97
# Create VLAN 10.
[Router] vlan 10
[Router-vlan10] quit
# Set VLAN 10 as the 802.1X guest VLAN for port GigabitEthernet 1/0/2.
[Router] dot1x guest-vlan 10 interface gigabitethernet 1/0/2
Verifying the configuration
Use
display dot1x interface gigabitethernet 1/0/2
to verify the 802.1X guest VLAN configuration on
GigabitEthernet 1/0/2. If no user passes authentication on the port within a specified period of time,
use
display vlan 10
to verify whether GigabitEthernet 1/0/2 is assigned to VLAN 10.
After a user passes authentication, use
display interface gigabitethernet 1/0/2
to verify that port
GigabitEthernet 1/0/2 has been added to VLAN 5.
802.1X with ACL assignment configuration example
Network requirements
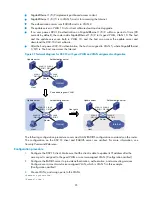
As shown in
, the host 192.168.1.10 connects to port GigabitEthernet 1/0/1 of the network
access device (named Router).
Perform 802.1X authentication on the port. Use the RADIUS server at 10.1.1.1 as the authentication and
authorization server and the RADIUS server at 10.1.1.2 as the accounting server. Assign an ACL to
GigabitEthernet 1/0/1 to deny 802.1X users to access the FTP server.
Figure 38
Network diagram for ACL assignment
Internet
Router
Host
RADIUS server cluster
192.168.1.10
GE1/0/2
Vlan-int2
192.168.1.1/24
FTP server
10.0.0.1
10.1.1.1/10.1.1.2
GE1/0/2
GE1/0/3
The following configuration procedure provides the major AAA and RADIUS configuration on the access
device. The configuration procedures on the 802.1X client and RADIUS server are beyond the scope of
this configuration example. For more information, see
Security Command Reference
.
Configuration procedure
1.
Configure the 802.1X client. Make sure that the client is able to update its IP address after the
access port is assigned to the 802.1X guest VLAN or a server-assigned VLAN. (Omitted)
2.
Configure the RADIUS servers, user accounts, and authorization ACL, which is ACL 3000 in this
example. (Omitted)
3.
Configure the access device.