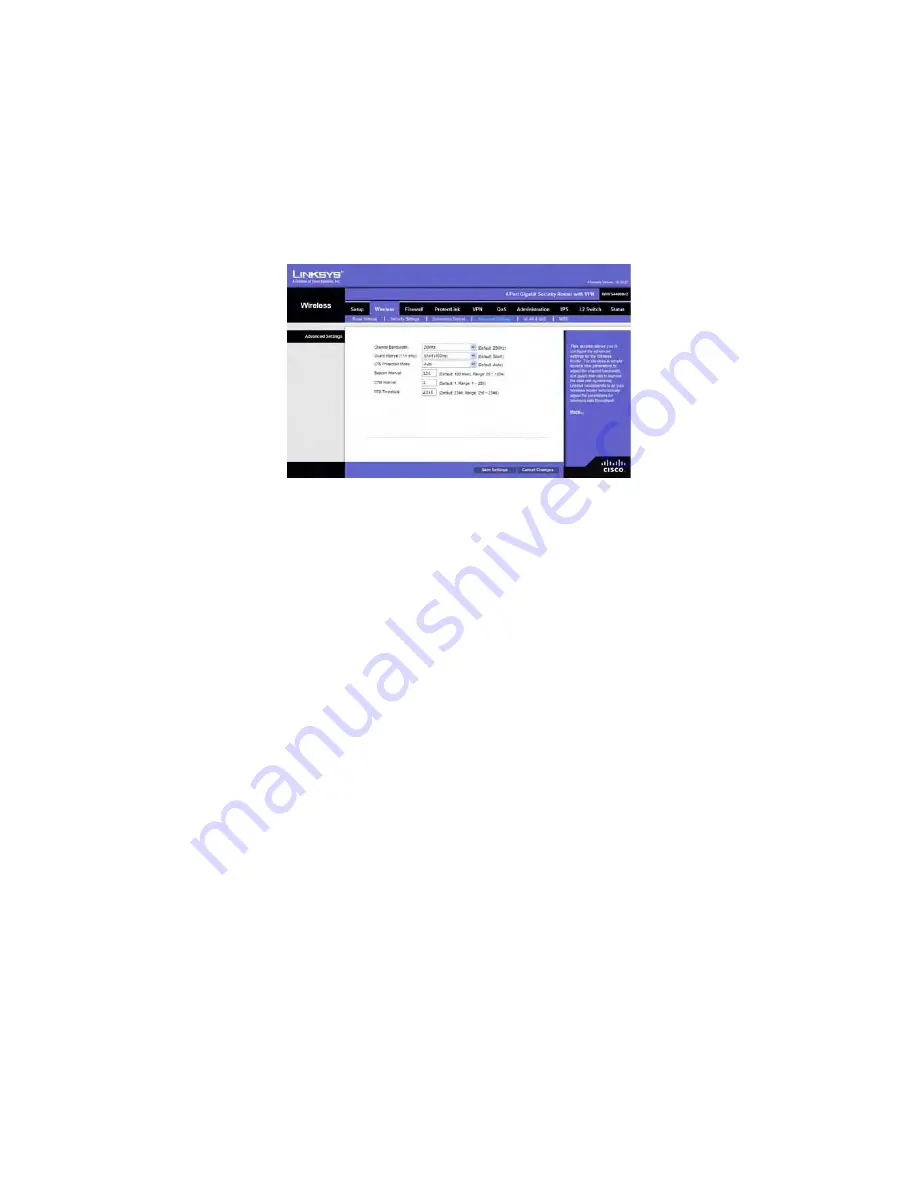
Advanced Wireless Settings
This screen allows you to configure the advanced settings for the Wireless Router. The
Wireless-N Router adopts several new parameters to adjust the channel bandwidth and
guard intervals to improve the data rate dynamically. Linksys recommends to let your
Wireless Router automatically adjust the parameters for maximum data throughput.
Advanced Settings
You can change the following advanced parameters (some only for Wireless-N) for this
Wireless Router.
Channel Bandwidth
. You can select the channel bandwidth manually for Wireless-N
connections. When it is set to 20MHz, only the 20MHz channel is used. When it is set to
40MHz, Wireless-N connections will use 40MHz channel but Wireless-B and Wireless-G
will still use 20MHz channel. When it is set to Auto, it allows wireless clients to negotiate
the bandwidth to use. The default is 20MHz.
Guard Interval
. You can select the guard interval manually for Wireless-N connections.
The two options are
Short (400ns)
and
Long (800ns)
. The default is
Auto
.
CTS Protection Mode
. CTS (Clear-To-Send) Protection Mode function boosts the
Wireless Router’s ability to catch all wireless transmissions, but will severely decrease
performance. Keep the default setting,
Auto
, so the Wireless Router can use this feature
as needed, when the Wireless-N/G products are not able to transmit to the Wireless
Router in an environment with heavy 802.11b traffic. Select
Disabled
if you want to
permanently disable this feature.
Beacon Interval.
This value indicates the frequency interval of the beacon. A beacon is
a packet broadcast by the Wireless Router to keep the network synchronized. A beacon
includes the wireless networks service area, the Wireless Router address, the Broadcast
destination addresses, a time stamp, Delivery Traffic Indicator Maps, and the Traffic
Indicator Message (TIM). The default is
100
ms.
DTIM Interval
. This value indicates how often the Wireless Router sends out a Delivery
Traffic Indication Message (DTIM). Lower settings result in more efficient networking,
while preventing your PC from dropping into power-saving sleep mode. Higher settings
allow your PC to enter sleep mode, thus saving power, but interferes with wireless
transmissions. The default is
1
ms.
RTS Threshold.
This setting determines how large a packet can be before the Wireless
Summary of Contents for Linksys WRVS4400N
Page 21: ......
Page 24: ......
Page 28: ...Configuring the Wireless N Router for directions on how to set up the Wireless N Router ...
Page 53: ......
















































