39
Chain rule
The Chain rule determines whether the access from the hosts is allowed or not. It can be one of
these two values:
ACCEPT : access allowed
DROP : access not allowed
The rule can be configured to apply to a particular Group level (All, User, Super, Administrator).
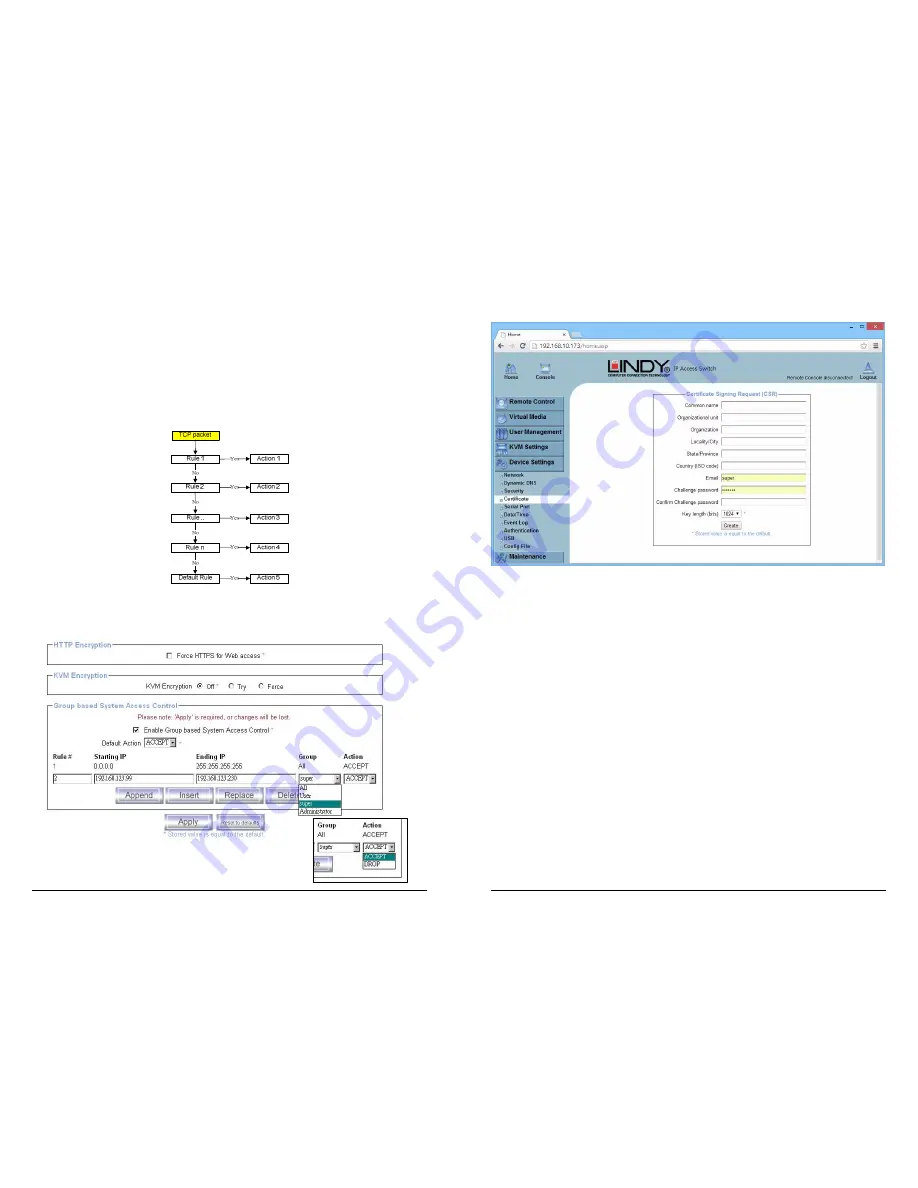
When the IP-KVM receives a TCP packet, it will process the packet with the chain rule depicted
below. The process ordering is important; the packet will enter the chain at rule 1 first, if it meets
the rule then take action directly, otherwise go to chain rule 2.
Check the “Enable Group based System Access Control” to edit the rules
Users can add a new IP filtering rule by populating the fields in the new line by using Append or
Insert. Users can remove a rule by using Replace or Delete. Use Apply to save your changes.
40
5.5.4 Certificate
The KVM OVER IP SWITCH uses the Secure Socket Layer (SSL) protocol for any encrypted
network traffic between itself and a connected client. During the connection establishment the
KVM OVER IP SWITCH has to expose its identity to a client using a cryptographic certificate.
This certificate and the underlying secret key is the same for all KVM OVER IP SWITCH units
and certainly will not match the network configuration that will be applied to the KVM OVER IP
SWITCH by its user. The certificate's underlying secret key is also used for securing the SSL
handshake. Hence, this is a security risk (but far better than no encryption at all).
However, it is possible to generate and install a new certificate that is unique for a particular
KVM OVER IP SWITCH . In order to do this, the KVM OVER IP SWITCH is able to generate a
new cryptographic key and the associated Certificate Signing Request (CSR) that needs to be
certified by a certification authority (CA). A certification authority verifies that you are the person
you claim you are, and signs and issues a SSL certificate to you.
The following steps are necessary to create and install an SSL certificate for the KVM OVER IP
SWITCH :
1. Create an SSL Certificate Signing Request using the panel shown in the screen shot
above. You need to fill out a number of fields that are explained on the next page. Once
this is done, click on the Create button to initiate the Certificate Signing Request
generation. The CSR can be downloaded to your administration machine with the
Download CSR button (see the illustration on the next page).
2. Send the saved CSR to a CA for certification. You will get the new certificate from the CA
after a more or less complicated traditional authentication process (depending on the
CA).
3. Upload the certificate to the KVM OVER IP SWITCH switch using the Upload button.











































