COMe-cVR6 – User Guide Rev. 1.5
// 52
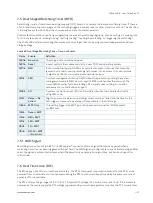
7.7.
GPIO
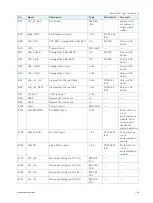
Eight GPIO pins are available, with four pins for the in-direction (pin A54 for GPI0, pin A63 for GPI1, pin A67 for GPI2 and
pin A85 for GPI3) and four pins for the out-direction (pin A93 for GPO0, pin B54 for GPO1, pin B57 for GPO2 and pin B63
for GPO3). The type of termination resistor on the module sets the direction of the GPIO where GPIs are terminated
with pull-up resistors and GPOs are terminated with pull-down resistors.
Due to, the fact that both the pull-up and pull-down termination resistors are weak, it is possible to override the
termination resistors using external pull-ups, pull-downs or IOs. Overriding the termination resistors means that the
eight GPIO pins can be considered as bi-directional since there are no restrictions whether you use the available GPIO
pins in the in-direction or out-direction.
7.8.
Trusted Platform Module (TPM 2.0)
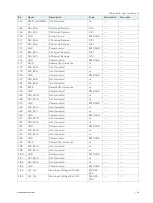
A Trusted Platform Module (TPM) stores RSA encryption keys specific to the host system for hardware
authentication. The term TPM refers to the set of specifications applicable to TPM chips. The LPC bus connects the
TPM chip to the CPU.
Each TPM chip contains an RSA key pair called the Endorsement Key (EK). The pair is maintained inside the chip and
cannot be accessed by software. The Storage Root Key (SRK) is created when a user or administrator takes ownership
of the system. This key pair is generated by the TPM based on the Endorsement Key and an owner-specified
password.
A second key, called an Attestation Identity Key (AIK) protects the device against unauthorized firmware and software
modification by hashing critical sections of firmware and software before they are executed. When the system
attempts to connect to the network, the hashes are sent to a server that verifies that they match the expected values.
If any of the hashed components have been modified since the last start, the match fails, and the system cannot gain
entry to the network.
7.9.
Kontron Security Solution
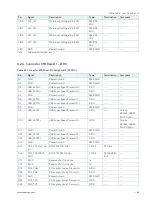
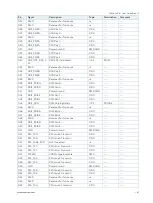
Kontron Security Solution is a combined hardware and software solution that includes an embedded hardware
security module and a software framework to provide full protection for your application.
The COMe-cVR6 includes an integrated security module connected to USB2 port 9, supporting the following features:
Copy protection
IP protection
License model enforcement
If required customers can customize the solution to meet specific needs. For more information, contact Kontron
Support.
Содержание kontron COMe-cVR6
Страница 1: ...USER GUIDE www kontron com 1 COMe cVR6 Doc User Guide Rev 1 5 Doc ID 1064 6276...
Страница 2: ...COMe cVR6 User Guide Rev 1 5 www kontron com 2 This page has been intentionally left blank...
Страница 22: ...COMe cVR6 User Guide Rev 1 5 www kontron com 22 2 3 2 Block Diagram COMe cVR6 Figure 2 Block Diagram COMe cVR6...
Страница 36: ...COMe cVR6 User Guide Rev 1 5 www kontron com 36 Figure 5 R1000 V1000 PCI Variants...