32
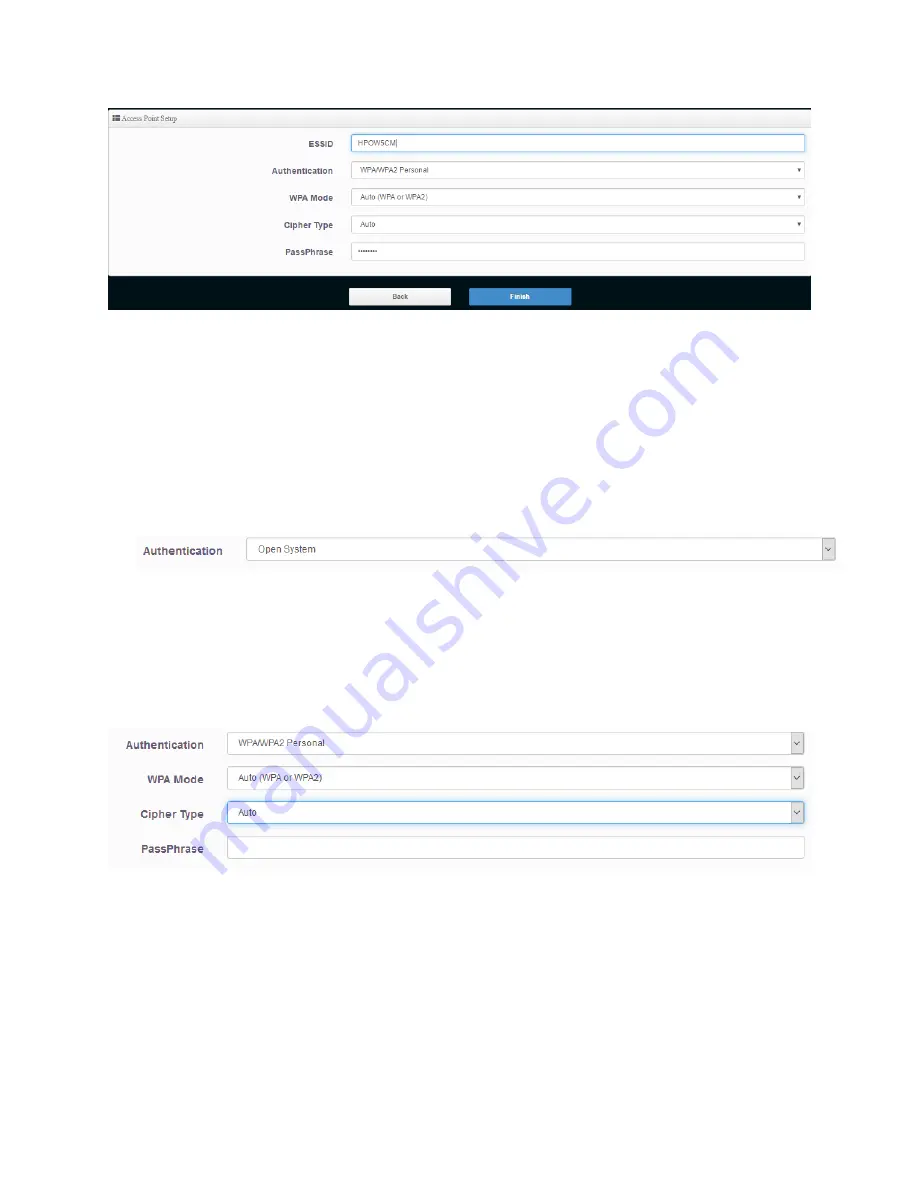
3-2-2-1 Authentication (Wireless Security)
This section allows you to set up wireless security to prevent any unauthorized access to your wireless
network
Open System (security disabled)
When you select this mode, data encryption is disabled, and every wireless device in proximity will
be able to connect your wireless access point if no other security measure is enabled
Use this option only when you want to allow any user to use your wireless access point, and you
are not concerned about unauthorized access to your files and/or transfers over your network.
Wi-Fi Protected Access (WPA-PSK or WPA2-PSK):
When you select this mode, the wireless access point will use WPA encryption, and the following
setup menu will be shown on your web browser:
Cipher Type:
AES is short for Advanced Encryption Standard, The AES cipher is specified as a
number of repetitions of transformation rounds that convert the input plain text
into the final output of ciphertext. Each round consists of several processing
steps, including one that depends on the encryption key. A set of reverse rounds
are applied to transform ciphertext back into the original plaintext using the
same encryption key. TKIP is short for Temporal Key Integrity Protocol, TKIP
scrambles the keys using a hashing algorithm and, by adding an integrity-
checking feature, ensures that the keys haven’t been tampered with.
Summary of Contents for HPOW5CM
Page 21: ...20...
Page 50: ...49 Settings can be modified via the VLAN setup after configuration is complete See section 4 3...
Page 126: ...125...
















































