TL-WN353G
54M Wireless PCI Adapter User Guide
14
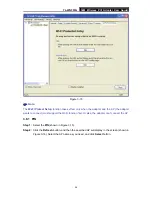
Figure 3-6
¾
Profile Name -
Please enter the Profile name which identifies the configuration profile. This
name must be unique. Note that the profile names are not case-sensitive.
¾
Network Name (SSID) -
Please enter the IEEE 802.11 wireless network name. This field has
a maximum limit of 32 characters.
)
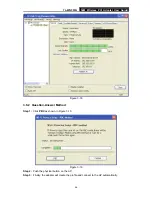
Note:
The
Profile Name
and
Network Name
are necessary for the profile, you must configure it.
¾
Channel -
If you want to use the specific channel to connect to the wireless network, select
the option “This is a computer-to-computer (ad-hoc) network; wireless access points are not
used.” If you don't select the option, the system will search the available channel to connect.
¾
Wireless network security -
This configure the security for the adapter.
)
Note:
You should configure the security for the adapter according with the wireless network that you
want to connect. If the wireless network takes some security measure, you should configure the
same security for the adapter accordingly. If the wireless network doesn’t take security measure,
you don’t need to configure the security for the adapter.
•
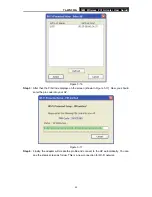
Network Authentication -
Select which mode the Wireless PCI Adapter uses to
authenticate to an access point. These modes are: Open System, Shared key,
WPA-PSK, WPA2-PSK, WPA 802.1X, WPA2 802.1X, and WEP 802.1X.
•
Data encryption -
Select the corresponding data encryption for the authentication.
These encryptions are: Disabled, WEP, TKIP and AES.