24
component updates within the
Update mode
tab depends on
each individual workstation, since that is where these settings are
to be applied. Please be aware that there are differences between
workstations and servers – e.g. restarting the server automatically
after a program upgrade could cause serious damage.
4.4.1.2.2
Proxy server
To access the proxy server setup options for a given update profile:
Click
Update
in the Advanced Setup tree (F5) and then click the
Setup...
button to the right of
Advanced update setup.
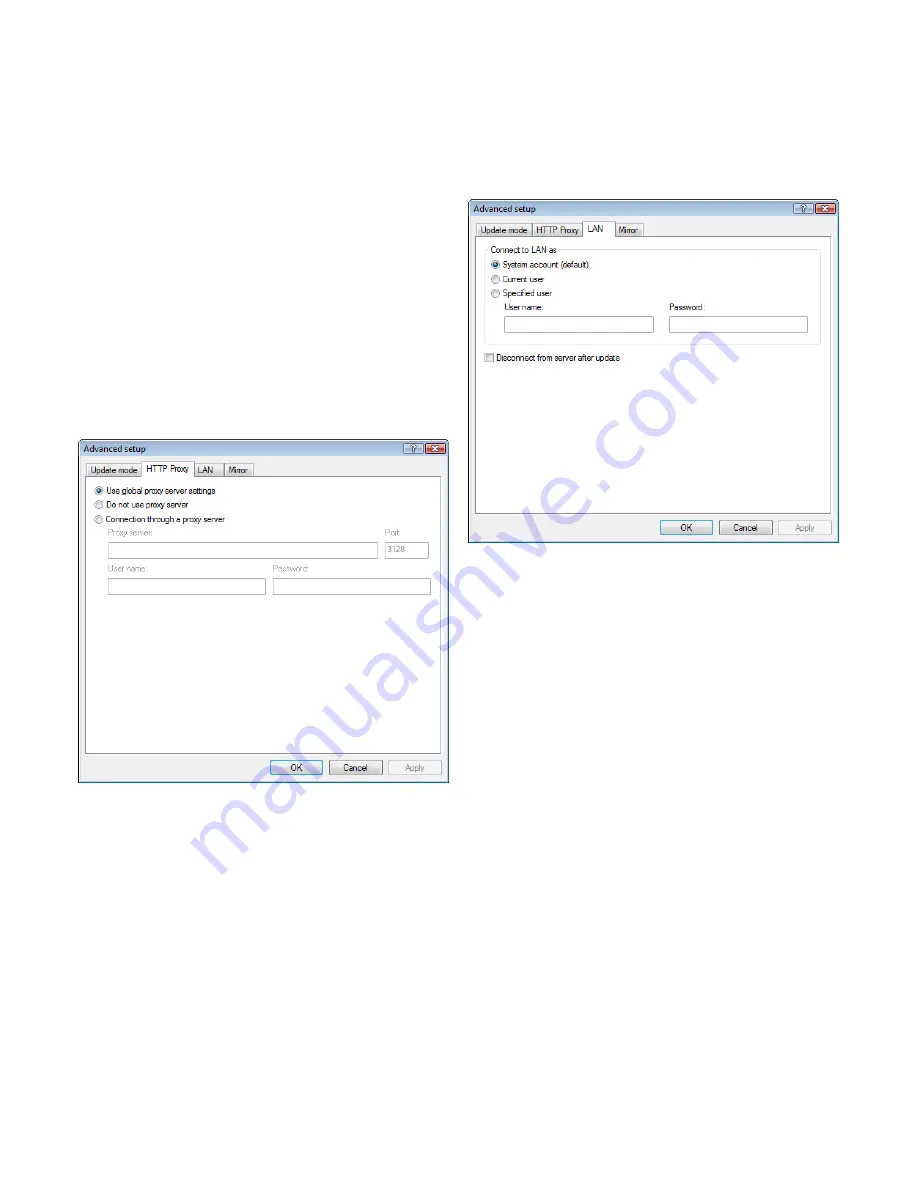
Click the
HTTP Proxy
tab and select one of the three following options:
▪
Use global proxy server settings
▪
Do not use proxy server
▪
Connection through a proxy server
(connection defined by the
connection properties)
Selecting the
Use global proxy server settings
option will use the
proxy server configuration options already specified within the
Miscellaneous > Proxy server
branch of the Advanced Setup tree.
Select the
Do not use proxy server
option to explicitly define that no
proxy server will be used for updating ESET Smart Security.
The
Connection through a proxy server
option should be chosen
if a proxy server is to be used for updating ESET Smart Security and
is different from the proxy server specified in the global settings
(
Miscellaneous > Proxy server
). If so, the settings should be specified
here:
Proxy server
address, communication
Port
, plus
User name
and
Password
for the proxy server if required.
This option should also be selected if the proxy server settings were
not set globally, but the ESET Smart Security will connect to a proxy
server for updates.
The default setting for the proxy server is
Use global proxy server
settings
.
4.4.1.2.3
Connecting to LAN
When updating from a local server with an NT‑based operating
system, authentication for each network connection is required by
default. In most cases, a local system account doesn‘t have sufficient
rights to access the Mirror folder (the Mirror folder contains copies of
update files). If this is the case, enter the user name and password in
the update setup section, or specify an existing account under which
the program will enter the update server (Mirror).
To configure such an account, click the
LAN
tab. The
Connect to
LAN as
section offers the options
System account (default)
,
Current
user
, and
Specified user
.
Select the
System account
option to use the system account for
authentication. Normally, no authentication process takes place if
there is no authentication data supplied in the main update setup
section.
To ensure that the program authorizes itself using a currently
logged‑in user account, select
Current user
. The drawback of this
solution is that the program is not able to connect to the update
server if no user is currently logged in.
Select
Specified user
if you want the program to use a specific user
account for authentication.
The default option for LAN connection is
System account
.
Warning:
When either
Current user
or
Specified user
is enabled, an error may
occur when changing the identity of the program to the desired user.
This is why we recommend inserting the LAN authentication data
in the main update setup section. In this update setup section, the
authentication data should be entered as follows: domain_name\user
(if it is a workgroup, enter workgroup_name\name) and the user’s
password. When updating from the HTTP version of the local server,
no authentication is required.
4.4.1.2.4
Creating update copies – Mirror
ESET Smart Security Business Edition allows the user to create copies
of update files which can be used to update other workstations
located in the network. Updating client workstations from a Mirror
optimizes network load balance and saves Internet connection
bandwidth.





























