Chapter 10 Maintenance
NWA1000 Series User’s Guide
111
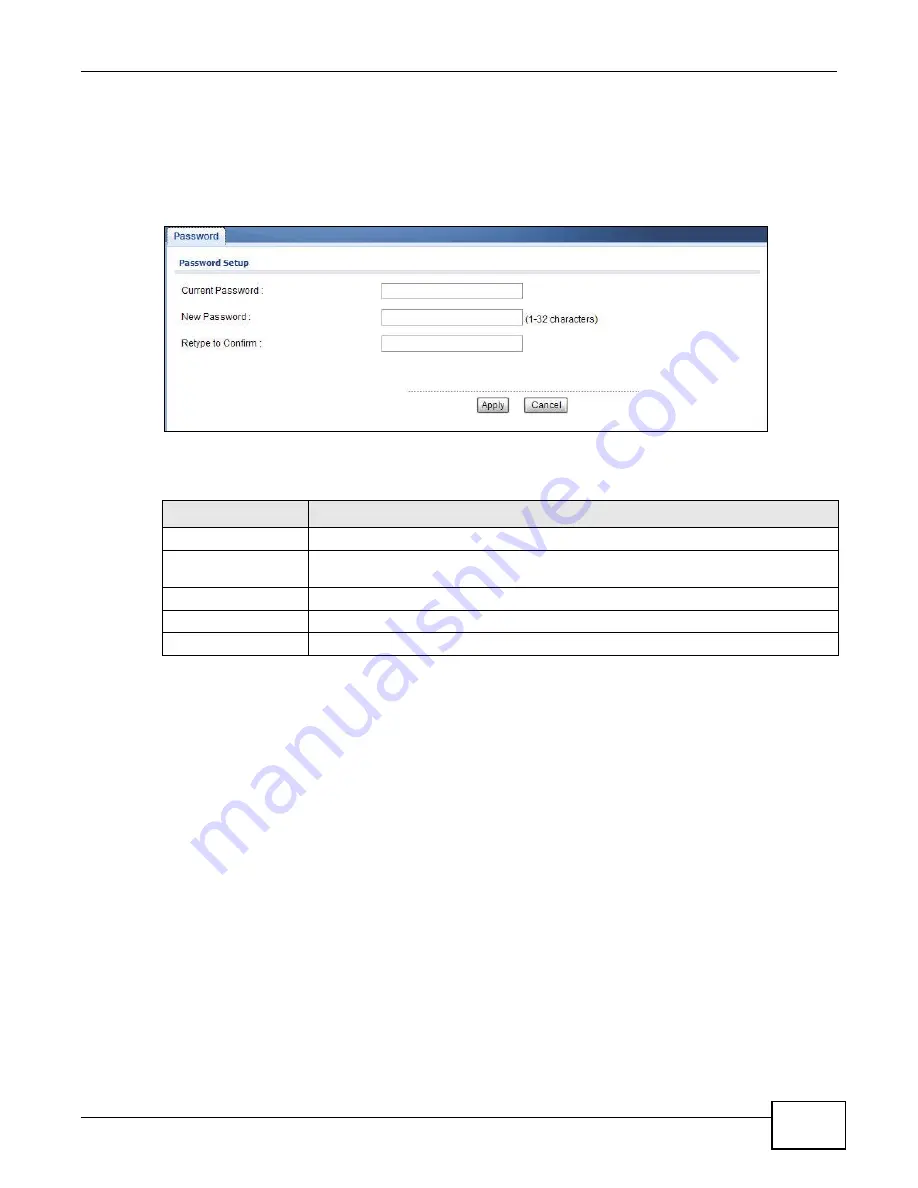
10.5 Password Screen
Use this screen to control access to your NWA by assigning a password to it. Click
Maintenance >
Password
. The following screen displays.
Figure 58
Maintenance > Password
The following table describes the labels in this screen.
Table 35
Maintenance > Password
LABEL
DESCRIPTIONS
Current Password
Type in your existing system password.
New Password
Type your new system password. Note that as you type a password, the screen
displays a dot (.) for each character you type.
Retype to Confirm
Retype your new system password for confirmation.
Apply
Click
Apply
to save your changes.
Cancel
Click
Cancel
to reload the previous configuration for this screen.
















































