16
Chapter 5: Using the Wireless Network Monitor
Accessing the Wireless Network Monitor
Wireless-G USB Network Adapter with SpeedBooster
Accessing the Wireless Network Monitor
Besides selecting
Turn on
when you right-click the icon, you can also double-click the
Wireless Network
Monitor
icon to activate the Wireless Network Monitor. Then the
Link Information
screen will appear. From this
screen, you can find out how strong the current wireless signal is and how good the connection’s quality is. You
can also click the
More Information
button to view additional status information about the current wireless
connection. To search for available wireless networks, click the
Site Survey
tab. To perform configuration
changes, click the
Profiles
tab.
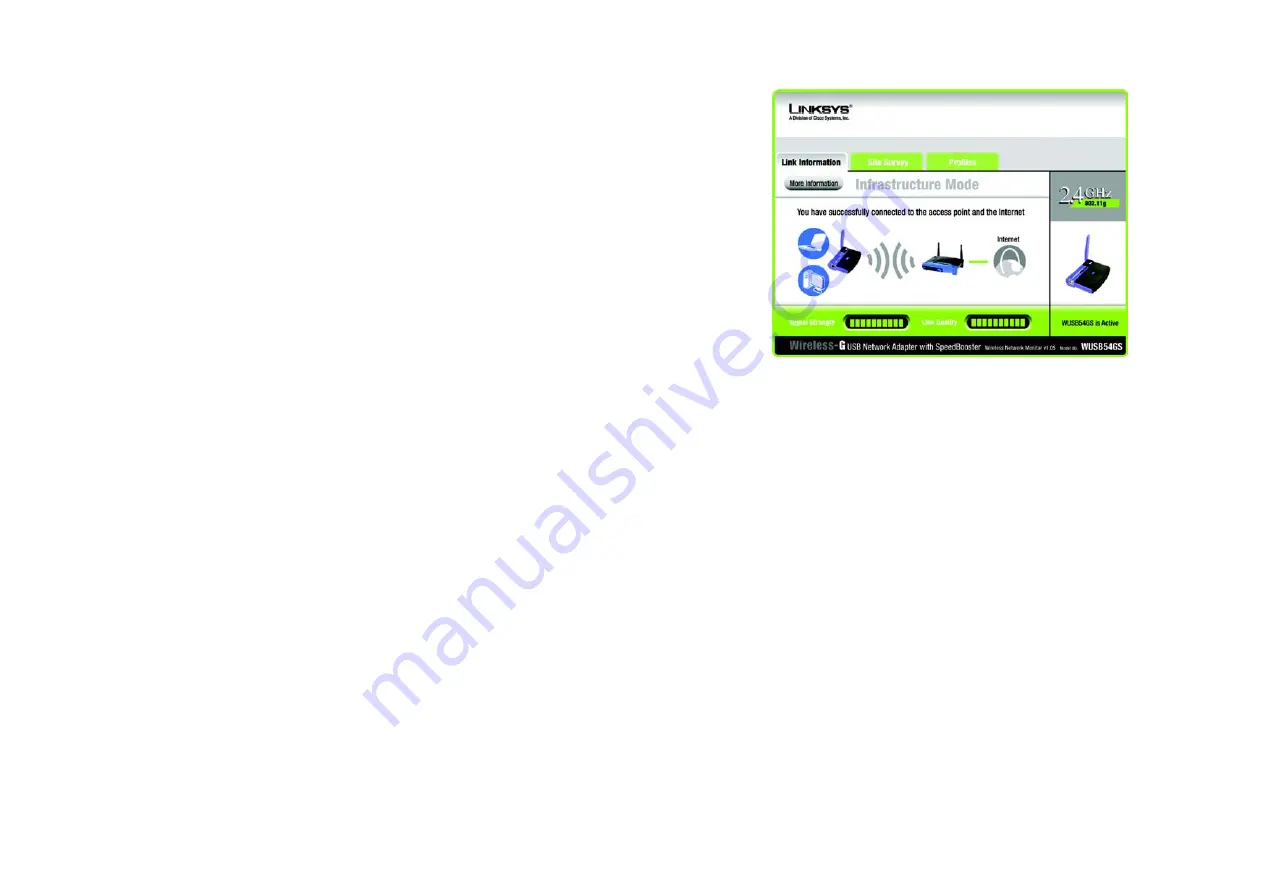
Link Information
The
Link Information
screen displays network mode, signal strength, and link quality information about the
current connection. It also provides a button to click for additional status information.
Ad-Hoc Mode
or
Infrastructure Mode
- The screen indicates whether the Adapter is currently working in ad-
hoc or infrastructure mode.
Signal Strength
- The Signal Strength bar indicates signal strength.
Link Quality
- The Link Quality bar indicates the quality of the wireless network connection.
Click the
More Information
button to view additional information about the wireless network connection.
Clicking the
More Information
button displays the
Wireless Network Status
screen, which displays more infor-
mation about the Adapter’s connection.
Figure 5-4: Link Information






























