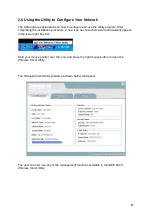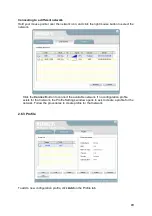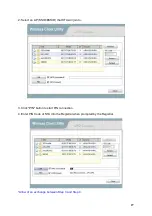
23
To define the security mode, select the security button of the desired security mode. And
then click Next to continue. Please see following table for details of security modes.
WPA/WPA2 Enables the use of Wi-Fi Protected Access (WPA).
Choosing WPA/WPA2 opens the WPA/WPA2 Security
Settings screen. The options include:
TLS (Transport Layer Security) is a Point-to-Point
Protocol (PPP) extension supporting additional
authentication methods within PPP. Transport Layer
Security (TLS) provides for mutual authentication,
integrity-protected cipher suite negotiation, and key
exchange between two endpoints.
PEAP (EAP-GTC) (Protected Extensible
Authentication Protocol) authenticates wireless
LAN clients using only server-side digital certificates
by creating an encrypted SSL/TLS tunnel between
the client and the authentication server. The tunnel
then protects the subsequent user authentication
exchange.
PEAP (EAP-MSCHAP V2) (Protected Extensible
Authentication Protocol) To use PEAP
(EAP-MSCHAP V2) security, the server must have
WPA-PEAP certificates, and the server properties
must already be set. Check with the IT manager
TTLS (Tunneled Transport Layer Security) An
EAP variant that provides mutual authentication
using a certificate for server authentication, and via a
secure TLS tunnel for the client
WPA-PSK/WPA2-PSK Enables WPA/WPA2 Passphrase security.
Fill in the WPA/WPA2 Passphrase on Security Settings
screen.
802.1x Enables 802.1x security. This option requires IT
administration.
Choosing 802.1x opens the 802.1x Security Settings
screen. The options include:
TLS
PEAP
TTLS
Содержание WUB-375L
Страница 1: ...802 11n g b Wireless USB Adapter Model WUB 375L User s Guide...
Страница 8: ......
Страница 16: ...16 STEP 11 Click Finish to complete the installation...
Страница 26: ...26 1 Click Refresh button to update available WPS APs...