316
Figure 4-12-1:
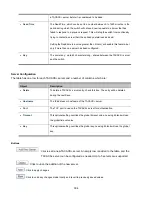
Port Limit Control Configuration Overview Page Screenshot
The page includes the following fields:
System Configuration
Object
Description
Mode
Indicates if Limit Control is globally enabled or disabled on the switchstack. If
globally disabled, other modules may still use the underlying functionality, but
limit checks and corresponding actions are disabled.
Aging Enabled
If checked, secured MAC addresses are subject to aging as discussed under
Aging Period.
Aging Period
If Aging Enabled is checked, then the aging period is controlled with this input. If
other modules are using the underlying port security for securing MAC
addresses, they may have other requirements to the aging period. The
underlying port security will use the shorter requested aging period of all modules
that use the functionality.
The Aging Period can be set to a number between 10 and 10,000,000 seconds.
To understand why aging may be desired, consider the following scenario:
Suppose an end-host is connected to a 3rd party switch or hub, which in turn is
connected to a port on this switch on which Limit Control is enabled. The
end-host will be allowed to forward if the limit is not exceeded. Now suppose that
the end-host logs off or powers down. If it wasn't for aging, the end-host would
still take up resources on this switch and will be allowed to forward. To overcome
this situation, enable aging. With aging enabled, a timer is started once the
end-host gets secured. When the timer expires, the switch starts looking for
frames from the end-host, and if such frames are not seen within the next Aging
Period, the end-host is assumed to be disconnected, and the corresponding
resources are freed on the switch.
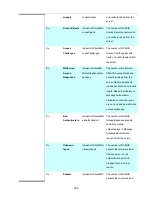
Port Configuration
The table has one row for each port on the selected switch in the stack and a number of columns, which are:
Object
Description
Port
The port number for which the configuration below applies.
Summary of Contents for NS4750-24S-4T-4X
Page 1: ...NS4750 24S 4T 4X User Manual P N 1702826 REV 00 01 ISS 14JUL14 ...
Page 56: ...56 Figure 4 2 7 Privilege Levels Configuration Page Screenshot ...
Page 110: ...110 Figure 4 4 6 Mirror Configuration Page Screenshot ...
Page 117: ...117 Figure 4 5 4 LACP Port Configuration Page Screenshot ...
Page 174: ...174 Figure 4 7 10 MST1 MSTI Port Configuration Page Screenshot ...
Page 180: ...180 Figure 4 8 2 Multicast Flooding ...
Page 249: ...249 Figure 4 9 18 Voice VLAN Configuration Page Screenshot ...
Page 271: ...271 Counter Counts the number of frames that match this ACE ...
Page 281: ...281 Figure 4 11 4 Network Access Server Configuration Page Screenshot ...
Page 315: ...315 ...
Page 328: ...328 ...
Page 335: ...335 ...
Page 346: ...346 Figure 4 14 1 LLDP Configuration Page Screenshot ...
Page 350: ...350 Figure 4 14 2 LLDP MED Configuration Page Screenshot ...
Page 372: ...372 Figure 4 16 1 Loop Protection Configuration Page Screenshot ...