SH-E514TR1 10 Gigabit Ethernet SmartPro Switch User Manual
65
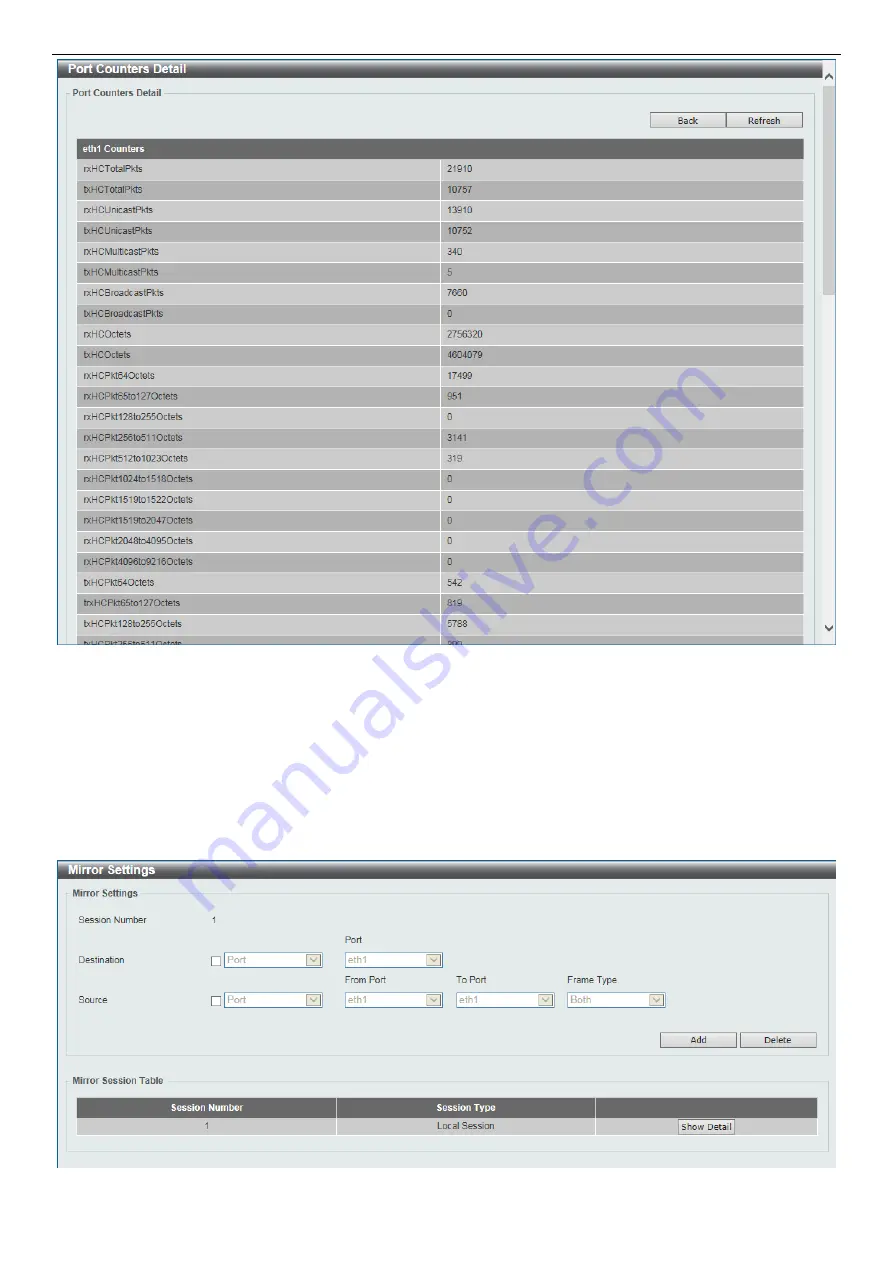
Figure 13-8 Port Counters Detail
Click
Back
to return to the previous window.
Click
Refresh
to refresh the display table.
Mirror Settings
This w
indow is used to view and configure the mirror feature’s settings. The Switch allows users to copy frames
transmitted and received on a port and redirect the copies to another port. Attach a monitoring device to the mirroring
port, such as a sniffer or an RMON probe, to view details about the packets passing through the first port. This is
useful for network monitoring and troubleshooting purposes.
Figure 13-9 Mirror Settings


































