XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
Ver. 2.00, March 2011
Page
28 of 50
3.4.4.1.
Access
The Xerox Service Technician must be authenticated twice:
1.
The first password, called the
PSW Lock Facility,
is obtained by calling a Xerox service location and
providing the CSE employee number and the serial number of the PSW. The password is then given to
the Xerox Service Technician, and is valid for 90 days. When the password expires, the Xerox Service
Technician must call in again. This password is unique to the client application running on that particular
PSW, and is required to log onto the PSW prior to initiating communications with the machine.
2.
Once the application is running, the PSW supplies the second password (different from the first) to
authenticate the session to the device. This embedded password is automatically passed from the
application to the machine, and is never seen by anyone. It is hardcoded in the software of the Marking
Engine and the PSW application, and is common to all products. It is not encrypted. Many of the
diagnostic routines will require this password in order to function.
3.4.4.2.
Communication Protocol
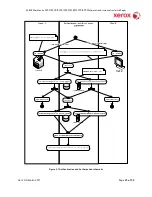
The communication process uses a Xerox proprietary protocol. Each packet passing back and forth will
have a unique identifier (session key) with it for authentication and tracking purposes. All protocols are
API based – very little information is directly transferred. For example, in order to run any given
diagnostic test, the ‘Start Test XXX’ command is sent to the Marking Engine. The Marking Engine runs
the test and responds with a “Test XXX passed (or failed)’ reply. This is illustrated in the following
diagram:
3.4.4.3.
Network Diagnostics executed from the PSW
The PSW allows the technician to execute certain Network diagnostic tests by connecting directly to the
serial port on the controller. These tests are executed with the device disconnected from the customer’s
LAN.
The tests that are available are echo tests for the various protocols (e.g. IP, IPX), where the controller
sends a dummy message to itself to test the transmit and receive capabilities of its own connectivity
stacks. Each protocol is tested individually and each test must be invoked separately. The diagnostic
sequence is as follows:
1)
After the PSW and Marking Engine have established a connection, the PSW must send the expected
synchronization message to the machine.
2)
The Marking Engine will respond with an acknowledge message containing its serial number.
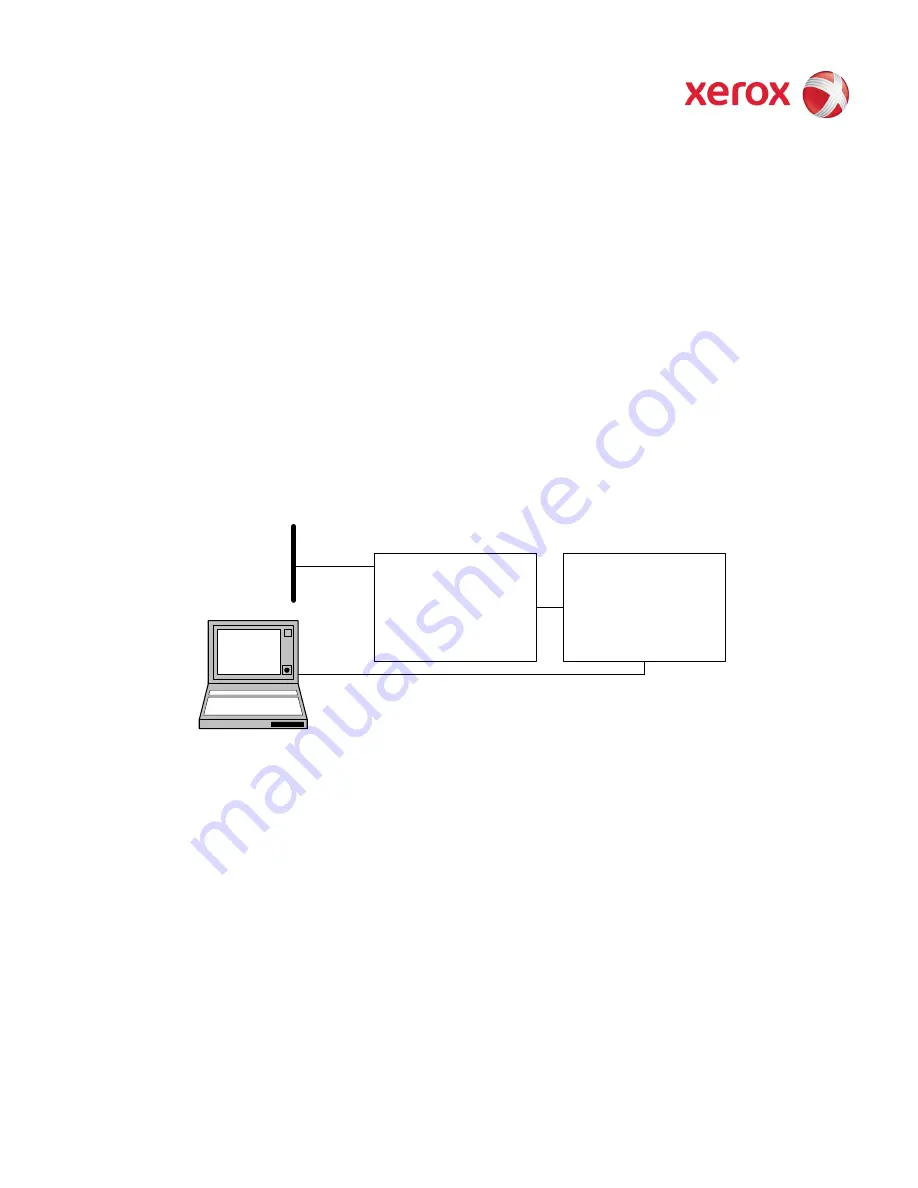
Network Controller
Marking Engine
PSW (Laptop computer)
Network
Marking Engine information may be
retrieved; no image data may be accessed