14
4.1.4 An infiltration is detected
Infiltrations can reach the system from various entry
points: webpages, shared folders, email or removable
computer devices (USB, external disks, CDs, DVDs,
diskettes, etc.).
If your computer is showing signs of malware
infection, e.g., it is slower, often freezes, etc., we
recommend the following steps:
1. Open ESET Cybersecurity and click
Computer scan
.
2. Click
Smart scan
(for more information, see the
Smart scan
section).
3. After the scan has finished, review the log for the
number of scanned, infected and cleaned files.
If you only wish to scan a certain part of your disk,
click
Custom scan
and select targets to be scanned for
viruses.
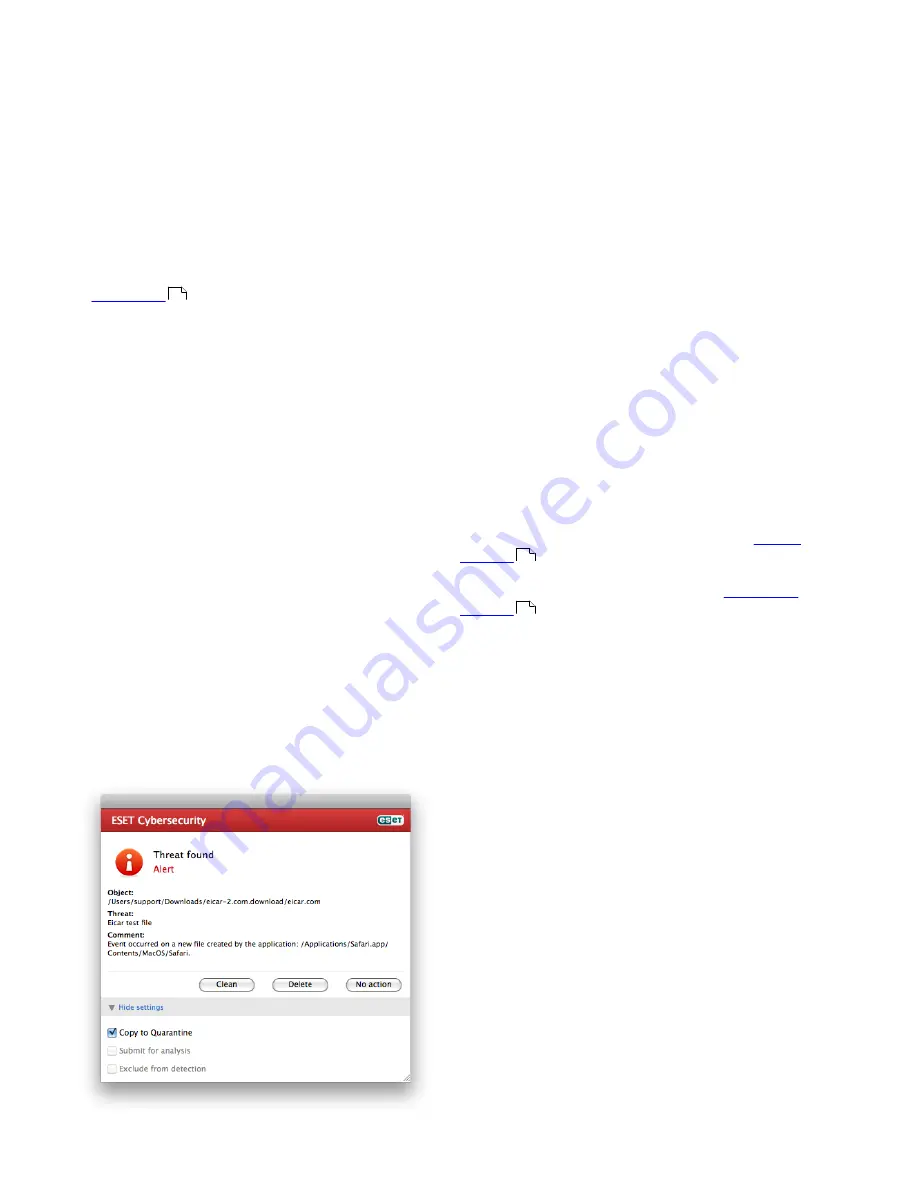
As a general example of how infiltrations are handled
in ESET Cybersecurity, suppose that an infiltration is
detected by the Real-time file system monitor, which
uses the default cleaning level. It will attempt to clean
or delete the file. If there is no predefined action to
take for the Real-time protection module, you will be
asked to select an option in an alert window. Usually,
the options
Clean
,
Delete
and
No action
are available.
Selecting
No action
is not recommended, since the
infected file(s) would be left untouched. An exception
to this is when you are sure that the file is harmless
and has been detected by mistake.
Cleaning and deleting – Apply cleaning if a file has been
attacked by a virus that has attached malicious code
to it. If this is the case, first attempt to clean the
infected file in order to restore it to its original state. If
the file consists exclusively of malicious code, it will be
deleted.
Deleting files in archives
– In the default cleaning
mode, the entire archive will be deleted only if it
contains infected files and no clean files. In other
words, archives are not deleted if they also contain
harmless clean files. However, use caution when
performing a
Strict cleaning
scan – with Strict
cleaning the archive will be deleted if it contains at
least one infected file, regardless of the status of other
files in the archive.
4.2 Updating the program
Regular updates of ESET Cybersecurity are necessary
to maintain the maximum level of security. The
Update module ensures that the program is always up
to date by updating the virus signature database.
By clicking
Update
from the main menu, you can find
the current update status, including the date and time
of the last successful update and if an update is
needed. To begin the update process manually, click
the
Update virus signature database
.
Under normal circumstances, when updates are
downloaded properly, the message
Virus signature
database is up to date
will appear in the Update
window. If the virus signature database cannot be
updated, we recommend that you check the
update
settings
- the most common reason for this error is
incorrectly entered authentication data (Username
and Password) or incorrectly configured
connection
settings
.
The Update window also contains the information
about the virus signature database version. This
numeric indicator is an active link to ESET’s website,
listing all signatures added during the given update.
NOTE:
Your username and password are provided by
ESET after purchasing ESET Cybersecurity.
4.2.1 Upgrading to a new build
For maximum protection, it is important to use the
latest build of ESET Cybersecurity. To check for a new
version, click
Update
from the main menu on the left.
If a new build is available, a message that says
A new
version of the product is available!
will be displayed at the
bottom of the window. Click
Learn more...
to display
a new window containing the version number of the
new build and the changelog.
11
15
21























