2
– Integrating Google Cloud Platform with SafeNet Luna HSM
Google Cloud Platform Integration Guide
20
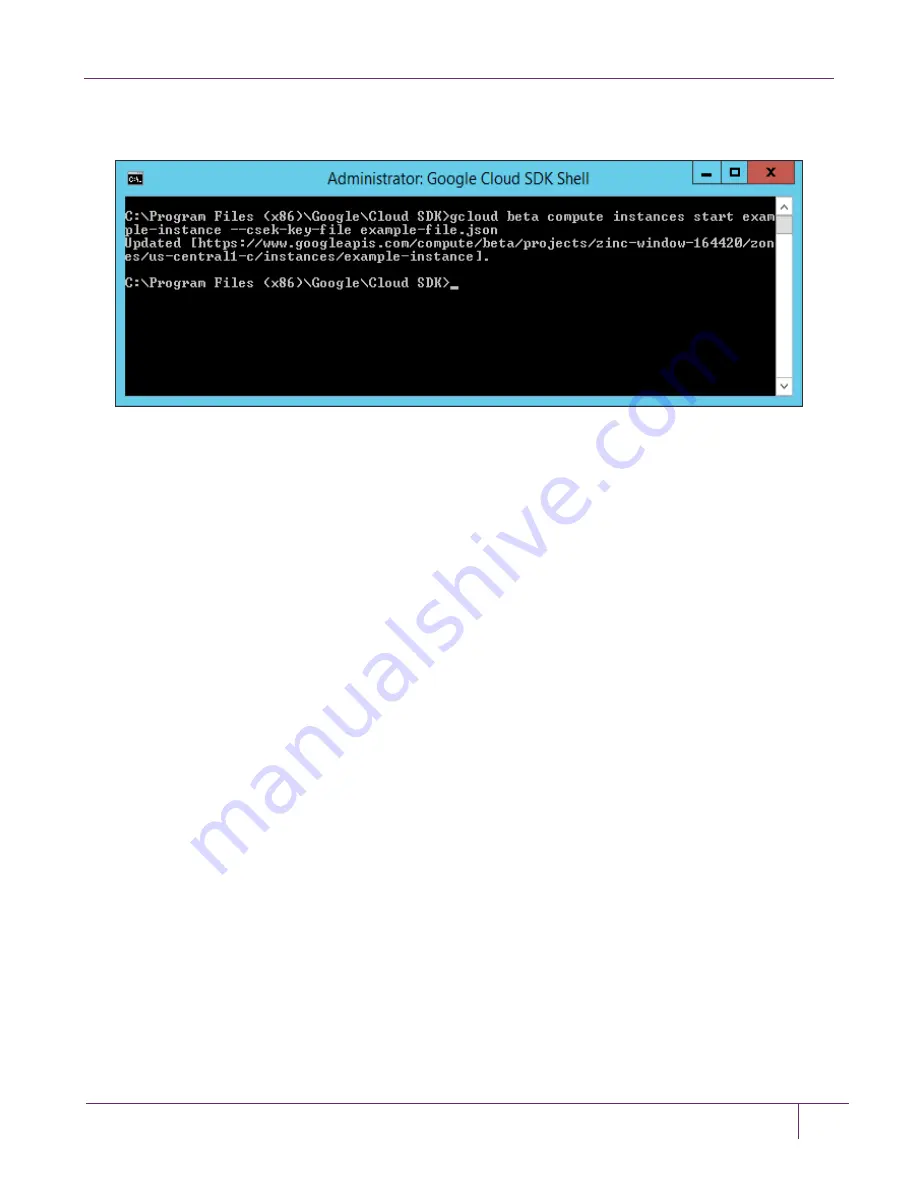
5. To start the VM instance run the following command on gcloud console.
# gcloud beta compute instances start example-instance --csek-key-file example-file.json
Stopping/deleting does not require the CSEK but other operations (read/write) like starting encrypted VM,
snapshot of the encrypted disk etc. require the CSEK used to encrypt the disk. For details regarding other
operations on encrypted disk refer to the google cloud documentation.
This completes the demonstration of generating the AES256 key on HSM and encrypting the disk using that key
on Google Cloud. Each time any read/write operation is performed on encrypted disk, it prompts for the
encryption key and you need to provide the base64 encoded wrapped key. Google keep the supplied CSEK till
operation completed, for example VM is restarted or snapshot of the encrypted disk, after that the CSEK purge
from memory. The key is secured on HSM and you can wrap and encode the key when required. So if you want
to delete the wrapped key form local system then you can delete it; however, there is no harm in keeping the
wrapped key as it can be only unwrapped by the Google Private Key.






































