455
Item Description
Polling Count
Set the polling interval and attempt limit for querying the certificate request status.
After an entity makes a certificate request, the CA might need a long period of time if it
verifies the certificate request in manual mode. During this period, the applicant needs to
query the status of the request periodically to get the certificate as soon as possible after
the certificate is signed.
Polling Interval
Enable CRL
Checking
Select this box to specify that CRL checking is required during certificate verification.
CRL Update Period
Enter the CRL update period, that is, the interval at which the PKI entity downloads the
latest CRLs.
This item is available after you click the
Enable CRL Checking
box.
By default, the CRL update period depends on the next update field in the CRL file.
IMPORTANT:
The manually configured CRL update period takes precedent over that specified in the CRL
file.
CRL URL
Enter the URL of the CRL distribution point. The URL can be an IP address or a domain
name.
This item is available after you click the
Enable CRL Checking
box.
When the URL of the CRL distribution point is not set, you should acquire the CA
certificate and a local certificate, and then acquire a CRL through SCEP.
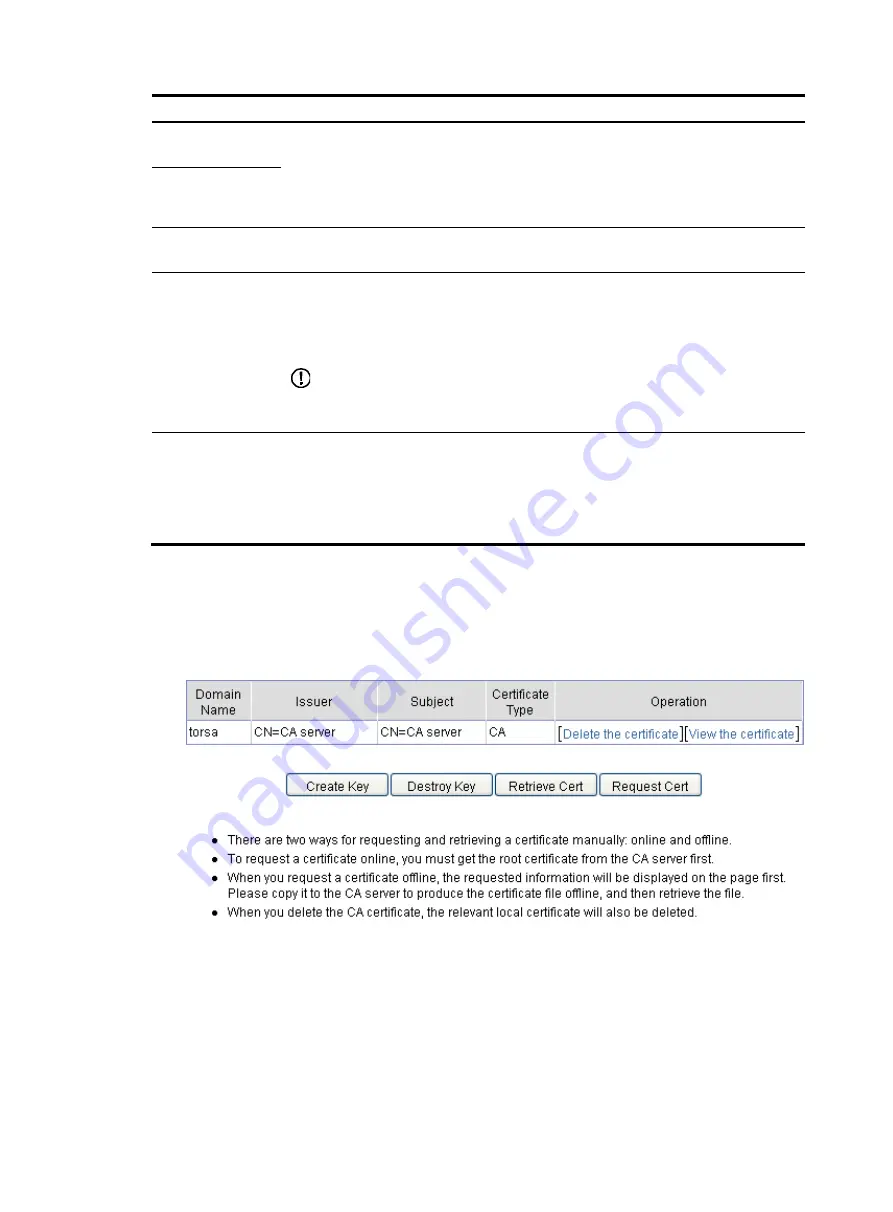
Generating an RSA key pair
1.
From the navigation tree, select
Certificate Management
>
Certificate
.
Figure 473
PKI certificates
2.
Click
Create Key
.
Содержание MSR SERIES
Страница 17: ...xv Documents 835 Websites 835 Conventions 836 Index 838 ...
Страница 20: ...3 Figure 3 Initial page of the Web interface ...
Страница 42: ...25 Figure 13 Firefox Web browser setting ...
Страница 59: ...42 Figure 27 Checking the basic service configuration ...
Страница 73: ...56 Figure 35 Sample interface statistics ...
Страница 156: ...139 Figure 139 Rebooting the 3G modem ...
Страница 168: ...151 Figure 152 Configuring Web server 2 ...
Страница 174: ...157 Figure 158 Configure the URL filtering function ...
Страница 187: ...170 Upon detecting the Land or Smurf attack on Ethernet 0 2 Router outputs an alarm log and drops the attack packet ...
Страница 242: ...225 Figure 233 Enabling the DHCP client on interface Ethernet 0 1 ...
Страница 247: ...230 Figure 236 The page for configuring an advanced IPv4 ACL ...
Страница 255: ...238 Figure 241 Advanced limit setting ...
Страница 298: ...281 e Click Apply 2 Configure Router B in the same way Router A is configured ...
Страница 354: ...337 Figure 339 Configuring a login control rule so Host B cannot access Router through the Web ...
Страница 400: ...383 Figure 387 Verifying the configuration ...
Страница 405: ...388 ...
Страница 523: ...506 Figure 530 Ping configuration page ...
Страница 538: ...521 a Click Device A on the topology diagram b Click Ethernet 0 2 on the panel diagram c Click Port Guard ...
Страница 744: ...727 Verifying the configuration In the case that the IP network is unavailable calls can be made over PSTN ...
Страница 775: ...758 Figure 785 Configuring a jump node ...
Страница 791: ...774 Figure 801 Configuring a jump node ...