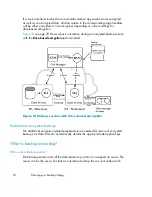
Data Protector security features
The following features allow and restrict access to Data Protector and the backed up
data. The items in this list are described in detail in the following sections.
•
Cells
•
Data Protector user accounts
•
Data Protector user groups
•
Data Protector user rights
•
Visibility and access to backed up data
Cells
Starting sessions
Data Protector security is based on cells. Backup and restore sessions can only be
started from the Cell Manager unless you have the Data Protector
Manager-of-Managers functionality. This ensures that users from other cells cannot
back up and restore data from systems in your local cell.
Access from a specific Cell Manager
Additionally, Data Protector allows you to explicitly configure from which Cell
Manager a client system can be accessed, that is, configuring a trusted peer.
Restrict pre- and post-execution
For security reasons, various levels of restrictions can be configured for pre-exec and
post-exec scripts. These optional scripts allow a client system to be prepared for the
backup by, for example, shutting down an application to obtain a consistent backup.
Data Protector users accounts
Anyone using any Data Protector functionality, administering Data Protector, or
restoring personal data, must have a Data Protector user account. This restricts
unauthorized access to Data Protector and backed up data.
Who defines user accounts?
An administrator creates this account specifying a user login name, systems from
which a user can log in, and the Data Protector user group membership that defines
the user rights.
Planning your backup strategy
74
Содержание B6960-96035
Страница 17: ...Overview of backup and automated media copy sessions 340 105 Concepts guide 17 ...
Страница 20: ...20 ...
Страница 22: ...Publication history 22 ...
Страница 132: ...Planning your backup strategy 132 ...
Страница 182: ...Media management and devices 182 ...
Страница 186: ...Users and user groups 186 ...
Страница 204: ...The Data Protector internal database 204 ...
Страница 218: ...Figure 62 Direct SIP integration example Service management 218 ...
Страница 242: ...Integration with database applications 242 ...
Страница 264: ...Synthetic backup 264 ...
Страница 274: ...Split mirror concepts 274 ...
Страница 288: ...Snapshot concepts 288 ...
Страница 344: ...Further information 344 ...
Страница 402: ...Glossary 402 ...