3e–525C–2 Wireless Access Point
Chapter 4: Wireless Bridge Configuration
64
29000155-001 A
3e–525C–2 Wireless Access Point
Chapter 4: Wireless Bridge Configuration
29000155-001 A
65
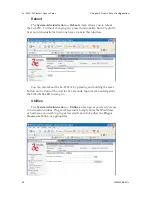
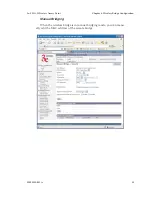
Point-to-Multipoint Bridge Configuration
A point-to-multipoint configuration allows you to set up three or
more 3e–525C–2 access points in bridging mode and accomplish bridging
between 3 or more locations wirelessly.
For the three bridges that are to be linked to communicate properly,
they have to be set up with compatible commands in their setup screens.
For instance, all bridges must have the same channel number. Span-
ning Tree Protocol will usually be set to Enable. If configured as in the
diagram following, Bridge 1 must contain all of the others' BSSIDs, while
Bridge 2 ~ n must only contain Bridge 1's BSSID. (The BSSID of each is
equivalent to the MAC address found on the
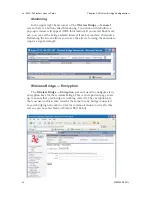
Wireless Bridge — General
page. Enter only hexadecimal numbers. Data entry is not case sensitive.)
Finally, the wireless bridging encryption of each must be set to the appro-
priate type and key length and must be the same on all.
Because the 3e–525C–2 has two separate WLAN cards, one for the
AP and one for the Bridge, each bridge can have a WLAN on the 802.11a
protocol with no loss of efficiency in bridging if you wish.
The following diagram pictures a point-to-multipoint setup, which
might be of use where a company's network spans several buildings
within a campus-like setting.
��������
��������
������ �
������ �
��������
������ �
��������
������ �
�������
�������
�������
�������
�������
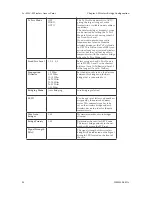
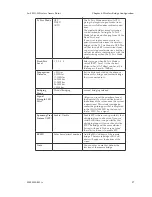
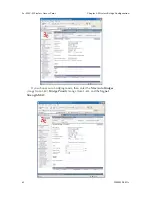
Follow the steps of the procedure outlined in the point-to-point bridge
section. The chart following describes the basic attributes.
Summary of Contents for AirGuard 3e-525C-2
Page 2: ...This page intentionally left blank ...
Page 3: ...3e Technologies International s AirGuard Wireless Access Point User s Guide Model 3e 525C 2 ...
Page 8: ...vi 29000155 0001 A This page intentionally left blank ...
Page 76: ...3e 525C 2 Wireless Access Point Chapter 4 Wireless Bridge Configuration 68 29000155 001 A ...