14-11
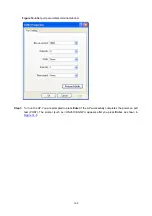
To ensure successful login, change the settings of the terminal emulation program running on the PC,
as shown in
, to make them consistent with those on the AP.
Configuring Scheme Authentication for Console Port Login
Configuration procedure
Follow these steps to configure scheme authentication for console port login:
To do…
Use the command…
Remarks
Enter system view
system-view
—
Enter console user interface
view
user-interface console
0
—
Enable scheme authentication
authentication-mode
scheme
Required
By default, users that log in through the
console port are not authenticated.
Quit to system view
quit
—
Enter the default
ISP domain view
domain
domain name
Apply an AAA
scheme to the
domain
authentication default
{
local
|
none
|
radius-scheme
radius-scheme-name
[
local
] }
Configure
the
authenticati
on mode
Quit to system
view
quit
Optional
By default, the local AAA scheme is applied. If
you specify to apply the local AAA scheme,
perform the configuration concerning local
user as well.
If you apply an existing scheme by providing
the
radius
-
scheme-name
argument, perform
the following configuration as well:
z
Perform AAA-RADIUS configuration on
the AP. (For more information, see
AAA
in
the
Security Configuration Guide
.)
z
Configure the user name and password on
the AAA server. (For more information,
see
AAA
in the
Security Configuration
Guide
.)
Create a local user (Enter local
user view.)
local-user
user-name
Required
By default, no local user exists.
Set the authentication password
for the local user
password
{
simple
|
cipher
}
password
Required
Specifies the level of the local
user
authorization-attribute
level level
Optional
By default, commands of level 0 are available
to Telnet users authenticated by password
Specify the service type for the
local user
service-type terminal
Required
By default, a user is authorized with no
service.
z
When you log in to an AP by using the scheme authentication mode, your access rights depend on
your user level defined in the AAA scheme.
z
When the local scheme authentication mode is used, the user levels are specified by using the
authorization-attribute level level
command.
z
When the RADIUS scheme authentication mode is used, the user levels are set on the
corresponding RADIUS servers.
Summary of Contents for WA Series
Page 10: ...v 15 Index 15 1...