3e-525A Outdoor Access Point
28
29000132-001 A
29000132-001 A
29
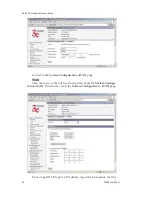
to communicate with the access point. In this case, input the MAC
addresses of all the PC cards that will be authorized to access this
access point. The MAC address is engraved or written on the PC
(PCMCIA) Card.
• If
Filtering
is enabled and
Filter Type
is
Disallow Access
, those
devices with a MAC address which has been entered in the MAC
Address listing will NOT be able to communicate with the access
point. In this case, navigate to the report:
Wireless Clients
and
copy the MAC address of any Wireless Client that you want to ex-
clude from communication with the access point and input those
MAC Addresses to the MAC Address list.
Bridging and Bridging Encryption
Bridging is covered in chapter five. If you will be deploying this 3e-
525A as a bridge, follow the instructions in chapter five.
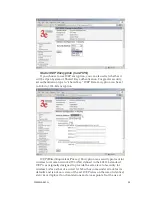
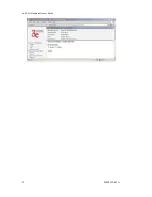
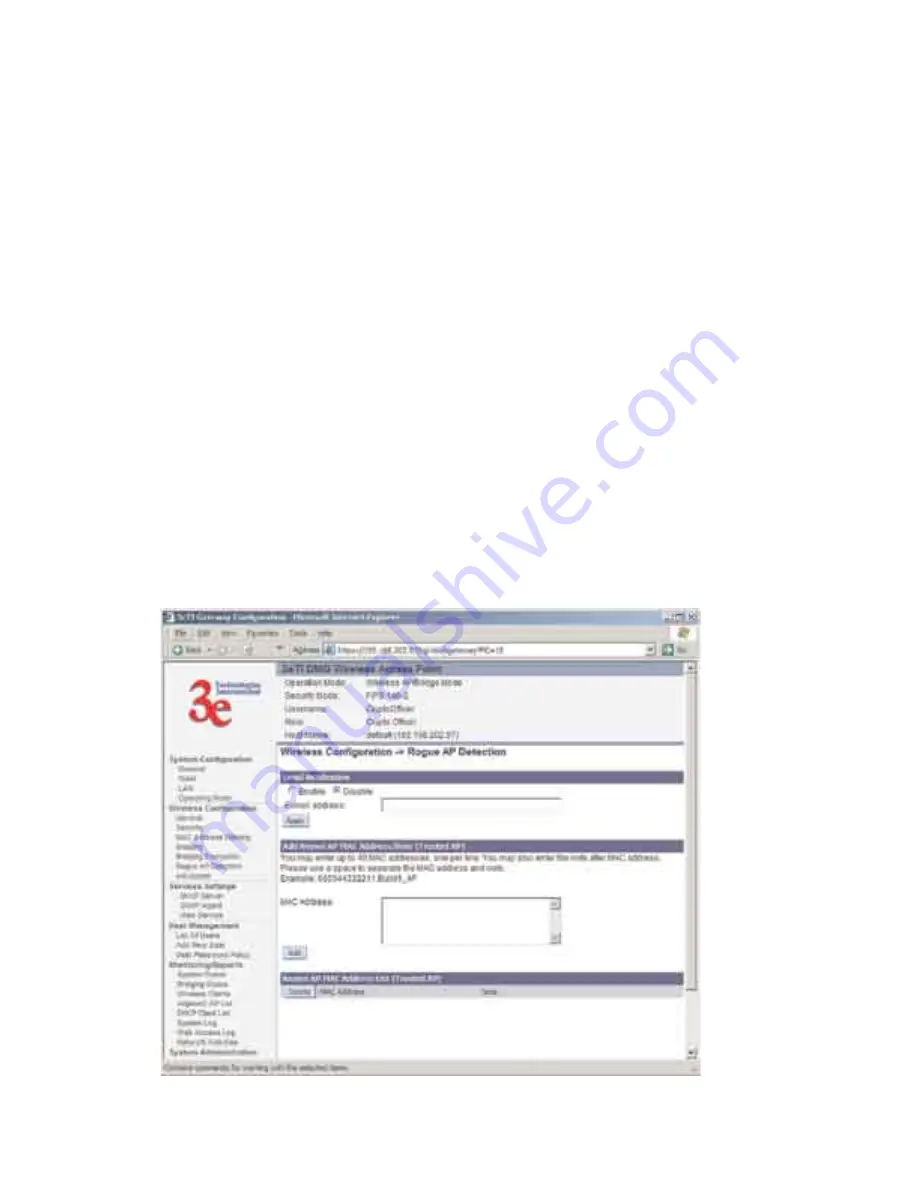
Rogue AP Detection
The Rogue AP Detection page allows the network administrator to set
up rogue AP detection. If you enable rogue AP detection, also enter the
MAC Address of each AP in the network that you want the AP being con-
figured to accept as a trusted AP. (You may add up to 20 APs.) Enter an
email address for notification of any rogue or non-trusted APs. (The MAC
Address for the 3e-525A is located on the
Setup—General
page.
The
Rogue AP list
, under
Monitoring Reports
on the navigation
menu, will detail any marauding APs.
Summary of Contents for 3e-525A
Page 3: ...This page intentionally left blank ...
Page 9: ...vi 29000132 0001 A This page intentionally left blank ...
Page 41: ...3e 525A Outdoor Access Point 32 29000132 001 A ...
Page 53: ...3e 525A Outdoor Access Point 44 29000132 001 A This page intentionality left blank ...
Page 105: ...3e 525A Wireless Access Point 96 29000132 001 A This page intentionally left blank ...