Incr3
<----
Incr1
<----
Full
8
Incr3
<----
Incr2
<----
Incr1
<----
Full
9
Incr3
<----
Incr2
<----
<----
<----
Full
10
Incr3
<----
<----
<----
<----
<----
Full
11
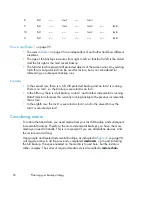
How to read Table 7
on page 95
•
The rows in
Table 7
on page 95 are independent of each other and show different
situations.
•
The age of the backups increases from right to left, so that the far left is the oldest
and the far right is the most recent backup.
•
The full and IncrX represent still protected objects of the same owner. Any existing
IncrX that is not protected can be used for restore, but is not considered for
referencing on subsequent backup runs.
Examples
•
In the second row, there is a full, still protected backup and an Incr2 is running.
There is no Incr1, so the backup is executed as an Incr1.
•
In the fifth row, there is a full backup, an Incr1 and another incremental is running.
Data Protector references the currently running backup to the previous incremental,
that is Incr1.
•
In the eighth row, the Incr3 is executed as Incr2, and in the eleventh row, the
Incr3 is executed as Incr1.
Considering restore
To restore the latest data, you need media from your last full backup and subsequent
incremental backups. Therefore, the more incremental backups you have, the more
media you need to handle. This is inconvenient if you use standalone devices, and
the restore can last long.
Using simple and leveled incremental backups, as indicated in
Figure 25
on page 98,
will require access to all five previously completed
media sets
, up to and including
the full backup. The space needed on the media is lowest here, but the restore is
rather complex. The series of required media sets is also called a
restore chain
.
Planning your backup strategy
96
Содержание B6960-96035
Страница 17: ...Overview of backup and automated media copy sessions 340 105 Concepts guide 17 ...
Страница 20: ...20 ...
Страница 22: ...Publication history 22 ...
Страница 132: ...Planning your backup strategy 132 ...
Страница 182: ...Media management and devices 182 ...
Страница 186: ...Users and user groups 186 ...
Страница 204: ...The Data Protector internal database 204 ...
Страница 218: ...Figure 62 Direct SIP integration example Service management 218 ...
Страница 242: ...Integration with database applications 242 ...
Страница 264: ...Synthetic backup 264 ...
Страница 274: ...Split mirror concepts 274 ...
Страница 288: ...Snapshot concepts 288 ...
Страница 344: ...Further information 344 ...
Страница 402: ...Glossary 402 ...