aXsGUARD Identifier 3.0.2.0 Product Guide v1.5
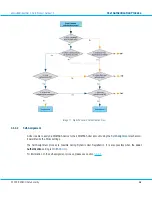
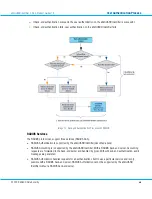
User Authentication Process
3.7
Authorization Profiles/Attributes
Some IIS Modules, e.g. IIS module for basic authentication, utilize User attributes to allow a website to retrieve
authorization information from local accounts following successful authentication. For more information, please
refer to relevant IIS module documentation.
Individual User attributes may be set for a DIGIPASS User account. The aXsGUARD Identifier returns these
attributes to the Web Application during authentication, if requested. User Attribute settings are listed in the table
below.
User attributes are only supported by SOAP and SEAL requests.
Table 6: User Attribute Settings
Setting
Explanation
A name for the attribute as expected by the Web Application.
Attribute Group
An Attribute Group is specified by the Web Application as a parameter to the authorization request.
When multiple IIS Modules are in use, the specified Attribute Group ensures that only attributes required
by the specific Web Application are used.
Usage
Basic
indicates that the attribute is for use by the IIS Modules for Basic Authentication.
Value
The Value set for an attribute is the required value of the named attribute.
3.8
Host Code Generation
3.8.1
Concept
A DIGIPASS Host Code is a One Time Password generated by the server, and verified by the end user. Host Codes
are used to authenticate the server to the end user, and therefore protect against server spoofing. Spoof servers
simulate a server, leading end users to believe they are the valid server, and attempt to acquire end user identity
credentials. The DIGIPASS Host Code helps to protect against spoof servers, which are unable to generate valid
Host Codes. Host Codes offer:
Spoof server detection: end users can detect connection to a spoof server and terminate the connection, if
the
correct Host Code is not generated.
Spoof server tracing: spoof servers can still deceive end users by requesting the valid server to generate the
Host Code and sending this code to the end user. However, once the spoof server has contacted the valid
server, the latter has a record of the connection in its log files, which can be used to trace the spoof server.
Once the spoof server has been traced, any further connections can be rejected by the valid server.
©
2009 VASCO Data Security
52