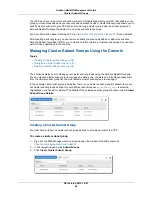
4.
Do one of the following:
•
Take one of the following rule actions.
Do this...
To...
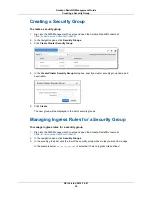
In the Connection Type bock, click CIDR/IP.
In the CIDR/IP to Authorize box, specify the range.
Click Authorize.
Add an ingress rule based on
CIDR/IP
Under Connection Type, select EC2 Security Group.
In the AWS Account select, the account to use. By default the
account currently logged into the console is used. In this case,
you need click the name of the EC2 security group you want
in the EC2 Security Group Name box.
If you change the AWS Account to Another account, you will
must specify values for both the AWS Account ID and EC2
Security Group.
Click Authorize.
Add an ingress rule based on
an EC2 Security Group
API Version 2012-12-01
35
Amazon Redshift Management Guide
Managing Ingress Rules for a Security Group