❏
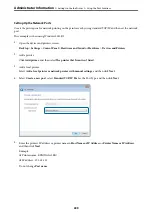
Windows:
Select
Control Panel
>
Network and Internet
>
Internet Options
>
Connections
>
LAN settings
>
Proxy server
, and then configure not to use the proxy server for LAN (local addresses).
❏
Mac OS:
Select
System Preferences
>
Network
>
Advanced
>
Proxies
, and then register the local address
for
Bypass proxy settings for these Hosts & Domains
.
Example:
192.168.1.*: Local address 192.168.1.XXX, subnet mask 255.255.255.0
192.168.*.*: Local address 192.168.XXX.XXX, subnet mask 255.255.0.0
Managing the Printer
Introduction of Product Security Features
This section introduces the security function of the Epson Devices.
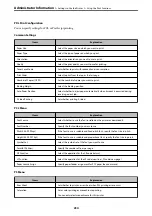
Feature name
Feature type
What to set
What to prevent
Setup for the
administrator
password
Locks the system settings,
such as connection setup for
network or USB.
An administrator sets a
password to the device.
You can set or change from
both Web Config and the
printer's control panel.
Prevent from illegally reading
and changing the
information stored in the
device such as ID, password,
network settings, and so on.
Also, reduce a wide range of
security risks such as leakage
of information for the
network environment or
security policy.
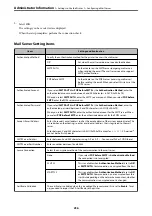
Setup for access
control
If you log on with a user
account registered in
advance, you are allowed to
use the printer.
Protects from illegal access by
any system other than the
authentication system when
using it.
Register any user account.
You can register up to 10 user
accounts.
The risk of leakage and
unauthorized viewing of data
can be reduced by
minimizing the numbers of
functions in accordance with
the business content and the
role of the user.
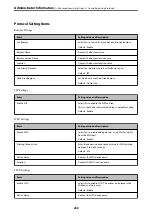
Setup for external
interface
Controls the interface that
connects to the device.
Enable or disable USB
connection with the
computer.
❏
USB connection of
computer: Prevents
unauthorized use of the
device by prohibiting
printing without going
through the network.
Related Information
&
“Application for Configuring Printer Operations (Web Config)” on page 221
&
“Configuring the Administrator Password” on page 244
&
“Restricting Available Features” on page 249
&
“Disabling the External Interface” on page 251
>
>
Introduction of Product Security Features
243