WebConsole - Security Options
35
NetLinx Integrated Controllers (Firmware v4)- WebConsole & Programming Guide
Login Rules
There is no limit to the number of concurrent logins allowed for a single user. This allows for the creation of a single User that is
provided to multiple ICSP devices (touch panels, for example) using the same login to obtain access to the Master. For example, if
you had 50 devices connected to a Master, you would not have to create 50 individual user accounts-one for each device. Instead,
you only need to create one which all 50 devices use for access.
The first layer of security for the Master is to prompt a user to enter a valid username and password before gaining access to a
secured feature on the target Master.
Depending on the Security configuration, Users may be prompted to enter a valid username and password before gaining access to
various features of the WebConsole. User access is specified by the administrator in the Group and User Level pages of the Security
section.
NOTE:
This username and password information is also used by both G4 touch panels (within the System Connection firmware page)
and AMX software applications such as NetLinx Studio to communicate securely with a Master using encrypted communication.
User Name and Password Rules
Case-sensitive
Must be between 4 and 20 characters
The following special characters are allowed for use in User Name and Password entries:
! ” # $ % & ’ ( ) * + , - . / : ; < = > ? @ [ \ ] ^ _ ` { | } ~
Also allowed are any printable ASCII characters (
including "space"
): A-Z, a-z, 0-9.
System
Security - System Level
The
System Level Security
options provide authorized users the ability to alter the current security options of the entire system
assigned to the Master.
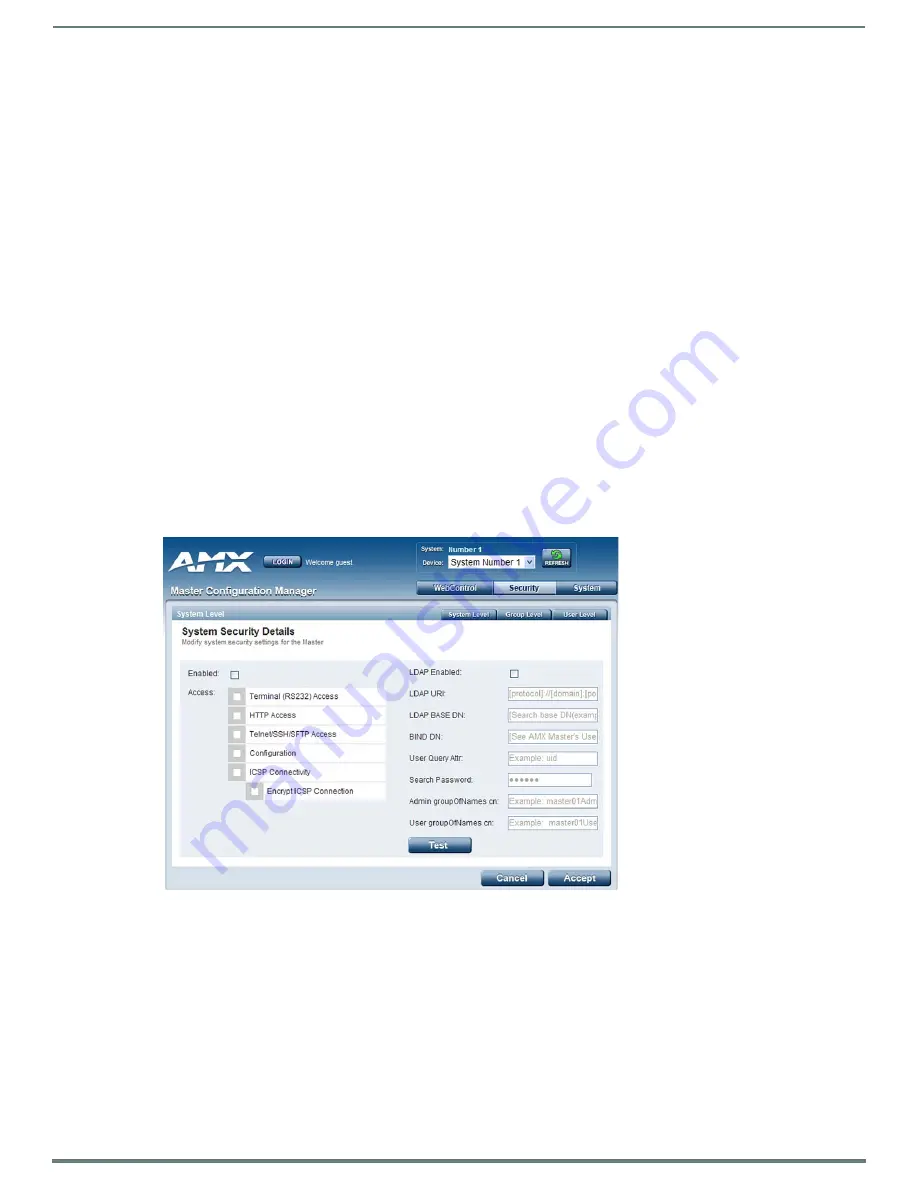
System Level Security - System Security Settings
Click the
System Security Settings
link to access the System Security Details page (FIG. 38). The options in this page allow you to
establish whether the Master will require a valid username and password be entered prior to gaining access to the configuration
options.
These are global options that enable or disable the login requirement for both users and groups.
FIG. 38
System Security Settings Page