DRO-210i Web Configuration
DRO-210i User Manual Page 3-78
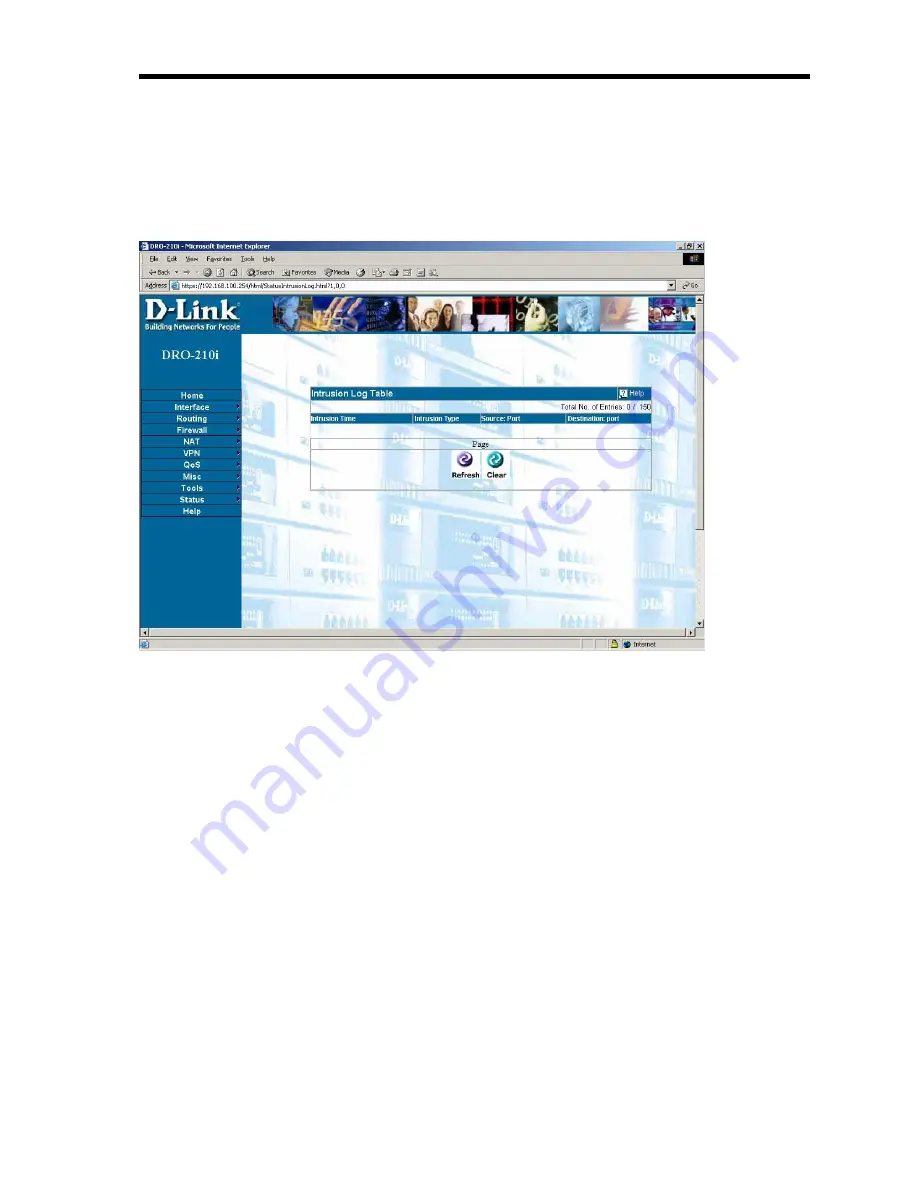
3.9.6.3 Status – Log Tables – Intrusion Log
Click on
Status > Log Tables > Intrusion Log
to get the web page as
shown
below:
Certain sessions between computers on your LAN and the WAN have the
potential to cause a disruption in the function of your computers and are
blocked by the Router's firewall. Some of these session types are pre-
defined by the factory and are commonly used intrusion methods. Events
blocked (attempts to connect to computers on your LAN, between
computers on your LAN, or between computers on your LAN and the
WAN) because they meet the criteria pre-defined at the factory as being a
commonly used intrusion method, are recorded here, in the
Intrusion
Detection Log
.
Intrusion Type
- A brief statement of the type of intrusion that was
attempted is displayed here. The Router firewall can detect following
attacks: SYN Flooding , TCP Hijacking, LAND Attack,
WinNuke/OOBNuke, Christmas Tree SYN / FIN (Jackal), SYN / FIN