49
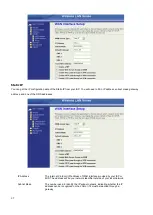
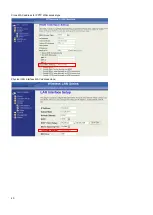
Configuring DMZ
A Demilitarized Zone is used to provide Internet services without sacrificing unauthorized access to its local private network.
Typically, the DMZ host contains devices accessible to Internet traffic, such as Web (HTTP) servers, FTP servers, SMTP (e-
mail) servers and DNS servers. All inbound packets will be redirected to the computer you set. It also is useful if you run some
applications (e.g. Internet games) that use uncertain incoming ports.
Enable DMZ
Enables the DMZ.
DMZ Host IP Address
Input the IP Address of the computer that you want to expose to the
Internet.
Summary of Contents for DLB27 Series
Page 1: ...DLB27XX WLAN Indoor Outdoor Radio User Manual Version 1 0 0 12 14 2006...
Page 36: ...35...
Page 43: ...42 Clone MAC address for Static IP WAN access type Clone MAC address for PPPoE WAN access type...
Page 44: ...43 Clone MAC address for PPTP WAN access type Physical LAN interface MAC address clone...
Page 47: ...46 In the Dynamic Routing Table there are two routings for Network 3 and Network 4...
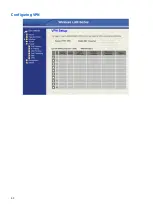
Page 51: ...50 Configuring VPN...
Page 62: ...61...