73
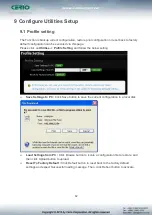
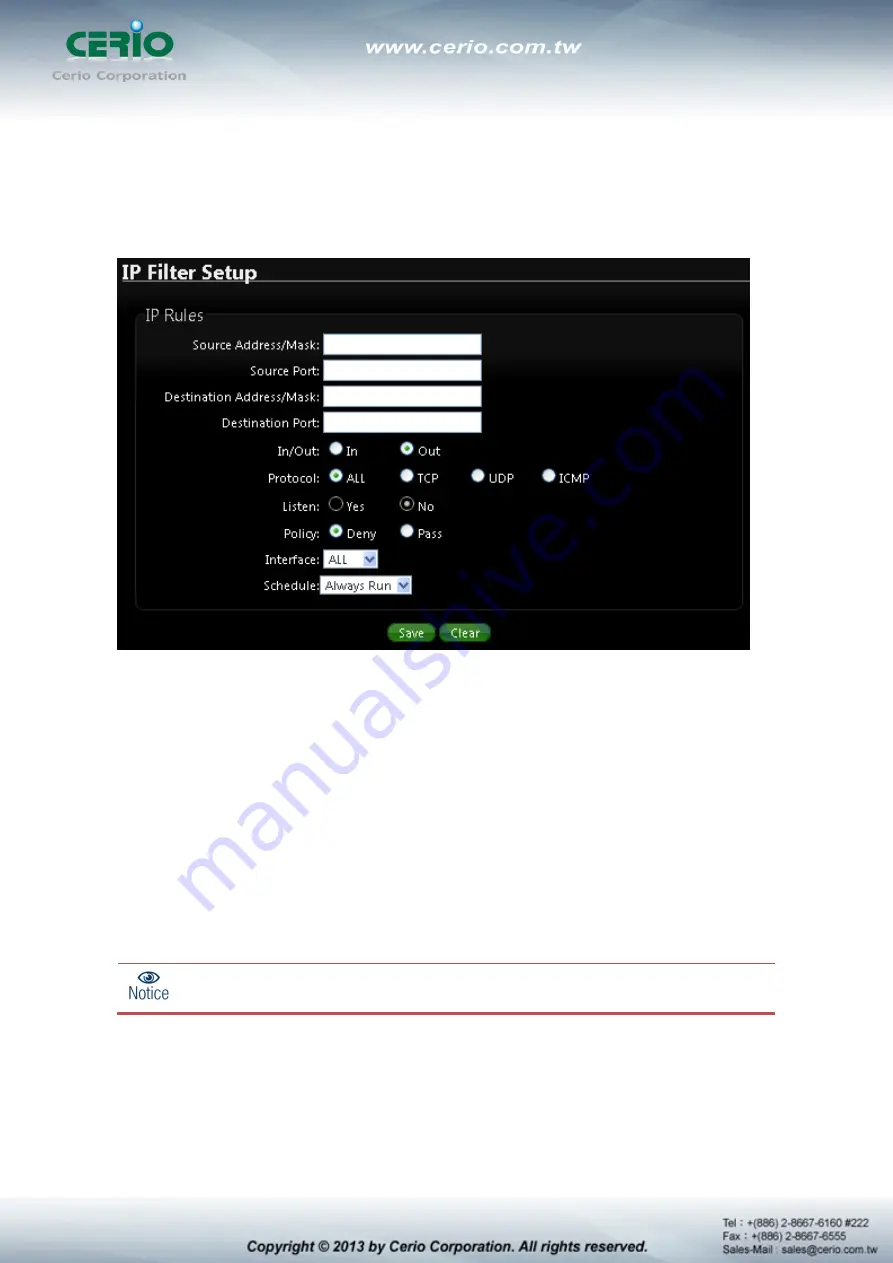
8.2 IP Filter (This function must be used WISP mode)
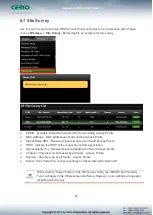
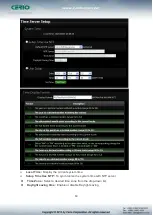
Allows to create deny or allow rules to filter ingress or egress packets from specific source
and/or to destination IP address on wired (LAN) or Wireless (WAN) ports. Filter rules could be
used to filter unicast or multicast packets on different protocols as shown in the IP Filter Setup.
Important to note that IP filter rules has precedence over Virtual server rules.
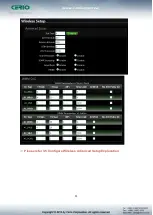
Source Address/Mask :
Enter desired source IP address and netmask. i.e.
192.168.2.10/32.
Source Port :
Enter a port or a range of ports as start:end. i.e. port 20:80
Destination Address/Mask :
Enter desired destination IP address and netmask. i.e.
192.168.1.10/32
Destination Port :
Enter a port or a range of ports as start:end. i.e. port 20:80
In/Out :
Applies to Ingress or egress packets.
Protocol :
Supports TCP, UDP or ICMP.
Listen :
Click Yes radial button to match TCP packets only with the SYN flag.
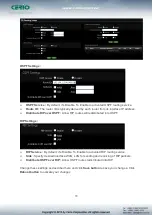
Policy :
Deny to drop and Pass to allow per filter rules
Interface :
The interface that a filter rule applies
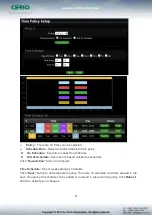
Schedule :
Can choose to use rule by “Time Policy”
Click
“Save”
button to add IP filter rule. Total of 20 rules maximum allowed in the IP Filter List.
All rules can be edited or removed from the List. Click
Reboot button
to activate your changes.
All packets are allowed by default. Deny rules could be added to the filter list to
filter out unwanted packets and leave remaining allowed.