The utility database
18
The date and time of the software build appears in the version string in ISO
datetime format:
YYYY-MM-DD hh:mm:ss
where
The message log continues to exist until you drop the database. If your message
log ever becomes too large, you can archive it while no users are connected to
the database, and then create a new, empty dbname.iqmsg file before allowing
another user to connect.
The utility database
The
utility
database is essentially a database that never holds data. The database
server uses it at times when it needs a database to connect to, but either no real
database exists, or none should be running. Adaptive Server IQ installation
creates the
utility
database automatically.
Be sure you do not delete this database. You need it to do any of these things:
•
Start the database server using the
START ENGINE
command with no
database specified
•
Create or drop a database when you have no other database to connect to
•
Start the database server or connect to a database when any other databases
you have are either corrupt or unavailable due to media failure
•
Restore a database
By default, the
utility
database has the user ID
dba
and the password
sql
. You
can change these to other values during installation, or later by editing the
connection parameters in the util_db.ini file in your executable directory.
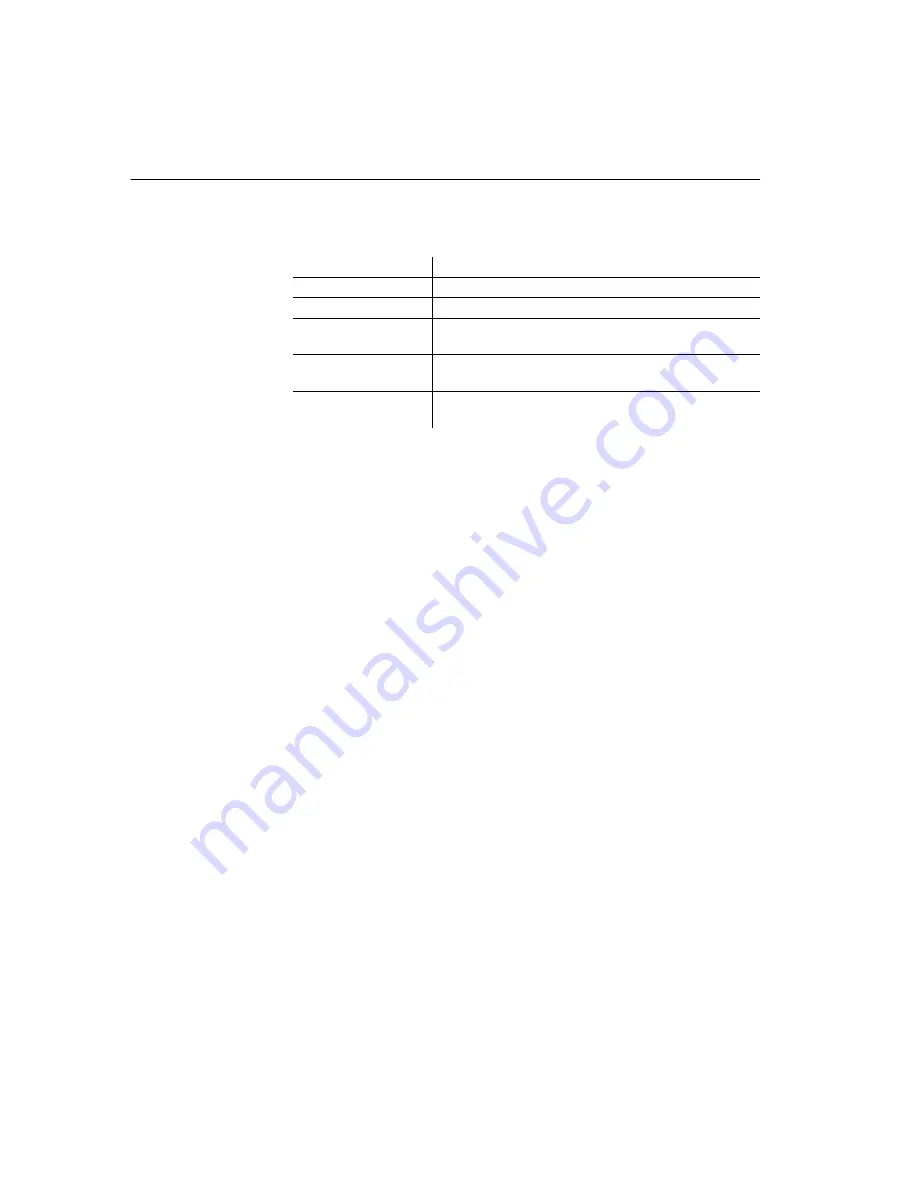
YYYY
4-digit year
MM
2-digit month number (0-12)
DD
2-digit day of month number (0-31)
hh
2-digit numbmer of complete hours that have passed since
midnight (00-23)
mm
2-digit number of complete minutes that have passed since
the start of the hour (00-59)
ss
2-digit number of complete seconds that have passed since
the start of the minute (00-59)
Summary of Contents for Adaptive Server IQ 12.4.2
Page 1: ...Administration and Performance Guide Adaptive Server IQ 12 4 2 ...
Page 16: ...xvi ...
Page 20: ...Related documents xx ...
Page 40: ...Compatibility with earlier versions 20 ...
Page 118: ...Troubleshooting startup shutdown and connections 98 ...
Page 248: ...Importing data by replication 228 ...
Page 306: ...Integrity rules in the system tables 286 ...
Page 334: ...Cursors in transactions 314 ...
Page 396: ...Users and permissions in the system tables 376 ...
Page 438: ...Determining your data backup and recovery strategy 418 ...
Page 484: ...Network performance 464 ...
Page 500: ...System utilities to monitor CPU use 480 ...
Page 514: ...Characteristics of Open Client and jConnect connections 494 ...
Page 536: ...Index 516 ...
















































