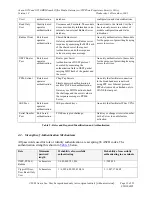
Key
Ena
b
le FIPS mo
de
Firmware Update
CSPs management
User Management
Module configuration
Reset
Read all st
at
us indicat
ions
Module backup
Restore
Zeroization
IK
E negot
iat
ion
IPSec tra
ffic pro
cessing
Read subset
of
st
at
us
indications
OSPF ro
uting
PPPo
E Serv
ice
Ra
dius Authentica
tio
n
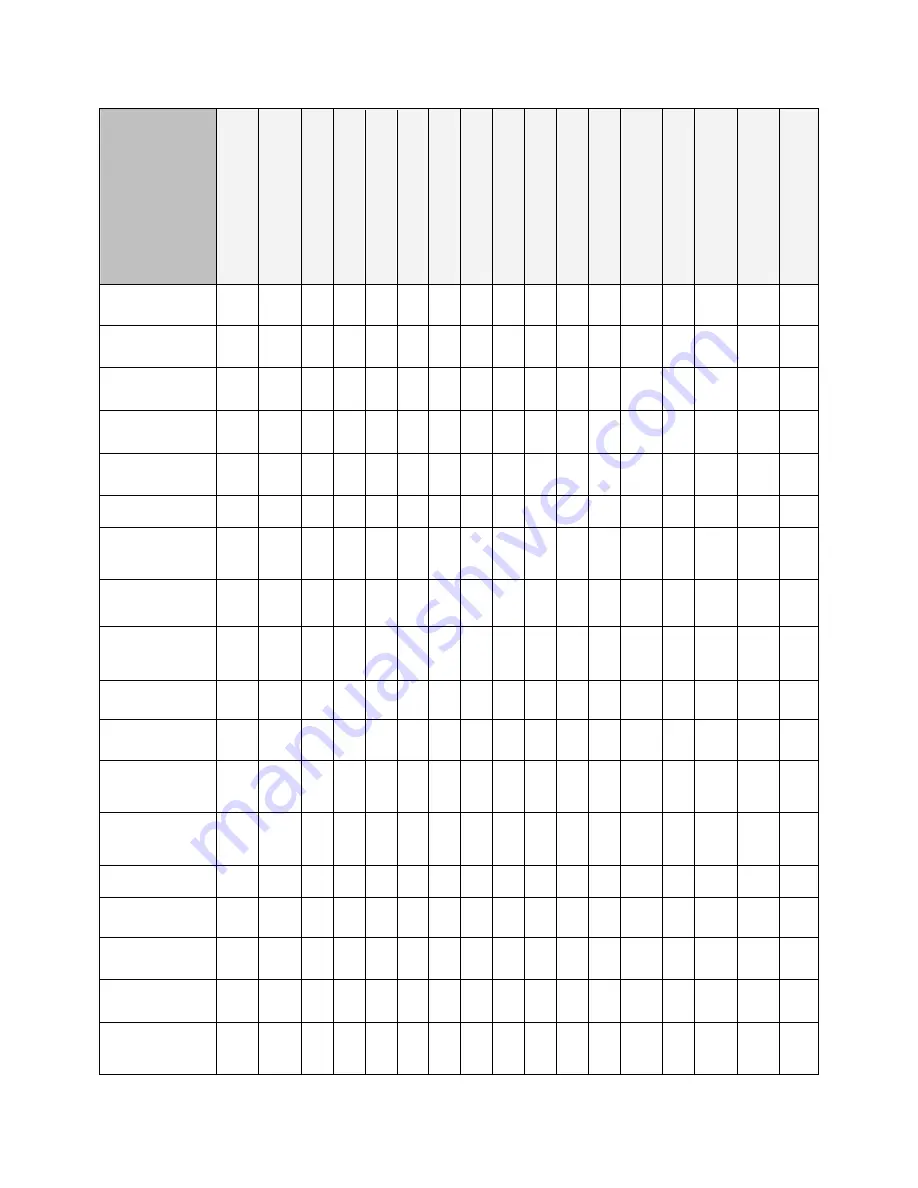
Serial Number Exchange
PRNG keys
RWZ
ZW
Z
R
IKE Pre-shared Keys
RWZ W Z Z R
Pre-shared Session Key
(SKEYID)
Z Z
RW
Ephemeral DH private
key
Z Z
RW
Ephemeral DH shared
secret
Z Z
RW
HASH_I, HASH_R
Z Z
RW
IKE session Phase 1
Secret (SKEYID_d)
Z Z
RW
IKE Phase 1 HMAC
Key (SKEYID_a)
Z Z
RW
IKE Session Phase 1
SKEYID_e
Z Z
RW
IKE Session Phase 1
TDES
Z Z
RW
IKE Session Phase 1
DES
Z Z
RW
IKE Session Phase 1
AES
Z Z
RW
IKE Phase 1 TDES key
(SKEYID_e)
Z Z
RW
Nonce
Z Z
W
R
IPSEC SA Phase-2
TDES key
Z Z
W
R
IPSEC SA Phased-2
AES key
WZ Z Z
W
R
IPSEC SA Phased-2
HMAC keys
Z Z
W
R
IPSEC SA Phased-2
keys per protocol
Z Z
RW