69
# Type the user name, password, verify code, select
English
, and click
Login
. The homepage appears.
After login, you can configure device settings through the web interface.
HTTPS login example
Network requirements
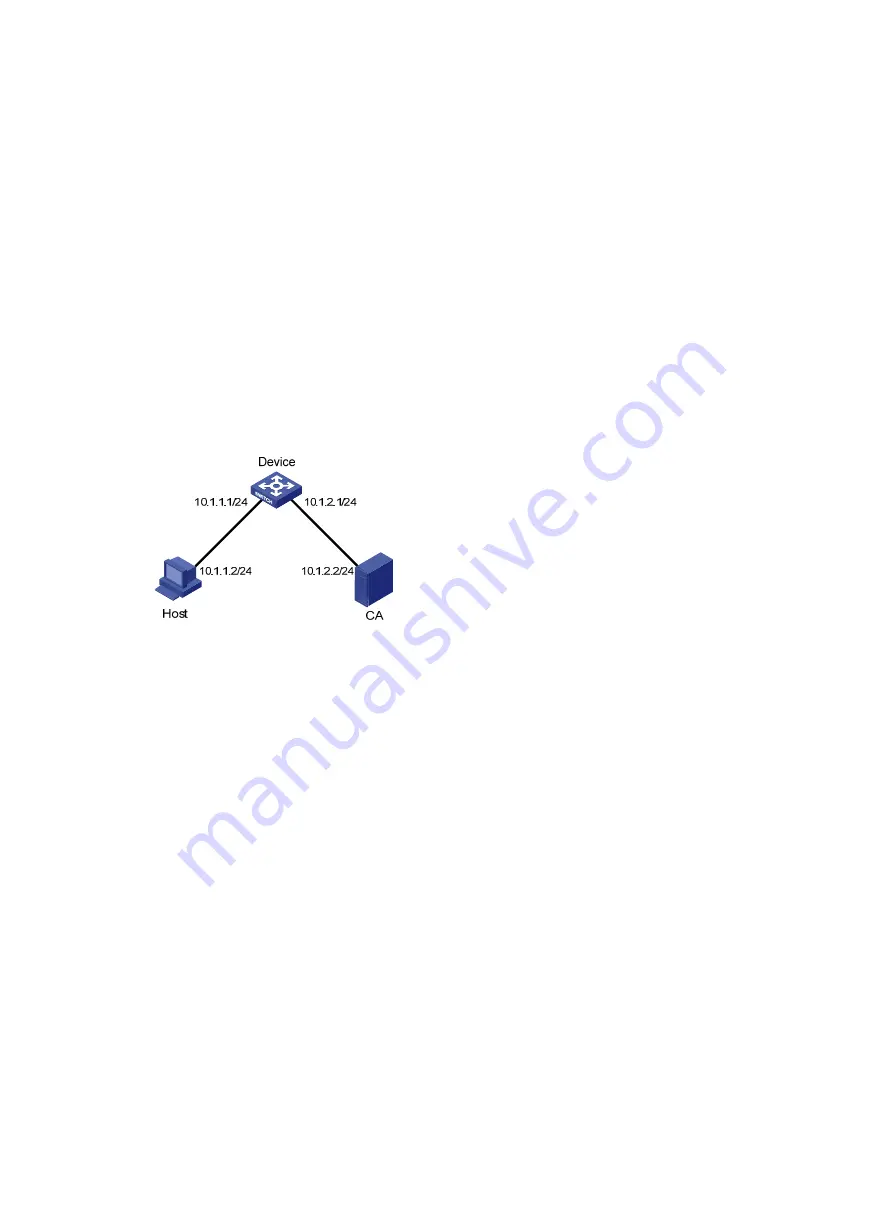
As shown in
, to prevent unauthorized users from accessing the Device, configure HTTPS login
as follows:
•
Configure the Device as the HTTPS server, and request a certificate for it.
•
The Host acts as the HTTPS client. Request a certificate for it.
In this example, Windows Server acts as the CA. Install Simple Certificate Enrollment Protocol (SCEP)
add-on on the CA. The name of the CA that issues certificates to the Device and Host is new-ca.
Before performing the following configuration, make sure that the Device, Host, and CA can reach each
other.
Figure 21
Network diagram for configuring HTTPS login
Configuration procedure
1.
Configure the device that acts as the HTTPS server
# Configure a PKI entity, configure the common name of the entity as
http-server1
, and the FQDN of the
entity as
ssl.security.com
.
<Device> system-view
[Device] pki entity en
[Device-pki-entity-en] common-name http-server1
[Device-pki-entity-en] fqdn ssl.security.com
[Device-pki-entity-en] quit
# Create a PKI domain, specify the trusted CA as
new-ca
, the URL of the server for certificate request as
http://10.1.2.2/certsrv/mscep/mscep.dll
, authority for certificate request as
RA
, and the entity for
certificate request as
en
.
[Device] pki domain 1
[Device-pki-domain-1] ca identifier new-ca
[Device-pki-domain-1] certificate request url http://10.1.2.2/certsrv/mscep/mscep.dll
[Device-pki-domain-1] certificate request from ra
[Device-pki-domain-1] certificate request entity en
# Specify the RSA key pair with the purpose general, the name hostkey.
[Device-pki-domain-1] public-key rsa general name hostkey
[Device-pki-domain-1] quit
















































