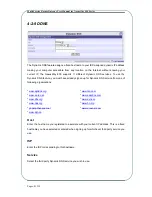
Multi Service Border Gateway User Manual for NexusWay 800 Series
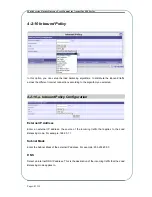
Exchange Mode
s available, which are Main Mode and Aggressive Mode. IKE
thentication phase includes verification of the identities of the
local and remote systems via pre-shared secrets or certificates, while the Key Exchange
nge is
e,
the Authentication phase will generate session keys if a secure channel is required for the Key
Exchange phase. Due to additional key generation steps, Main Mode is about three times
slower than Aggressive Mode, however it has higher security.
Local Identity/Remote Identity
Enter your Fully Qualified Domain Name box if you select
Local User_FQDN
or
Local FQDN
.
For using X509 Certificates for Authentication, select
Remote User_asn1dn
for your Local
and Remote Identities.
Encryption Algorithm
elect either DES (Data Encryption Standard) using 56 Bit Keys or 3DES (Triple DES) which
uthentication Algorithm
choice.
n Method
Key button and enter the key. To use RSA
ivest-Shamir-Adleman), a public-key algorithm for asymmetric Encryption, copy and paste
the signed public key of the desired endpoint as provided by a Certification Authority. For more
information about Certificate Authorities, please see
4-3-4 Certificate Authority
Diffie-Hellman (DH) Group
DH is an algorithm for developing a shared secret between endpoints by separately integrating
endpoints’ public key combination result with private key. Essentially, this is a method for
authenticating and negotiating keys; allowing two hosts to create and share a secret key. A 768
bit algorithm is used by "Group 1", a 1024 bit by "Group 2" and a 1536 bit by "Group 5," which
subsequently has the highest security, requires the longest time and the most resources.
There are two exchange mode
consists of two phases. The Au
phase involves the negotiation of security parameters. If the Authentication phase excha
in Aggressive Mode, the Key Exchange phase will not be encrypted. When set in Main Mod
S
uses 168 bit keys.
A
You can select MD5 (returns a 32 byte hash) or SHA-1 (returns a 160 byte hash). SHA-1 is
more secure but much slower than MD5 and requires more system resources. For general
application, MD5 is secure enough and much more suitable
Authenticatio
To use a Pre-shared Key, select Pre-shared
(R
Pages: 90/119