276
Step 3.
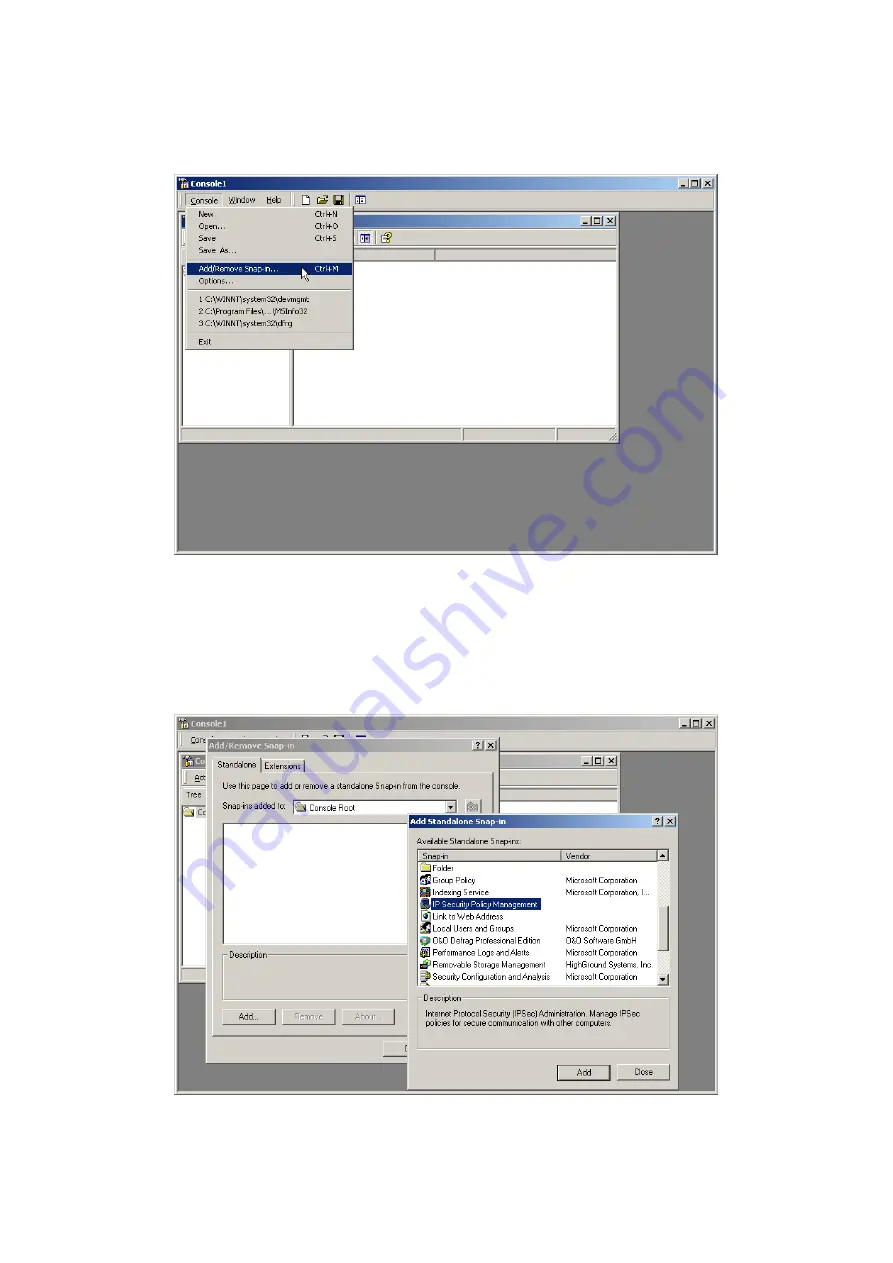
In the
Console 1
window, click
Console
on the menu bar, and then click
Add/Remove Snap-in.
(
Figure 11-64
)
Figure 11-64 Selecting “Add / Remove Snap-in” on the Console Menu
Step 4.
In the
Add / Remove Snap-in
window, click
Add
. Then, in the
Add
Standalone Snap-ins
window, select
IP Security Policy Management
and
add it.
(
Figure 11-65
)
Figure 11-65 Adding the “IP Security Policy Management”
Содержание CS-2001
Страница 9: ...8 Quick Installation Guide ...
Страница 12: ...11 CS 2001 Topology Figure2 Topology of the CS 2001 ...
Страница 20: ...19 Step 11 Settings complete Figure13 Installation Wizard Completed ...
Страница 28: ...27 System ...
Страница 35: ...34 Step 2 Click OK and then the logout message appears Figure 1 6 Figure 1 6 The Logout Message ...
Страница 47: ...46 Privacy Password The NMS uses this password to access information from the CS 2001 ...
Страница 57: ...56 Step 3 Under Policy Object Address LAN set as below Figure 2 11 Figure 2 11 Address Settings for the LAN ...
Страница 59: ...58 Figure 2 13 The Second Outgoing Policy Settings ...
Страница 60: ...59 Figure 2 14 Policy Settings Completed ...
Страница 63: ...62 Figure 2 16 First Multiple Subnet Setting ...
Страница 67: ...66 Step 5 The internal network s VLAN Figure 2 23 Figure 2 23 The Completed Mulitple Subnet VLAN Settings ...
Страница 75: ...74 Figure 2 30 DHCP Settings ...
Страница 83: ...82 Interface ...
Страница 96: ...95 Figure 3 4 Configuring the Static IPAddress Figure 3 5 Setting Completed ...
Страница 97: ...96 Figure 3 6 Configuring the Dynamic IPAddress Figure 3 7 Setting Completed ...
Страница 98: ...97 Figure 3 8 Configuring the PPPoE Figure 3 9 Setting Completed ...
Страница 101: ...100 Figure 3 10 Configuring the LAN Interface ...
Страница 105: ...104 Figure 3 13 Configuring the LAN Interface ...
Страница 111: ...110 Figure 3 18 The deployment of LAN Using Transparent Routing and NAT Routing ...
Страница 130: ...129 ...
Страница 131: ...130 Policy Object ...
Страница 150: ...149 Figure 5 11 The Added Service Group ...
Страница 152: ...151 Figure 5 14 The Completed Policy Settings ...
Страница 160: ...159 Figure 7 4 The Completed QoS Settings ...
Страница 161: ...160 Step 2 Under Policy Outgoing set as below Figure 7 5 Select the pre configured QoS setting Click OK Figure 7 6 ...
Страница 162: ...161 Figure 7 5 Applying QoS to a Policy ...
Страница 166: ...165 Figure 8 1 Authentication Management Settings ...
Страница 176: ...175 Figure 8 14 Typing a Friendly Name and the Management Address ...
Страница 178: ...177 Figure 8 16 Adding a Remote Access Policy ...
Страница 180: ...179 Step 10 Select Ethernet Figure 8 18 Figure 8 18 Selecting the Access Method ...
Страница 188: ...187 Step 20 Select Framed Protocol and click Add Figure 8 28 Figure 8 28 Adding the Attribute ...
Страница 191: ...190 Figure 8 32 Adding a User ...
Страница 195: ...194 Figure 8 39 Adding POP3 User to an Authenticated Group ...
Страница 209: ...208 Step 25 Go to Policy Object Authentication Group then add LDAP User Figure 8 66 Figure 8 66 Adding the LDAP User ...
Страница 216: ...215 Figure 9 2 Settings Completed ...
Страница 219: ...218 Figure 9 6 Settings Completed ...
Страница 229: ...228 Figure 10 9 Setting Virtual IP Figure 10 10 The Completed Virtual IP Settings ...
Страница 231: ...230 Step 4 Settings completed Figure 10 13 Figure 10 13 Multiple Servers Hosting a Single Website ...
Страница 238: ...237 Figure 10 25 A Created Group Service ...
Страница 242: ...241 Step 7 Settings completed Figure 10 32 Figure 10 32 Settings Completed ...
Страница 266: ...265 Figure 11 41 VPN Trunk Settings Figure 11 42 VPN Trunk Created ...
Страница 269: ...268 Step 13 Settings completed Figure 11 47 Figure 11 47 Deployment of IPSec VPN ...
Страница 273: ...272 Figure 11 56 VPN Trunk Settings Figure 11 57 VPN Trunk Created ...
Страница 282: ...281 Figure 11 73 VPN_B Properties ...
Страница 284: ...283 Figure 11 75 Adding an IP Filter ...
Страница 286: ...285 Figure 11 77 IP Filter Added ...
Страница 288: ...287 Figure 11 79 Ticking the Session Key Perfect Forward Secrecy ...
Страница 290: ...289 Figure 11 81 Modifying Security Method ...
Страница 292: ...291 Figure 11 83 Selecting the Connection Type ...
Страница 294: ...293 Figure 11 85 Authentication Methods Settings ...
Страница 297: ...296 Step 27 Settings completed Figure 11 88 Figure 11 88 Settings Completed ...
Страница 299: ...298 Step 29 In the New Rule Properties window click Add Figure 11 90 Figure 11 90 Clicking Add to Add an IP Filter ...
Страница 302: ...301 Step 32 Settings completed Figure 11 93 Figure 11 93 IP Filter Added ...
Страница 304: ...303 Figure 11 95 Ticking the Session Key Perfect Forward Secrecy ...
Страница 306: ...305 Figure 11 97 Modifying Security Method ...
Страница 313: ...312 Step 43 Settings completed Figure 11 104 Figure 11 104 Settings Completed ...
Страница 319: ...318 Step 53 Settings completed Figure 11 114 Figure 11 114 Deployment of IPSec VPN Using CS 2001 and Windows 2000 ...
Страница 321: ...320 and enter the management address of B Company Figure 11 117 Figure 11 117 Remote Settings ...
Страница 331: ...330 Figure 11 140 VPN Trunk Created ...
Страница 334: ...333 Step 13 Settings completed Figure 11 145 Figure 11 145 Deployment of IPSec VPN Using Aggressive Mode ...
Страница 341: ...340 Figure 11 164 VPN Trunk Settings Figure 11 165 VPN Trunk Created ...
Страница 345: ...344 Figure 11 174 ISAKMPAlgorithm Settings ...
Страница 352: ...351 Step 22 Settings completed Figure 11 194 Figure 11 194 Deployment of IPSec VPN Using GRE IPSec ...
Страница 358: ...357 1 for Key Group Figure 11 209 Figure 11 209 Configuring ISAKMPAlgorithm ...
Страница 374: ...373 Step 12 Setting completed Figure 11 249 Figure 11 249 The Deployment of IPSec VPN ...
Страница 378: ...377 Figure 11 253 Configuring the Second PPTP Server ...
Страница 379: ...378 Figure 11 254 Second PPTP Server Completed ...
Страница 389: ...388 Step 5 Settings completed Figure 11 271 Figure 11 271 The Deployment of PPTP VPN ...
Страница 396: ...395 Step 4 Setting Completed Figure 11 281 Figure 11 281 Deployment of PPTP VPN Connection ...
Страница 405: ...404 Figure 11 292 Double Clicking on Make New Connection ...
Страница 407: ...406 Figure 11 294 Phone and Modem Options ...
Страница 412: ...411 Figure 11 302 PPTP VPN Connection Successfully Connected ...
Страница 413: ...412 Step 11 Settings completed Figure 11 303 Figure 11 303 Deployment of PPTP VPN ...
Страница 414: ...413 Mail Security ...
Страница 417: ...416 Tag virus infected emails with Virus Type the subject and the content of the mail notice Click OK Figure 12 1 ...
Страница 418: ...417 Figure 12 1 Configuring the Settings of Mail Security ...
Страница 434: ...433 Figure 12 25 The User Preferences Settings Figure 12 26 User Preferences Settings Completed ...
Страница 437: ...436 Figure 12 29 Creating the Second Entry of Whitelist Figure 12 30 Settings Completed ...
Страница 439: ...438 Figure 12 32 Creating the Second Entry of Blacklist Figure 12 33 Blacklist Created ...
Страница 469: ...468 Figure 13 6 Configuring an Outgoing Policy with Group Service and POP3 Anti Spam ...
Страница 470: ...469 Figure 13 7 Policy Created ...
Страница 472: ...471 Figure 13 9 Policy Created ...
Страница 474: ...473 Figure 13 10 Creating a DMZ to WAN Policy with Group Service and POP3 Anti Spam ...
Страница 475: ...474 Figure 13 11 Policy Created ...
Страница 478: ...477 joe supportplanet com tw CS 2001 will filter the email for spam ...
Страница 482: ...481 Figure 13 17 Policy Created ...
Страница 484: ...483 Figure 13 18 Creating a DMZ to WAN Policy ...
Страница 485: ...484 Figure 13 19 Policy Created ...
Страница 492: ...491 Figure 13 31 Creating Service Groups ...
Страница 494: ...493 Figure 13 33 Policy Completed ...
Страница 496: ...495 Figure 13 34 Creating a DMZ to WAN Policy with Service and SMTPAnti Spam ...
Страница 497: ...496 Figure 13 35 Policy Created ...
Страница 506: ...505 Figure 13 45 Naming the Folder as Spam Mail ...
Страница 508: ...507 Figure 13 47 Selecting the Spam Mail Folder ...
Страница 510: ...509 Figure 13 49 Compacting the Spam Mail Folder ...
Страница 512: ...511 Figure 13 51 Copying the Pathname of the Spam Mail Folder ...
Страница 516: ...515 Figure 13 55 Creating a New Folder Figure 13 56 Naming the Folder as Ham Mail ...
Страница 518: ...517 Figure 13 58 Selecting the Ham Mail Folder ...
Страница 520: ...519 Figure 13 60 Compacting the Ham Mail Folder ...
Страница 522: ...521 Figure 13 62 Copying the Pathname of the Ham Mail Folder ...
Страница 525: ...524 Figure 13 65 All Normal Emails Have Been Deleted ...
Страница 529: ...528 Figure 13 68 Forwarding the Selected Spam Emails as Attachment ...
Страница 531: ...530 Figure 13 70 Forwarding the Selected Normal Emails as Attachment ...
Страница 533: ...532 ...
Страница 541: ...540 Figure 14 4 Creating an Outgoing Policy with Service and POP3 Anti Virus Figure 14 5 Policy Created ...
Страница 543: ...542 Figure 14 7 Policy Created ...
Страница 545: ...544 Figure 14 8 Creating a DMZ to WAN Policy with Service and POP3 Anti Virus ...
Страница 546: ...545 Figure 14 9 Policy Created ...
Страница 547: ...546 Step 8 Go to Mail Security Anti Virus Settings and then set as below Figure 14 10 Figure 14 10 Anti Virus Settings ...
Страница 552: ...551 Figure 14 16 Policy Completed ...
Страница 554: ...553 Figure 14 17 Creating an Outgoing Policy with Service and SMTPAnti Virus ...
Страница 555: ...554 Figure 14 18 Settings Completed ...
Страница 560: ...559 Figure 15 2 Periodical Report Sent as an Attachment ...
Страница 564: ...563 Figure 15 26 Navigating to Tools Mbox2eml on the Menu Bar Figure 15 27 Locating the mbx File to be Converted ...
Страница 565: ...564 Figure 15 28 Converting the mbx File into an eml File Figure 15 29 File Conversion Completed ...
Страница 566: ...565 Figure 15 30 Clicking and Dragging the eml File into Outlook Express to Open It ...
Страница 568: ...567 15 2 Logs Step 1 Under Mail Security Mail Reports Logs it shows how emails are processed ...
Страница 570: ...569 Web Filter ...
Страница 582: ...581 Figure 16 8 Group Settings for URL Blocking ...
Страница 583: ...582 Figure 16 9 The Completed Group Settings ...
Страница 586: ...585 Figure 16 13 The Completed Category Settings ...
Страница 588: ...587 Figure 16 16 Adding a New Extension Figure 16 17 Typing a New Extension Figure 16 18 File Extension Added ...
Страница 592: ...591 Figure 16 24 Configuring the URL Group ...
Страница 593: ...592 Figure 16 25 Setting Completed ...
Страница 597: ...596 Figure 17 2 A Daily Report Sent through an Email Message ...
Страница 602: ...601 ...
Страница 603: ...602 Figure 17 15 Statistics Report ...
Страница 605: ...604 IDP ...
Страница 610: ...609 Note 1 The IDP log is generated upon the Log setting under IDP Signatures Anomaly Pre defined Custom ...
Страница 614: ...613 Figure 19 2 Pre Defined Settings ...
Страница 622: ...621 Figure 19 8 Applying the IDP to the Policy ...
Страница 623: ...622 Figure 19 9 Policy Created ...
Страница 626: ...625 Figure 20 2 Periodic Report Received ...
Страница 630: ...629 Web VPN SSL VPN ...
Страница 636: ...635 Figure 21 4 User Group Entries ...
Страница 638: ...637 Figure 21 6 Web VPN SSL VPN Setting Completed ...
Страница 639: ...638 Figure 21 7 Web VPN SSL VPN Authentication Settings Figure 21 8 Web VPN SSL VPN Authentication Completed ...
Страница 642: ...641 Figure 21 12 Warning Security Window ...
Страница 643: ...642 Figure 21 13 Warning Security Window Figure 21 14 The Authentication Window Figure 21 15 Web VPN SSL VPN Connection ...
Страница 644: ...643 Figure 21 16 Web VPN SSL VPN Connection Established ...
Страница 649: ...648 Figure 21 22 Installing Java Runtime Environment Plug in ...
Страница 650: ...649 Policy ...
Страница 654: ...653 VPN Trunk This is where you apply the policy to regulate the session packets of IPSec or PPTP VPN ...
Страница 661: ...660 Figure 22 4 Traffic Shown in Log Screen ...
Страница 663: ...662 ...
Страница 664: ...663 Figure 22 5 Statistics Screen ...
Страница 666: ...665 Figure 22 9 MIME Script Settings Figure 22 10 Group Settings ...
Страница 673: ...672 Figure 22 20 Applying the Schedule and Authentication to the Policy Figure 22 21 Policy Completed ...
Страница 678: ...677 Figure 22 28 A WAN to DMZ Policy Created ...
Страница 683: ...682 Anomaly Flow IP ...
Страница 689: ...688 Advance ...
Страница 697: ...696 Note 1 The DNS must point to the fixed IPs ...
Страница 703: ...702 Figure 24 3 The First Inbound Balance Configuration ...
Страница 713: ...712 Figure 24 19 Configuring the Second Policy Settings Figure 24 20 Policy Completed ...
Страница 715: ...714 cycle restarted The 5th user accesses the server via 211 22 22 22 The 6th user accesses the server via 211 22 22 22 ...
Страница 718: ...717 Figure 24 26 Completed CNAME Alias Settings ...
Страница 721: ...720 Figure 24 30 Configuring the Second Policy Settings Figure 24 31 Adding the Second Policy ...
Страница 726: ...725 Figure 24 37 MX Mail eXchanger Settings Completed ...
Страница 728: ...727 Figure 24 40 The Third Setting of Server Figure 24 41 The Fourth Setting of Server ...
Страница 730: ...729 Figure 24 43 The Second Policy Settings Figure 24 44 The Third Policy Settings ...
Страница 731: ...730 Figure 24 45 The Fourth Policy Settings Figure 24 46 Policy Completed ...
Страница 748: ...747 Figure 26 4 Core Switch Settings Completed ...
Страница 751: ...750 Monitoring ...
Страница 754: ...753 Figure 27 1 Searching for a Specific Log ...
Страница 755: ...754 Figure 27 2 Downloading the Search Results ...
Страница 758: ...757 Figure 27 4 Searching for a Specific Log ...
Страница 762: ...761 Figure 27 8Monitoring the Traffic Flow of Each IPAddress ...
Страница 765: ...764 Figure 27 11 Specific Details of a History Event ...
Страница 769: ...768 Figure 27 14 A Policy with HTTP WebMail and FTP ...
Страница 770: ...769 Figure 27 15 Policy Completed ...
Страница 775: ...774 Figure 27 20 A Policy with Limitation of Concurrent Sessions ...
Страница 778: ...777 Figure 27 22 A Policy with Limitation of Quota per Source IP ...
Страница 781: ...780 Step 3 Go to Monitor Log Settings and then set as below Figure 27 27 Figure 27 27 Monitoring Settings ...
Страница 786: ...785 Figure 28 2 Searching for the Specific Log ...
Страница 787: ...786 Figure 28 3 Downloading the Accounting Reports ...
Страница 788: ...787 Figure 28 4 Deleting the Accounting Reprots ...
Страница 791: ...790 Figure 28 6 Today Top N ...
Страница 793: ...792 Figure 28 7 Today Top N Report according to the Time Interval ...
Страница 795: ...794 Figure 28 9 The Source IP and Service ...
Страница 801: ...800 Step 2 Statistic charts Figure 29 2 Vertical axis indicates network stream Horizontal axis indicates time ...
Страница 802: ...801 ...
Страница 805: ...804 Step 2 Statistics charts Figure 29 4 Vertical axis indicates network traffic Horizontal axis indicates time ...
Страница 806: ...805 ...
Страница 811: ...810 Figure 30 3 Ping Results for a VPN Connection ...
Страница 813: ...812 Figure 30 5 Traceroute Results ...
Страница 821: ...820 Figure 32 3 System Information ...
Страница 824: ...823 Figure 32 6 Downloading the Anti ARP Virus Software Figure 32 7 The Result of Executng the Anti ARP Virus Software ...
Страница 825: ...824 Figure 32 8 The Anti ARP Virus Software will Automatically Run when the System Startups ...






























