MAN-0077 Honeywell Global Tracking Ltd
23
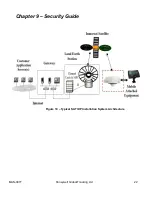
9.1 Security Checklists
You can mitigate the potential security risk to your site by following the steps listed under each threat.
9.1.1 Infection by Malicious Software Agents
This threat encompasses malicious software agents, for example viruses, spyware (Trojans), and worms. The
intrusion of malicious software agents can result in:
Performance degradation
Loss of system availability
The capture, modification, or deletion of data.
Mitigation steps
Ensure virus protection is installed, signature
files are up-to-date, and subscriptions are
active on all machines hosting Honeywell
products.
Recommend that all SAT IDP software
installed should be authorized and approved
by Honeywell.
Use a firewall at the interface between other
networks and Honeywell components.
9.1.2 Unauthorized External Access
This threat includes intrusion into your Honeywell system from the business network or other external networks
including the Internet.
Unauthorized external access can result in:
Loss of system availability
The capture, modification, or deletion of data
Reputation damage if the external access security breach becomes public knowledge.