Installation Guide 11
Table 2-8
Alarm
Type
Alarm Event
Alarm Signal
Input Port
Alarm Signal
Output Port
Alarm Status
External
alarm
input
Trigger no. 1
alarm detector
ALM1
OUT1
No. 1 alarm gives an
alarm, and links all
doors to be normally
open.
Trigger no. 2
alarm detector
ALM2
Trigger no. 3
alarm detector
ALM3
OUT2
No. 2 alarm gives an
alarm, and links all
doors to be normally
closed.
Trigger no. 4
alarm detector
ALM4
Internal
alarm
input
Intrusion alarm or
unlock timeout
alarm of no. 1
door
SR1
OUT1
No. 1 alarm gives an
alarm.
Intrusion alarm or
unlock timeout
alarm of no. 2
door
SR2
OUT2
No. 2 alarm gives an
alarm.
Tamper alarm of
no. 1 door reader
RS-485/CASE
OUT1
No. 1 alarm gives an
alarm.
Tamper alarm of
no. 2 door reader
RS-485/CASE
OUT2
No. 2 alarm gives an
alarm.
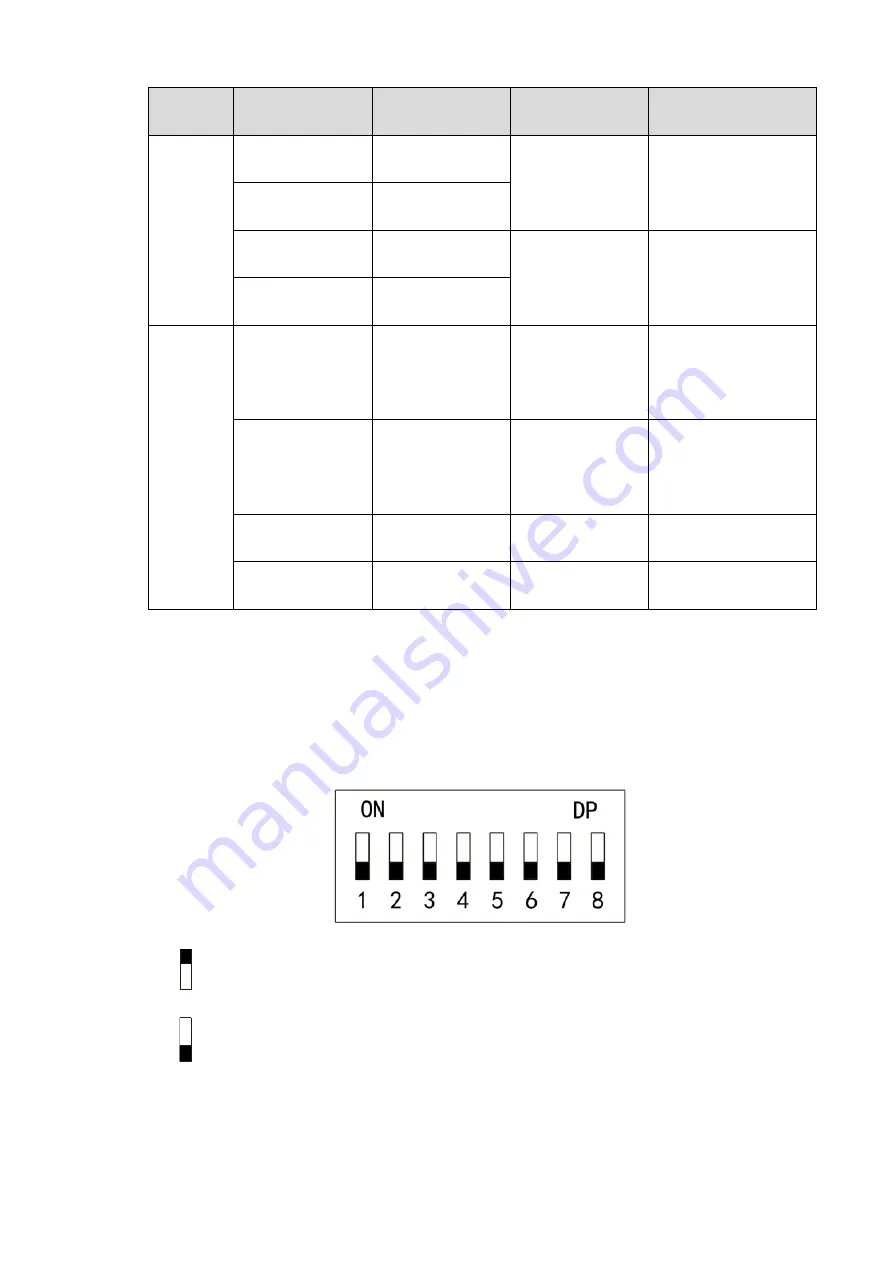
2.4 DIP Switch
Operate with DIP switch.
Figure 2-14
the switch is at ON position, meaning 1.
the switch is at the bottom, meaning 0.
1
~
8 are all 0; the system is started normally.
1
~
8 are all 1; the system enters BOOT mode after start.
1, 3, 5 and 7 are 1, while others are 0. After restart, the system restores factory defaults.
















































