P a g e
|
21
UCM Security Manual
TLS
The UCM administrators may consider securing SIP packets sent across an untrusted network. Using TLS
could be a solution. It will authenticate servers and clients, and then encrypt SIP messages between the
authenticated parties.
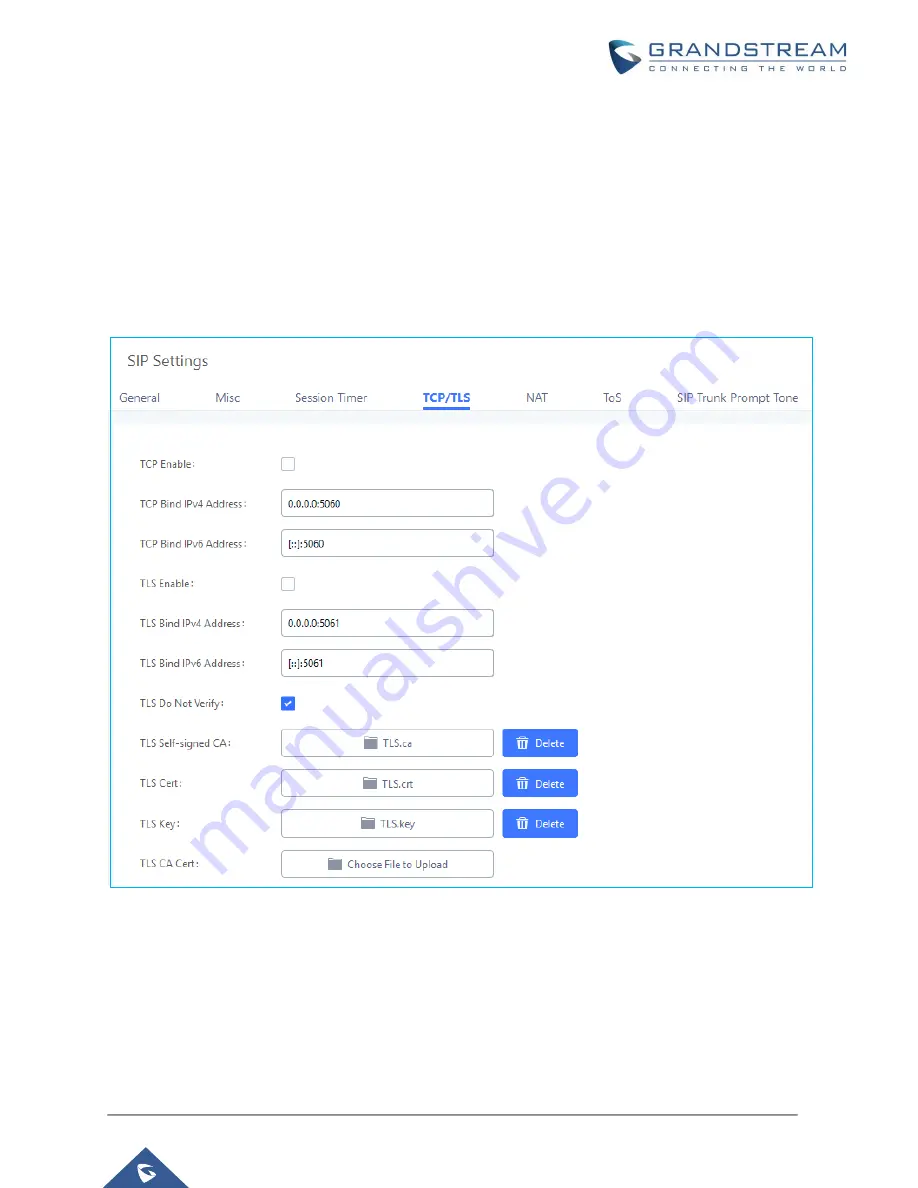
TLS can be configured under UCM web GUI
PBX Settings
SIP Settings
TCP/TLS page.
Figure 15: PBX Settings
SIP Settings
TCP/TLS
1.
Set “TLS Enable” as “Yes” to enable TLS on UCM.
2.
Configure “TLS Do Not Verify”, “TLS Self-Signed CA” and “TLS Cert” properly to achieve basic TLS
authentication and encryption.

























