449
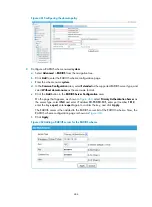
Recommended configuration procedure for manual request
Step Remarks
1.
Required.
Create a PKI entity and configure the identity information.
A certificate is the binding of a public key and the identity information of an
entity, where the distinguished name (DN) shows the identity information of
the entity. A CA identifies a certificate applicant uniquely by an entity DN.
The DN settings of an entity must be compliant to the CA certificate issue
policy. Otherwise, the certificate request might be rejected. You must know
the policy to determine which entity parameters are mandatory or optional.
2.
Required.
Create a PKI domain, setting the certificate request mode to
Manual
.
Before requesting a PKI certificate, an entity needs to be configured with
some enrollment information, which is called a PKI domain.
A PKI domain is intended only for convenience of reference by other
applications like IKE and SSL, and has only local significance.
3.
Required.
Generate a local RSA key pair.
By default, no local RSA key pair exists.
Generating an RSA key pair is an important step in certificate request. The
key pair includes a public key and a private key. The private key is kept by
the user, and the public key is transferred to the CA along with some other
information.
IMPORTANT:
If a local certificate already exists, you must remove the certificate before
generating a new key pair, so as to keep the consistency between the key pair
and the local certificate.
4.
Retrieving the CA
certificate
Required.
Certificate retrieval serves the following purposes:
•
Locally store the certificates associated with the local security domain for
improved query efficiency and reduced query count,
•
Prepare for certificate verification.
IMPORTANT:
If a local CA certificate already exists, you cannot perform the CA certificate
retrieval operation. This restriction avoids possible mismatch between
certificates and registration information resulting from relevant changes. To
retrieve the CA certificate, you must remove the CA certificate and local
certificate first.
Содержание MSR SERIES
Страница 17: ...xv Documents 835 Websites 835 Conventions 836 Index 838 ...
Страница 20: ...3 Figure 3 Initial page of the Web interface ...
Страница 42: ...25 Figure 13 Firefox Web browser setting ...
Страница 59: ...42 Figure 27 Checking the basic service configuration ...
Страница 73: ...56 Figure 35 Sample interface statistics ...
Страница 156: ...139 Figure 139 Rebooting the 3G modem ...
Страница 168: ...151 Figure 152 Configuring Web server 2 ...
Страница 174: ...157 Figure 158 Configure the URL filtering function ...
Страница 187: ...170 Upon detecting the Land or Smurf attack on Ethernet 0 2 Router outputs an alarm log and drops the attack packet ...
Страница 242: ...225 Figure 233 Enabling the DHCP client on interface Ethernet 0 1 ...
Страница 247: ...230 Figure 236 The page for configuring an advanced IPv4 ACL ...
Страница 255: ...238 Figure 241 Advanced limit setting ...
Страница 298: ...281 e Click Apply 2 Configure Router B in the same way Router A is configured ...
Страница 354: ...337 Figure 339 Configuring a login control rule so Host B cannot access Router through the Web ...
Страница 400: ...383 Figure 387 Verifying the configuration ...
Страница 405: ...388 ...
Страница 523: ...506 Figure 530 Ping configuration page ...
Страница 538: ...521 a Click Device A on the topology diagram b Click Ethernet 0 2 on the panel diagram c Click Port Guard ...
Страница 744: ...727 Verifying the configuration In the case that the IP network is unavailable calls can be made over PSTN ...
Страница 775: ...758 Figure 785 Configuring a jump node ...
Страница 791: ...774 Figure 801 Configuring a jump node ...