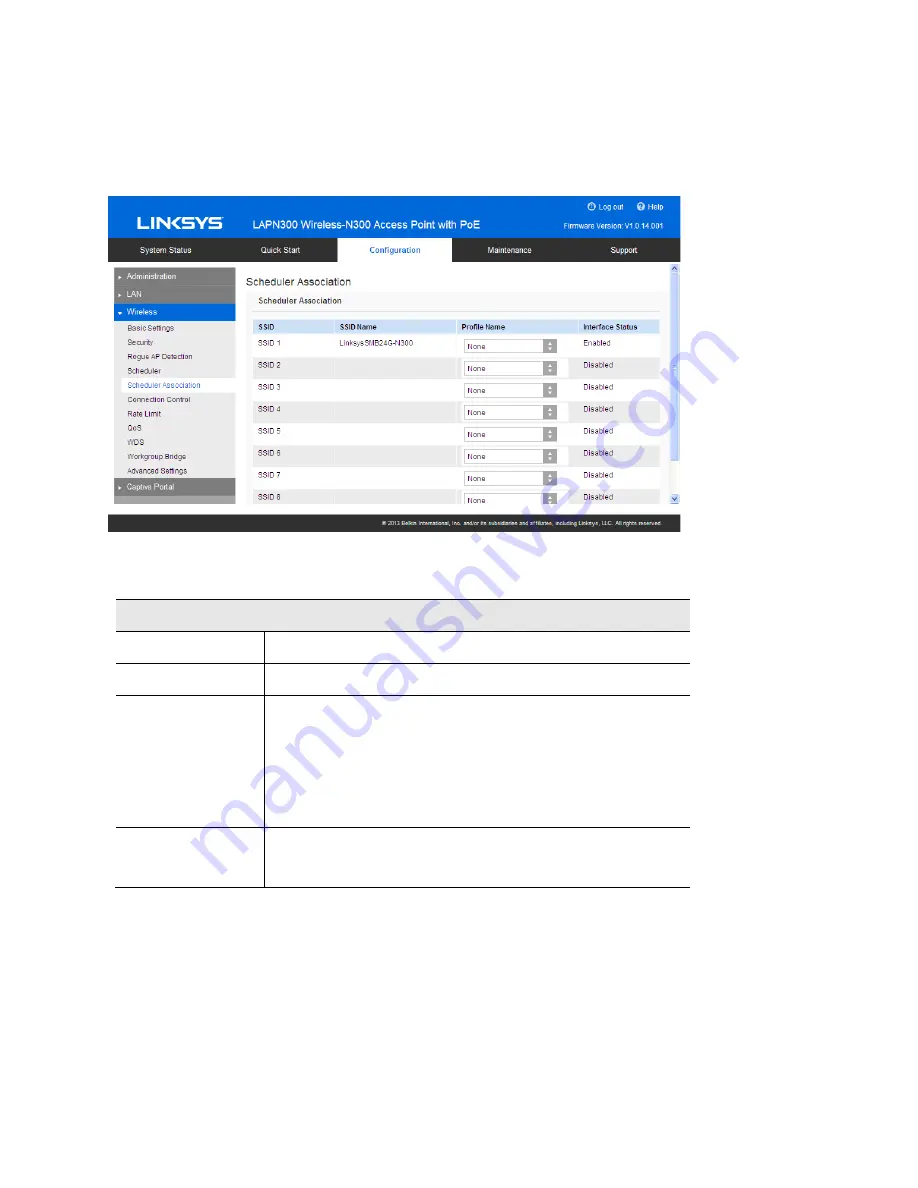
Scheduler Association
Associate defined scheduler profiles with SSIDs.
Figure 26: Scheduler Association Screen
Scheduler Association Screen
Scheduler Association
SSID
The index of SSID.
SSID Name
The name of the SSID.
Profile Name
Choose the profile that is associated with the SSID.
If the profile associated with the SSID is deleted, then the
association will be removed.
If "None" is selected, it means no scheduler profile is
associated.
Interface Status
The Status of the SSID. It can be Enabled or Disabled.
Scheduler only works when the SSID is enabled.
40
Содержание LAPN300
Страница 1: ...User Guide LAPN300 Wireless N300 Access Point with POE Model LAPN300 1 ...
Страница 14: ...Figure 8 Setup Wizard Finish 14 ...
Страница 97: ...6 Select the Group Policy tab choose Default Domain Policy then click Edit Figure 62 Group Policy Tab 97 ...
Страница 104: ...4 On the first screen below select Request a certificate click Next Figure 70 Wireless CA Screen 104 ...
Страница 105: ...5 Select User certificate request and select User Certificate click Next Figure 71 Request Type Screen 105 ...
Страница 106: ...6 Click Submit Figure 72 Identifying Information Screen 106 ...
















































