Chapter 18 IPSec VPN
ZyWALL 5/35/70 Series User’s Guide
384
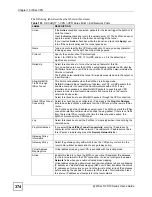
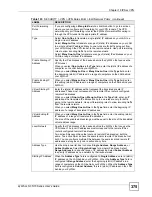
My ZyWALL
When the ZyWALL is in router mode, enter the WAN IP address of your ZyWALL
or leave the field set to
0.0.0.0
.
The ZyWALL uses its current WAN IP address (static or dynamic) in setting up the
VPN tunnel if you leave this field as
0.0.0.0
. If the WAN connection goes down, the
ZyWALL uses the dial backup IP address for the VPN tunnel when using dial
backup or the LAN IP address when using traffic redirect.
The VPN tunnel has to be rebuilt if this IP address changes.
When the ZyWALL is in bridge mode, this field is read-only and displays the
ZyWALL’s IP address.
Primary Remote
Gateway
Type the WAN IP address of the IPSec router with which you're making the VPN
connection.
Manual Proposal
SPI
Type a unique
SPI
(Security Parameter Index) from one to four characters long.
Valid Characters are "0, 1, 2, 3, 4, 5, 6, 7, 8, and 9".
Encapsulation
Mode
Select
Tunnel
mode or
Transport
mode from the drop-down list box.
Active Protocol
Select
ESP
if you want to use ESP (Encapsulation Security Payload). The ESP
protocol (RFC 2406) provides encryption as well as some of the services offered
by
AH
. If you select
ESP
here, you must select options from the
Encryption
Algorithm
and
Authentication Algorithm
fields (described next).
Select
AH
if you want to use AH (Authentication Header Protocol). The AH
protocol (RFC 2402) was designed for integrity, authentication, sequence integrity
(replay resistance), and non-repudiation but not for confidentiality, for which the
ESP was designed. If you select
AH
here, you must select options from the
Authentication Algorithm
field (described next).
Encryption
Algorithm
Select
DES
,
3DES
or
NULL
from the drop-down list box.
When
DES
is used for data communications, both sender and receiver must know
the
Encryption Key
, which can be used to encrypt and decrypt the message or to
generate and verify a message authentication code. The DES encryption
algorithm uses a 56-bit key. Triple DES (
3DES
) is a variation on DES that uses a
168-bit key. As a result,
3DES
is more secure than
DES
. It also requires more
processing power, resulting in increased latency and decreased throughput.
Select
NULL
to set up a tunnel without encryption. When you select
NULL
, you do
not enter an encryption key.
Authentication
Algorithm
Select
SHA1
or
MD5
from the drop-down list box.
MD5
(Message Digest 5) and
SHA1
(Secure Hash Algorithm) are hash algorithms used to authenticate packet
data. The
SHA1
algorithm is generally considered stronger than
MD5
, but is
slower. Select
MD5
for minimal security and
SHA-1
for maximum security.
Encryption Key
This field is applicable when you select
ESP
in the
Active
Protocol
field above.
With
DES
, type a unique key 8 characters long. With
3DES
, type a unique key 24
characters long. Any characters may be used, including spaces, but trailing
spaces are truncated.
Authentication
Key
Type a unique authentication key to be used by IPSec if applicable. Enter 16
characters for
MD5
authentication or 20 characters for
SHA-1
authentication. Any
characters may be used, including spaces, but trailing spaces are truncated.
Apply
Click
Apply
to save your changes back to the ZyWALL.
Cancel
Click
Cancel
to exit this screen without saving.
Table 107
SECURITY > VPN > VPN Rules (Manual) > Edit (continued)
LABEL
DESCRIPTION
Содержание ZyWALL 35 Series
Страница 2: ......
Страница 8: ...Safety Warnings ZyWALL 5 35 70 Series User s Guide 8 ...
Страница 52: ...List of Tables ZyWALL 5 35 70 Series User s Guide 52 ...
Страница 54: ...54 ...
Страница 60: ...Chapter 1 Getting to Know Your ZyWALL ZyWALL 5 35 70 Series User s Guide 60 ...
Страница 86: ...Chapter 2 Introducing the Web Configurator ZyWALL 5 35 70 Series User s Guide 86 ...
Страница 126: ...Chapter 4 Tutorials ZyWALL 5 35 70 Series User s Guide 126 Figure 57 SECURITY VPN VPN Rules IKE Add Network Policy ...
Страница 140: ...Chapter 4 Tutorials ZyWALL 5 35 70 Series User s Guide 140 ...
Страница 146: ...Chapter 5 Registration ZyWALL 5 35 70 Series User s Guide 146 ...
Страница 147: ...147 PART II Network LAN Screens 149 Bridge Screens 161 WAN Screens 167 DMZ Screens 203 WLAN 213 ...
Страница 148: ...148 ...
Страница 160: ...Chapter 6 LAN Screens ZyWALL 5 35 70 Series User s Guide 160 ...
Страница 173: ...Chapter 8 WAN Screens ZyWALL 5 35 70 Series User s Guide 173 Figure 93 NETWORK WAN General ...
Страница 202: ...Chapter 8 WAN Screens ZyWALL 5 35 70 Series User s Guide 202 ...
Страница 212: ...Chapter 9 DMZ Screens ZyWALL 5 35 70 Series User s Guide 212 ...
Страница 242: ...242 ...
Страница 262: ...Chapter 11 Firewall ZyWALL 5 35 70 Series User s Guide 262 Figure 146 SECURITY FIREWALL Rule Summary Edit ...
Страница 274: ...Chapter 11 Firewall ZyWALL 5 35 70 Series User s Guide 274 ...
Страница 294: ...Chapter 13 Configuring IDP ZyWALL 5 35 70 Series User s Guide 294 ...
Страница 320: ...Chapter 15 Anti Spam ZyWALL 5 35 70 Series User s Guide 320 ...
Страница 342: ...Chapter 16 Content Filtering Screens ZyWALL 5 35 70 Series User s Guide 342 ...
Страница 350: ...Chapter 17 Content Filtering Reports ZyWALL 5 35 70 Series User s Guide 350 ...
Страница 363: ...Chapter 18 IPSec VPN ZyWALL 5 35 70 Series User s Guide 363 Figure 210 SECURITY VPN VPN Rules IKE Edit Gateway Policy ...
Страница 373: ...Chapter 18 IPSec VPN ZyWALL 5 35 70 Series User s Guide 373 Figure 213 SECURITY VPN VPN Rules IKE Edit Network Policy ...
Страница 424: ...Chapter 19 Certificates ZyWALL 5 35 70 Series User s Guide 424 ...
Страница 430: ...430 ...
Страница 448: ...Chapter 21 Network Address Translation NAT ZyWALL 5 35 70 Series User s Guide 448 ...
Страница 474: ...Chapter 24 Bandwidth Management ZyWALL 5 35 70 Series User s Guide 474 ...
Страница 514: ...Chapter 26 Remote Management ZyWALL 5 35 70 Series User s Guide 514 ...
Страница 533: ...533 PART V Reports Logs and Maintenance Reports 535 Logs Screens 547 Maintenance 575 ...
Страница 534: ...534 ...
Страница 551: ...Chapter 31 Logs Screens ZyWALL 5 35 70 Series User s Guide 551 Figure 334 LOGS Log Settings ...
Страница 592: ...Chapter 32 Maintenance ZyWALL 5 35 70 Series User s Guide 592 ...
Страница 594: ...594 Troubleshooting 751 Product Specifications 757 ...
Страница 602: ...Chapter 33 Introducing the SMT ZyWALL 5 35 70 Series User s Guide 602 ...
Страница 622: ...Chapter 35 WAN and Dial Backup Setup ZyWALL 5 35 70 Series User s Guide 622 ...
Страница 628: ...Chapter 36 LAN Setup ZyWALL 5 35 70 Series User s Guide 628 ...
Страница 634: ...Chapter 37 Internet Access ZyWALL 5 35 70 Series User s Guide 634 ...
Страница 638: ...Chapter 38 DMZ Setup ZyWALL 5 35 70 Series User s Guide 638 ...
Страница 642: ...Chapter 39 Route Setup ZyWALL 5 35 70 Series User s Guide 642 ...
Страница 658: ...Chapter 41 Remote Node Setup ZyWALL 5 35 70 Series User s Guide 658 ...
Страница 662: ...Chapter 42 IP Static Route Setup ZyWALL 5 35 70 Series User s Guide 662 ...
Страница 700: ...Chapter 45 Filter Configuration ZyWALL 5 35 70 Series User s Guide 700 ...
Страница 738: ...Chapter 50 Remote Management ZyWALL 5 35 70 Series User s Guide 738 ...
Страница 746: ...Chapter 51 IP Policy Routing ZyWALL 5 35 70 Series User s Guide 746 ...
Страница 766: ...766 ...
Страница 770: ...Appendix A Hardware Installation ZyWALL 5 35 70 Series User s Guide 770 ...
Страница 778: ...Appendix B Pop up Windows JavaScripts and Java Permissions ZyWALL 5 35 70 Series User s Guide 778 ...
Страница 780: ...Appendix C Removing and Installing a Fuse ZyWALL 5 35 70 Series User s Guide 780 ...
Страница 802: ...Appendix D Setting up Your Computer s IP Address ZyWALL 5 35 70 Series User s Guide 802 ...
Страница 816: ...Appendix F Common Services ZyWALL 5 35 70 Series User s Guide 816 ...
Страница 852: ...Appendix J Importing Certificates ZyWALL 5 35 70 Series User s Guide 852 ...
Страница 856: ...Appendix K Legal Information ZyWALL 5 35 70 Series User s Guide 856 ...
Страница 862: ...Appendix L Customer Support ZyWALL 5 35 70 Series User s Guide 862 ...